Writer: Kian Buckley Maher
SEG Bypassed: Microsoft
The Cofense Phishing Protection Middle (PDC) has famous a rise within the variety of malicious emails utilising this assault vector. In an try to bypass conventional file and textual content detection software program, QR codes present risk actors with a unique tactic to encode malicious URLs.
Whereas it’s doable to open QR codes on a pc, they’re most conveniently accessed utilizing a wise cellphone or pill with its inbuilt digital camera. As a person’s private cellular gadget, they generally lack the safety from community and endpoint options which might generally stop entry to malicious URLs and create alerts for safety groups to analyze. With many of the assault occurring exterior of the safety bubble created by an organization, it’s tougher to assemble proof of the assault and monitoring any subsequent actions taken by the person.
Seen by a cellphone display screen these webpages, which endeavour to impersonate authentic web sites, are much less more likely to be noticed. Their imperfections can simply be attributed to the buggy nature of cellular browsers and their fixed wrestle displaying webpages effectively, particularly when a web page is primarily accessed by a desktop browser.
Preliminary Electronic mail
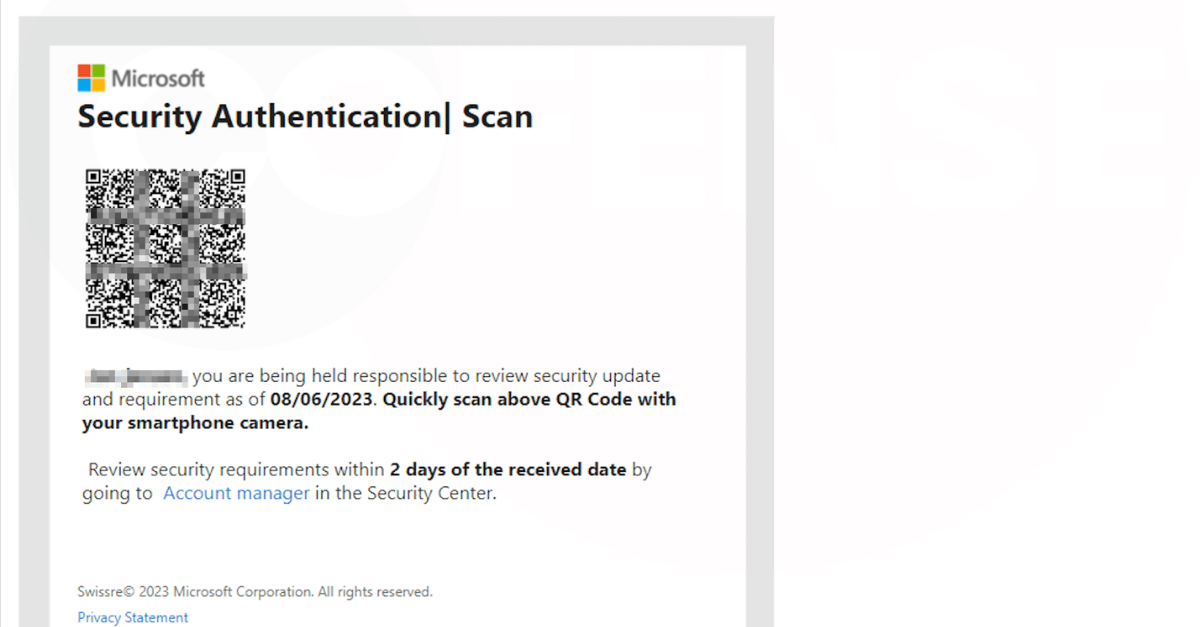
The recipients of those campaigns will obtain an electronic mail from the risk actor, it’s gentle on vital info, features a slight sense urgency as to its content material, and lacks any custom indicators of compromise like an attachment or hyperlink. This will likely invoke a want from the person to analyze additional. On this context the QR code is positioned with prominence to attract speedy consideration and lure the person to rapidly scan it with their smartphone.
