Cofense not too long ago recognized and named a brand new malware referred to as Poco RAT, which is an easy Distant Entry Trojan that targets Spanish language victims. It was first noticed in early 2024, primarily specializing in corporations within the Mining sector and initially was delivered by way of embedded hyperlinks to 7zip archives containing executables that had been hosted on Google Drive. The campaigns are ongoing and proceed to exhibit the identical TTPs. The vast majority of the customized code within the malware seems to be centered on anti-analysis, speaking with its Command and Management heart (C2), and downloading and operating information with a restricted concentrate on monitoring or harvesting credentials.
First Seen and Categorized
Poco RAT was first recognized and assigned a malware household on 2024-02-07. The strings had been used to label the malware as “Poco RAT”. It had all of the hallmarks of the campaigns that will likely be described on this report.
Noticed Focused Sectors
Whereas Poco RAT first focused clients within the Mining sector, over time this has unfold to include 4 sectors in complete as of Q2 2024. A breakdown of the sectors focused over the course of the campaigns may be seen in Determine 1. It’s notable that whereas there are 4 complete focused sectors, Mining nonetheless makes up the vast majority of the targets on the time of this report. Regardless of the unfold of industries, you will need to be aware that one firm was essentially the most focused, being answerable for 67% of the whole quantity of those Poco RAT campaigns.

Determine 1: Sectors focused by e-mail quantity in Poco RAT campaigns.
E-mail Options
The emails campaigns have a number of constant options which made identification very simple.
- The emails had been finance themed, having each a topic and message physique indicating as such.
- The language of each the e-mail topic and message physique was Spanish.
- The emails both contained a hyperlink to a 7zip archive hosted on Google Drive or delivered a file with a hyperlink embedded contained in the file to obtain a 7zip archive hosted on Google Drive.
A pattern of what a lot of the emails appear like may be seen in Determine 2.

Determine 2: E-mail seen delivering Poco RAT by way of a Google Drive hyperlink embedded inside picture within the e-mail physique.
Supply Strategies
The file finally delivered by every of the emails is a 7zip archive containing an executable. The archive may very well be delivered in three other ways. The primary, and most typical, method is by way of a Google Drive URL that’s embedded immediately within the e-mail. As seen in Determine 3, this accounted for 53% of the emails. The second most typical method was by way of a hyperlink embedded in an HTML file which was noticed 40% of the time. The HTML file may very well be both connected or downloaded by way of one other embedded hyperlink which was additionally hosted on Google Drive. Lastly, an connected PDF may comprise a hyperlink to obtain the archive from Google Drive.
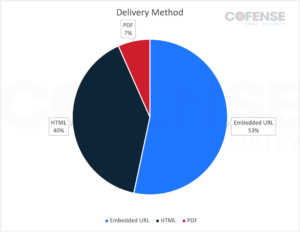
Determine 3: Supply methodology of 7zip archives by e-mail quantity in Poco RAT campaigns.
URL Embedded in E-mail Physique
Essentially the most generally seen methodology of supply was a Google Drive URL embedded within the e-mail physique which downloaded a 7zip archive containing an executable. An instance of an e-mail with this tactic may be seen in Determine 2. Menace actors usually use authentic file internet hosting providers reminiscent of Google Drive to bypass Safe E-mail Gateways (SEGs) and this tactic has been seen in use by many various risk actors and APT teams through the years.
Downloaded HTML
The second mostly seen methodology of delivering Poco RAT was HTML information with a 40% share. Particularly, emails would have a Google Drive hyperlink embedded in them which might result in downloading an HTML file. The HTML file, proven in Determine 4, would then present a hyperlink that may then obtain a 7zip archive containing the Poco RAT executable. This tactic would seemingly be simpler than merely offering a URL to immediately obtain the malware as any SEGs that may discover the embedded URL would solely obtain and verify the HTML file, which might look like authentic.

Determine 4: Contents of a downloaded HTML file with an embedded Google Drive hyperlink to obtain Poco RAT.
Hooked up PDF
The ultimate, and most uncommon, methodology of delivering Poco RAT was by way of an connected PDF file at solely 7% of all emails. An instance of one among these PDFs may be seen in Determine 5. The PDF file contained an embedded Google Drive hyperlink which might, as typical on this marketing campaign, obtain a 7zip archive containing the Poco RAT executable. Regardless of being the rarest type of supply, utilizing an connected PDF with an embedded hyperlink somewhat than a hyperlink embedded immediately in an e-mail is definitely essentially the most profitable methodology of bypassing a SEG based mostly on evaluation of comparable campaigns. It’s because SEGs usually take into account PDF information to be non-malicious and, if correctly managed, a PDF file can have embedded URLs hidden from scanning strategies.
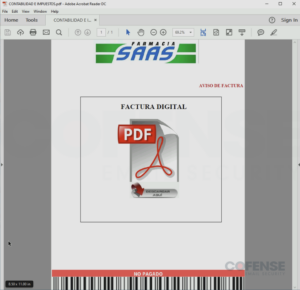
Determine 5: Hooked up PDF file with an embedded Google Drive hyperlink to obtain Poco RAT.
Malware Options
Detection Charges
The usage of in depth metadata is probably going in an try to bypass Anti-Virus (AV), nonetheless, with a mean detection charge of 38% for the executables, it’s unlikely to have succeeded. The detection charge for the archives is decrease however nonetheless substantial at a mean of 29% whereas not one of the supply mechanisms used had been detected by any AV after they had been first submitted to VirusTotal. Not solely did the executables face vital detection charges however their suspicious habits, reminiscent of checking for a debug surroundings, checking for consumer enter, and having lengthy sleeps was additionally detected in virtually each case.
POCO C++ Libraries
Poco RAT makes use of, and derives its title from, the POCO C++ libraries. These libraries are fairly standard cross-platform open-source libraries used for including community performance to desktop and cell apps. This makes malware utilizing them much less more likely to be detected than if the malware had been to make use of its personal customized code or a much less extensively used library.
Executable Specifics
Poco RAT is delivered as an executable with the .exe file extension. It’s written in Delphi, generally UPX packed, and has an uncommon quantity of Exif metadata included in every executable. The metadata usually features a random Firm Identify, Inner Identify, Unique File Identify, Product Identify, Authorized Copyrights and Emblems, and varied model numbers.
Habits
Poco RAT is constant in its habits. When the executable is run it establishes persistence, usually by way of a registry key. It then launches the authentic course of grpconv.exe, which has only a few alternatives to run legitimately on trendy Home windows OS. Poco RAT then injects into grpconv.exe and connects to its Command and Management (C2) location. This C2 is all the time hosted on 94[.]131[.]119[.]126 and is linked to at the very least one among 3 ports: 6541, 6542, or 6543. Except the contaminated laptop has a geo location in Latin America, the makes an attempt to speak will not be responded to by the C2. If the contaminated laptop seems to be coming from Latin America, then a really small dialog takes place over an prolonged time period. Other than with the ability to talk primary details about the surroundings, Poco RAT additionally seems to have the ability to obtain and execute information making it able to delivering different malware extra specialised for data stealing and even ransomware.

