Researchers have pulled again the curtain on an up to date model of an Apple macOS malware known as RustBucket that comes with improved capabilities to determine persistence and keep away from detection by safety software program.
“This variant of RustBucket, a malware household that targets macOS methods, provides persistence capabilities not beforehand noticed,” Elastic Safety Labs researchers mentioned in a report revealed this week, including it is “leveraging a dynamic community infrastructure methodology for command-and-control.”
RustBucket is the work of a North Korean menace actor often known as BlueNoroff, which is an element of a bigger intrusion set tracked beneath the identify Lazarus Group, an elite hacking unit supervised by the Reconnaissance Basic Bureau (RGB), the nation’s main intelligence company.
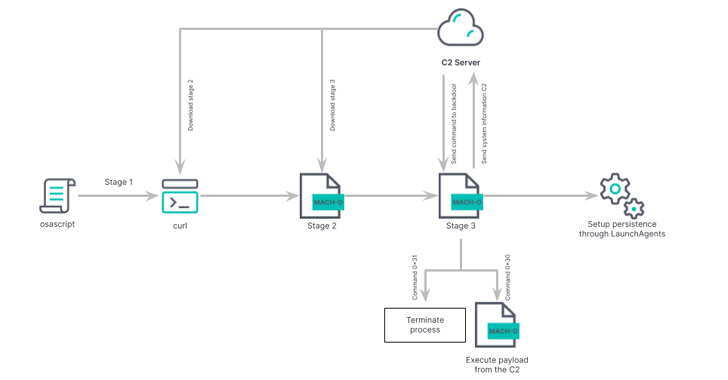
The malware got here to mild in April 2023, when Jamf Risk Labs described it as an AppleScript-based backdoor able to retrieving a second-stage payload from a distant server. Elastic is monitoring the exercise as REF9135.
The second-stage malware, compiled in Swift, is designed to obtain from the command-and-control (C2) server the principle malware, a Rust-based binary with options to assemble in depth data in addition to fetch and run extra Mach-O binaries or shell scripts on the compromised system.
It is the primary occasion of BlueNoroff malware particularly focusing on macOS customers, though a .NET model of RustBucket has since surfaced within the wild with the same set of options.
“This current Bluenoroff exercise illustrates how intrusion units flip to cross-platform language of their malware improvement efforts, additional increasing their capabilities extremely more likely to broaden their victimology,” French cybersecurity firm Sekoia mentioned in an evaluation of the RustBucket marketing campaign in late Could 2023.
The an infection chain consists of a macOS installer file that installs a backdoored, but practical, PDF reader. A major facet of the assaults is that the malicious exercise is triggered solely when a weaponized PDF file is launched utilizing the rogue PDF reader. Preliminary intrusion vector contains phishing emails, in addition to using bogus personas on social networks equivalent to LinkedIn.
🔐 Privileged Entry Administration: Study Find out how to Conquer Key Challenges
Uncover totally different approaches to beat Privileged Account Administration (PAM) challenges and stage up your privileged entry safety technique.
The noticed assaults are extremely focused and centered on finance-related establishments in Asia, Europe, and the U.S., suggesting that the exercise is geared in direction of illicit income technology to evade sanctions.
What makes the newly recognized model notable is its uncommon persistence mechanism and using dynamic DNS area (docsend.linkpc[.]internet) for command-and-control, alongside incorporating measures centered on remaining beneath the radar.
“Within the case of this up to date RustBucket pattern, it establishes its personal persistence by including a plist file on the path /Customers/<person>/Library/LaunchAgents/com.apple.systemupdate.plist, and it copies the malware’s binary to the next path /Customers/<person>/Library/Metadata/System Replace,” the researchers mentioned.