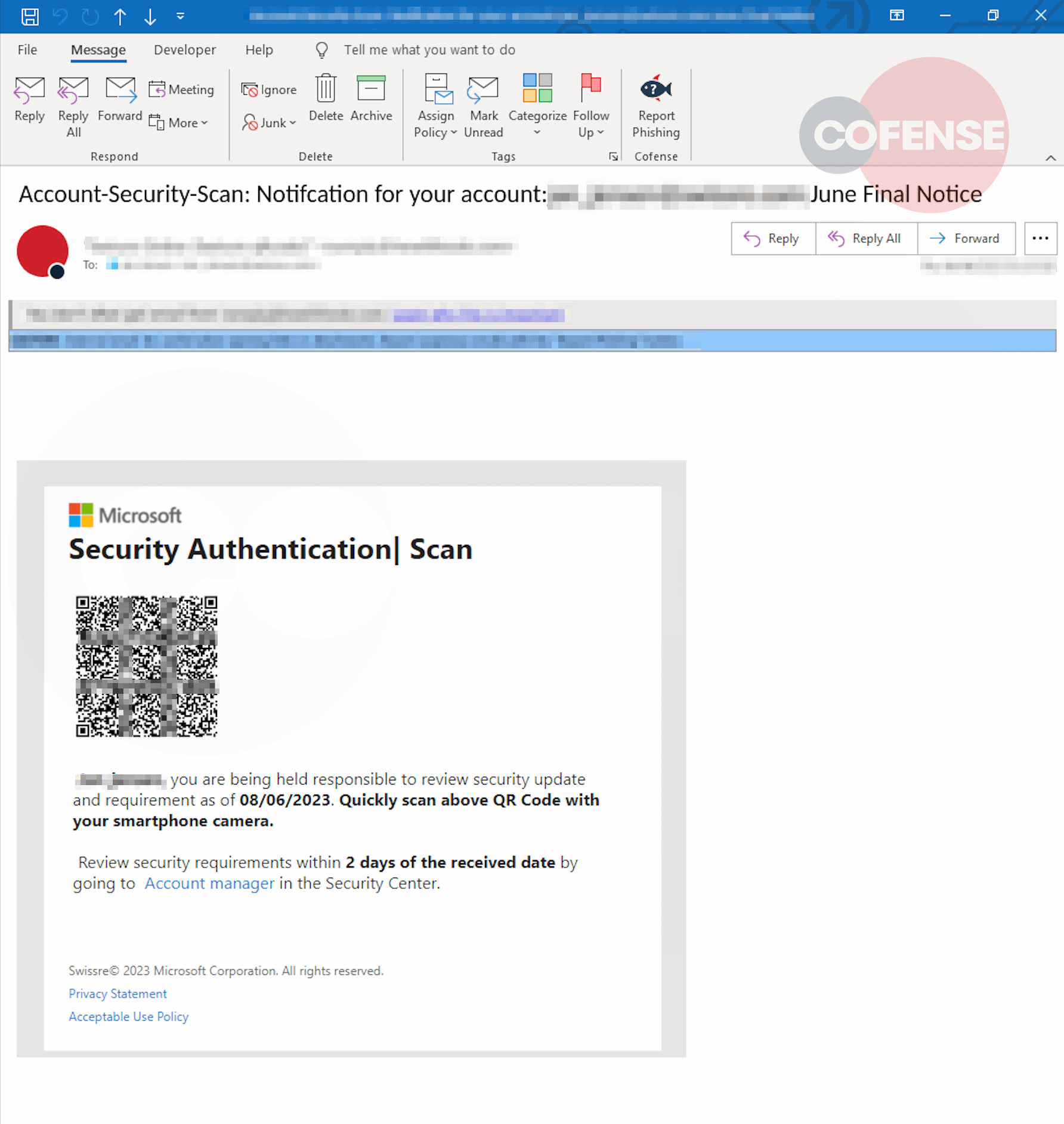
Determine 1 – QR Electronic mail
As soon as scanned with a QR code software on a wise cellphone the URL can be decoded. Upon agreeing to navigate additional the person is offered with a captcha verify, utilised on this method it gives the look of the ultimate touchdown web page itself being authentic.
