Present in Environments Protected By: Microsoft
By Tej Tulachan, Phishing Protection Middle (PDC)
In the course of the busy self-assessment season within the UK, risk actors benefit from the heightened on-line exercise to deceive unsuspecting people into revealing their delicate info on fraudulent HM Income & Customs (HMRC) self-assessment web sites. Phishing Protection Middle (PDC) has famous this wave of assaults throughout numerous sectors and regrettably, these phishing emails usually evade well-liked safe e-mail gateways (SEGs) that should present safety for customers.
The phishing emails start by pressuring customers to right away replace their self-assessment on-line profile. This can be a frequent tactic employed by risk actors to generate a misleading notion of urgency and legitimacy. Determine 1 reveals that the sender’s tackle seems to be from GOV[.]UK, however upon nearer examination, it turns into evident that it’s a spoofed tackle: [email protected][.]co[.]jp. A spoofed tackle like that is utilized in phishing emails to trick recipients into considering that the e-mail originates from a reliable supply, particularly HMRC on this occasion. When customers hover over the “Replace Now” hyperlink as proven in Determine 1, customers are redirected to a malicious URL: hxxps://rumanta[.]com/cs/hmrc. This marks the initiation of the primary part of the assault.
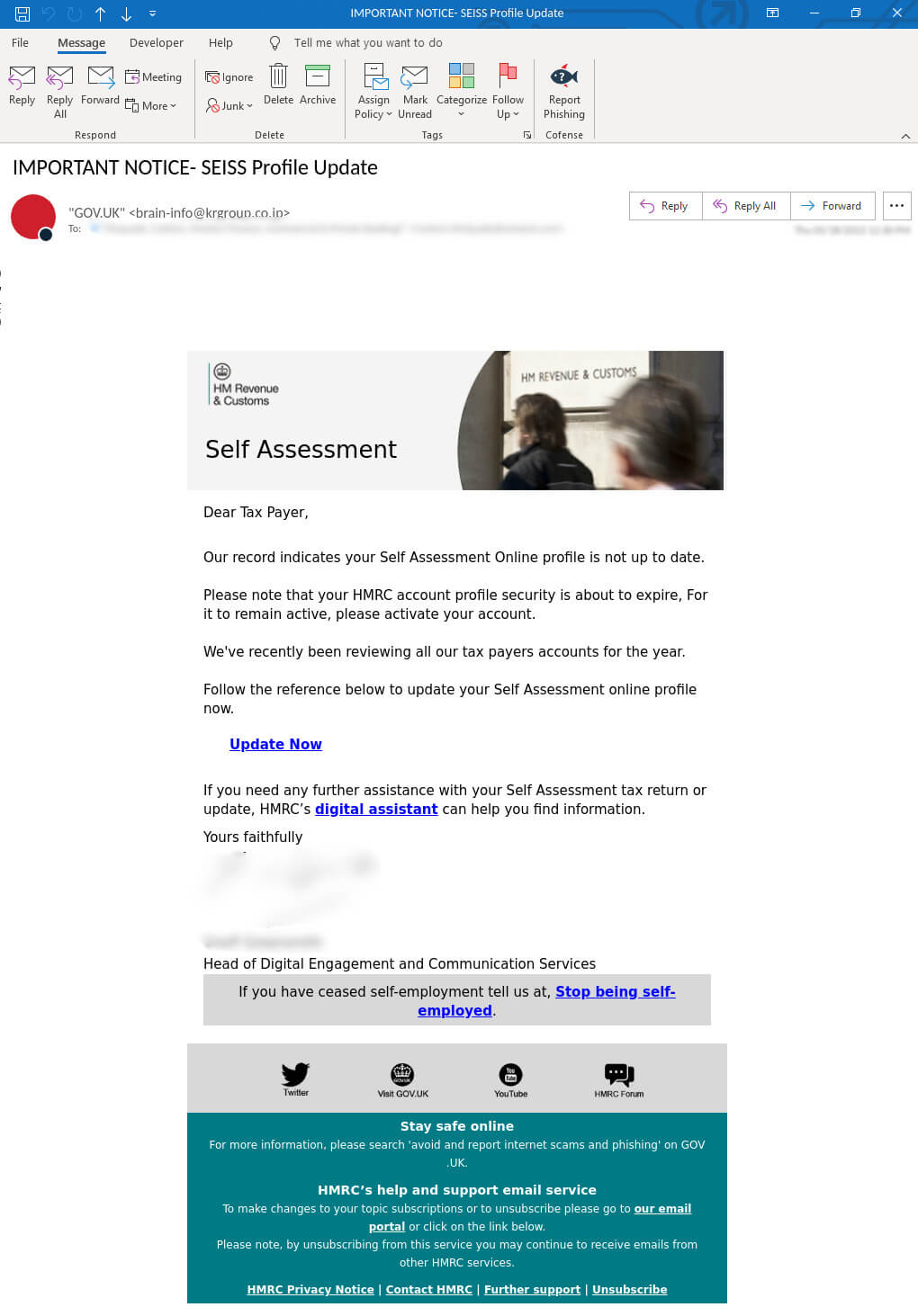
Determine 1 – E-mail physique
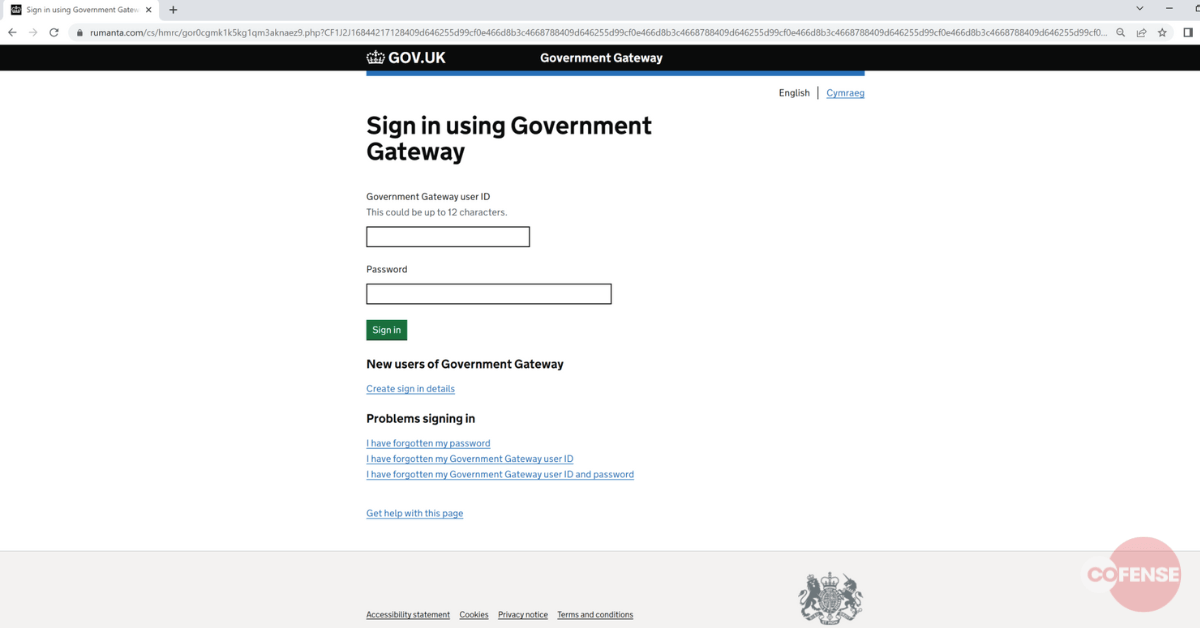
Upon clicking the hyperlink, it redirects to the webpage illustrated in Determine 2. At first sight, this webpage seems to be the real authorities gateway web page, which features as a centralized registration platform for accessing on-line authorities companies within the UK. But, upon additional scrutiny of the URL displayed within the search bar, it turns into obvious that it’s a phishing web site.