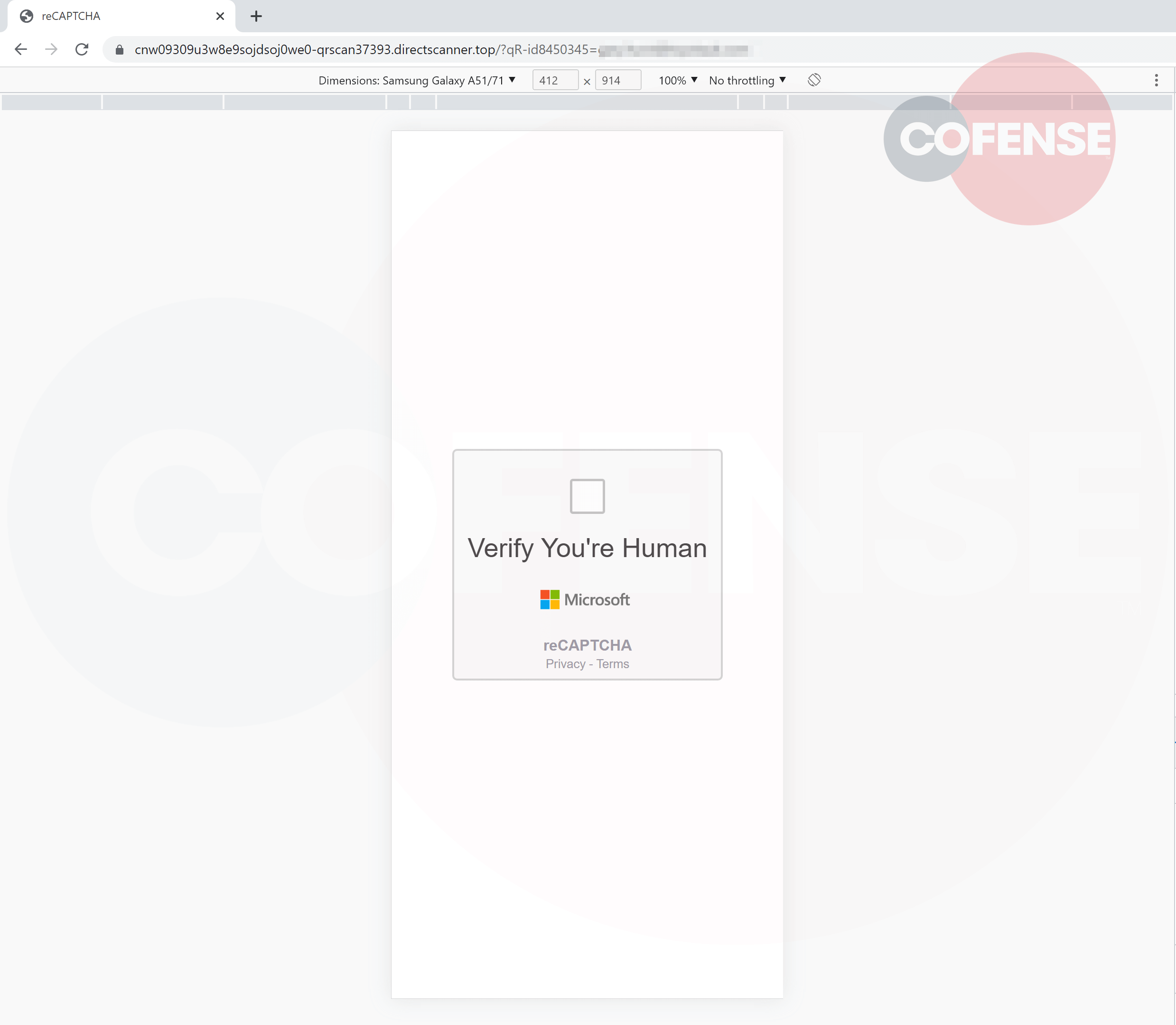
Determine 2 – Captcha Touchdown Web page
After interacting with the captcha, a loading icon will seem adopted by a inexperienced checkmark, after which person is redirected to the malicious web page. In most up-to-date circumstances famous by the PDC this methodology deploys a standard Microsoft credential phish. Nonetheless there have been quite a few situations of supply service impersonations additionally making use of a QR code.
The touchdown web page displays the intent of the preliminary electronic mail acquired, consisting of a generic Microsoft login web page. Nothing about this web page will instantly stand out to an unsuspecting person apart from the URL current on the high of the web page. The web page in Determine 2 and three was accessed with the gadget emulation included in Chrome’s developer instruments. Nonetheless, on a cellphone display screen this clearly incorrect and weird URL goes to be tougher to detect as a result of smaller dimension of the tackle bar.
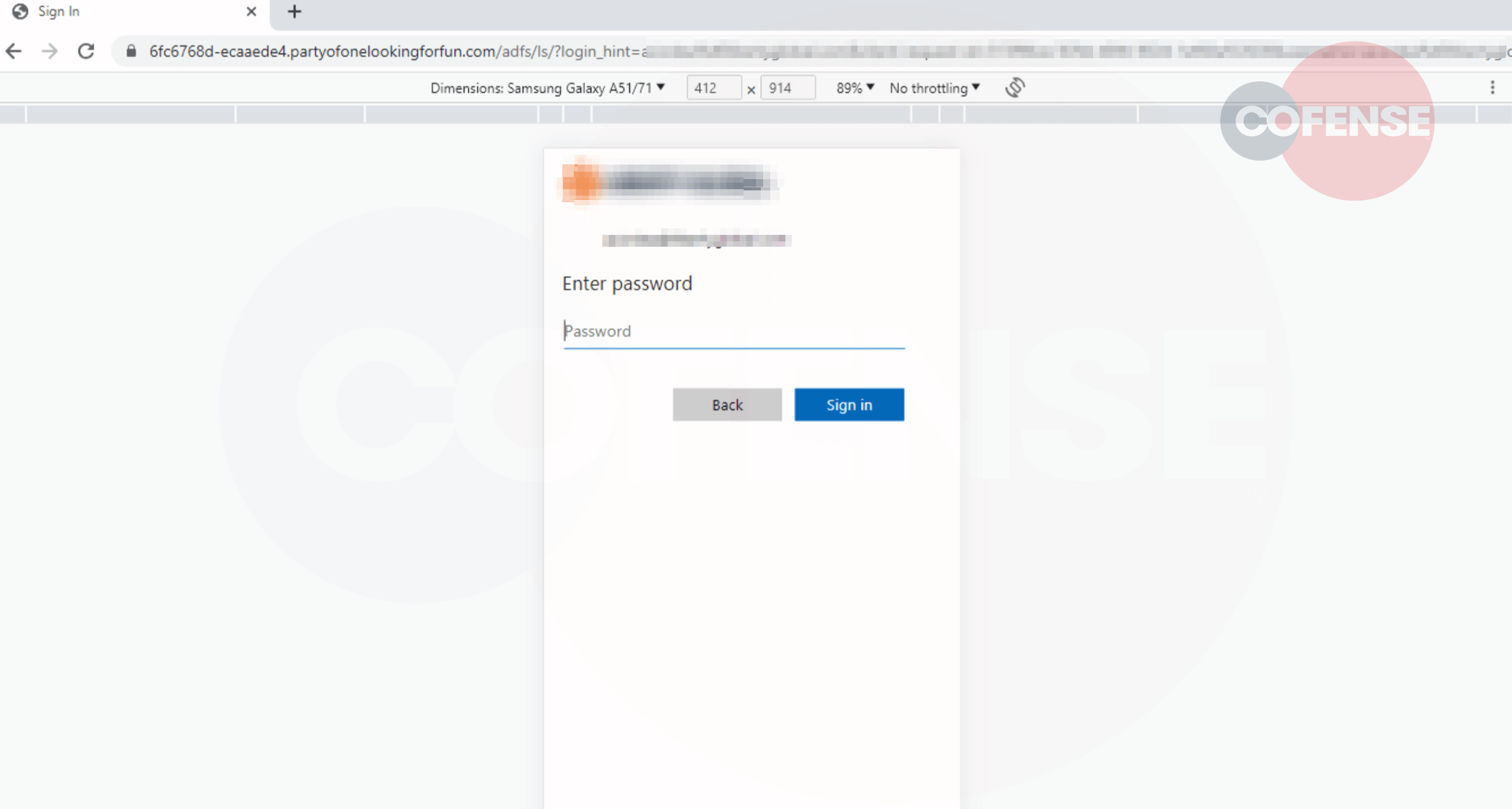
Determine 3 – Microsoft Phishing Web page
Customers needs to be cautious of scanning QR codes from any supply they don’t belief. If unsure, it’s advisable to utilize a web-based service to scan the QR code such because the one seen under.