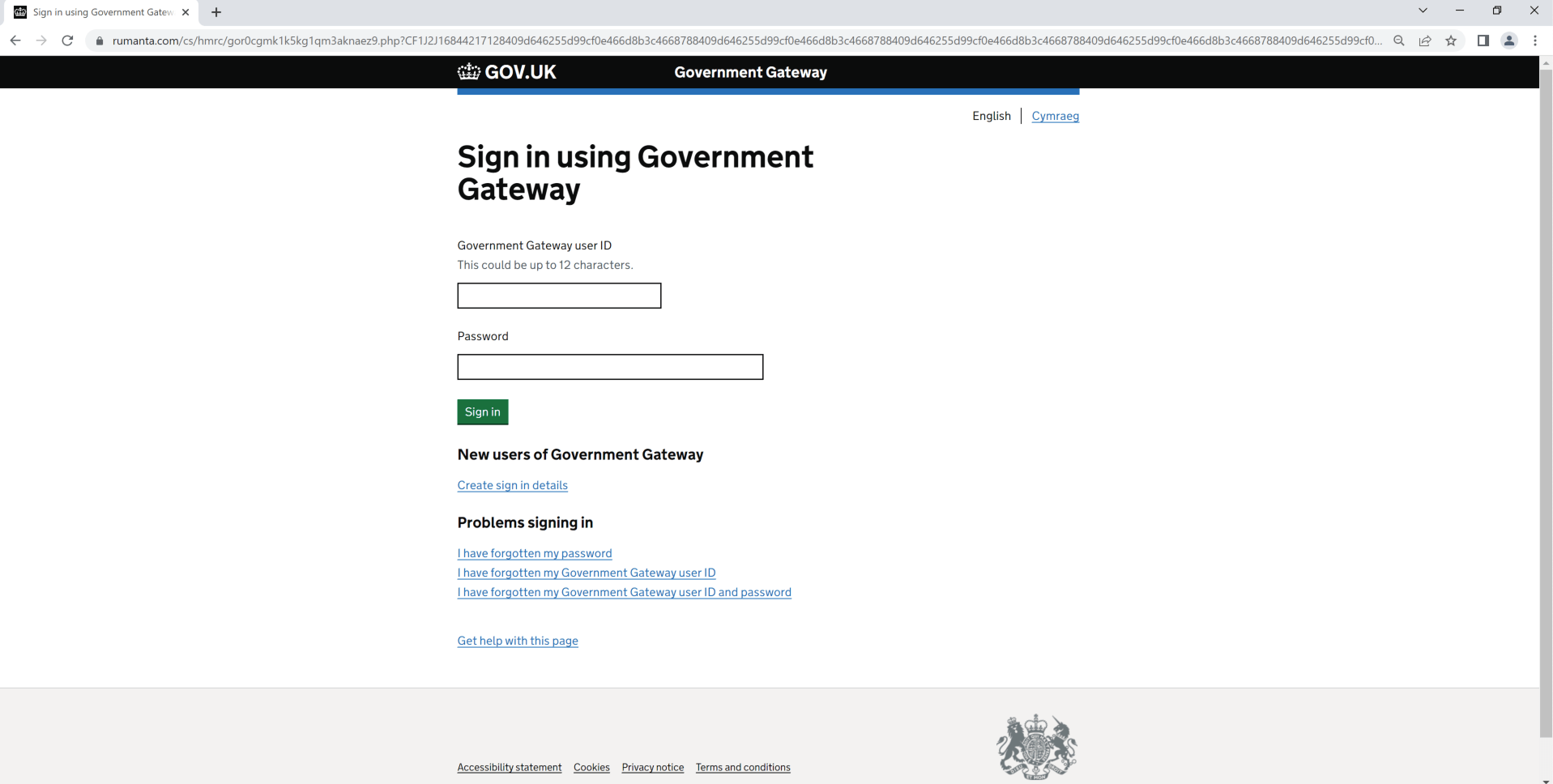
Determine 2 – Phishing Web page
As soon as the faux credentials are entered into the shape discipline, the HTTP POST request is shipped to the indicated tackle proven in Determine 3.The HTTP POST request directed to the URL https://rumanta[.]com/cs/hmrc/_mstr_php?_do=same_form signifies that the entered information within the kind is being despatched to this particular tackle to bear processing. This suggests that the submitted info, probably containing fabricated credentials, is being transmitted to a server hosted at rumanta[.]com. The intention behind this motion is to allow the risk actor to control or exploit the acquired information additional. We are able to confidently affirm that the area “rumanta[.]com” is experiencing downtime on the time of this writing.
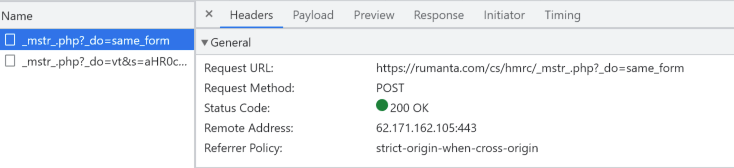
Determine 3 – HTTP POST
It’s essential for people to stay vigilant and cautious when dealing with emails and interacting with on-line platforms, particularly in the course of the self-assessment season. Recognizing the crimson flags of phishing makes an attempt, corresponding to urgency, suspicious sender addresses, and weird URLs, is essential to safeguarding private and monetary info.