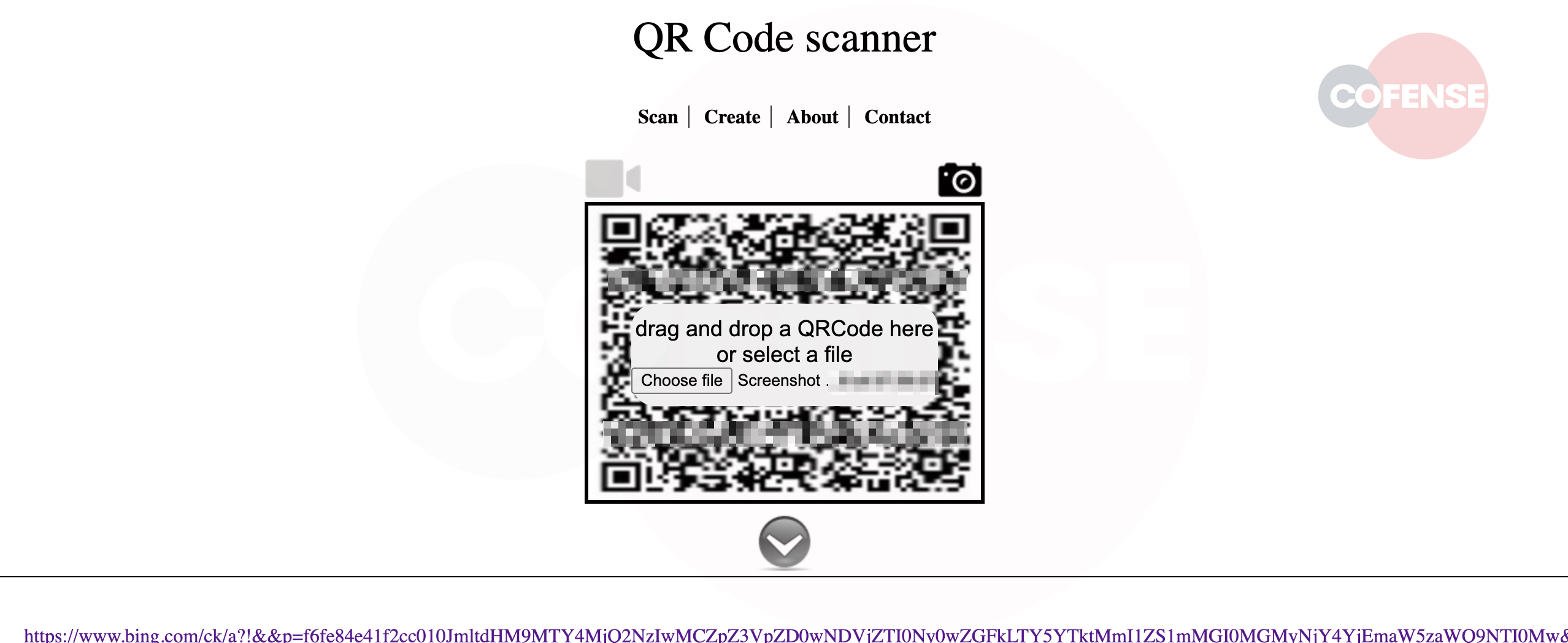
Determine 4 – Browser QR Code Scanner
These websites will allow an correct assessment of the URL associated to the QR code and stop unintended navigation to a probably malicious web site.
We advocate educating staff to those risks and guaranteeing they may take additional time to ensure an electronic mail is authentic earlier than interacting with it additional. Knowledgeable Staff making use of the suite of electronic mail safety and phishing training merchandise supplied by Cofense, you’ll be able to extra successfully make sure that phishing emails reminiscent of this have much less of an opportunity of affecting your enterprise.