QR Code utilization has skyrocketed lately. In truth, 97% of customers had no thought what a QR Code was in 2012. However by 1Q22, Americas led the world in QR code utilization with 2,880,960 scans, making these quirky codes an interesting path for brand spanking new and complex phishing campaigns.1,2
INKY lately caught a mess of QR Code phish, however earlier than leaping in, we’d wish to shortly make you an skilled on QR Code fundamentals. (For those who’re already an skilled, be at liberty to learn forward.)
How QR Codes Got here to Be
The evolution of QR codes is fairly attention-grabbing. First got here barcodes, which have been developed within the Sixties in Japan when the financial system was thriving. Up till that time, cashiers needed to enter every worth into the register by hand. Enterprise was thriving and so was carpal tunnel syndrome. An answer was sought out and located. When scanned by an optical sensor, barcodes may shortly ship the pc product and worth info. The downside was {that a} barcode can solely maintain about 20 alphanumeric characters of knowledge. Ultimately, {the marketplace} wished extra, and Japanese firm Denso Wave Included answered the decision. In 1994, the primary QR code was launched.
The QR code’s greatest bump got here in 2002 with the discharge of a cell phone characteristic that might learn the codes. Immediately, QR codes are thought of a necessary advertising instrument. Sadly, it appears to be like like QR codes are going to be fairly indispensable to phishers too.
Okay…let’s get again to our malicious QR Code phish.
Quick Response or Quickly Retrieving? What INKY Caught
Technically, QR stands for fast response due to QR codes’ capacity to supply info within the snap of a finger. Sadly, that’s additionally the pace with which cybercriminals have shortly retrieving worker credentials.
INKY lately caught tons of of QR code phishing emails and whereas these credential-harvesting emails got here from a number of completely different hackers, the similarities are clear. They embrace:
- Use of image-based phishing tactic
- Microsoft impersonation
- Showing to come back from contained in the recipient’s group
- Asking the worker to resolve a selected account subject, comparable to 2FA setup, account verification, or password modifications.
- Instilling a way of urgency
- Repercussions for not performing the duty at hand (safe your password, keep away from account lockout, be held accountable)
- Prompting workers have been informed to scan a malicious QR code discovered within the e mail.
Let’s have a look at a number of examples.
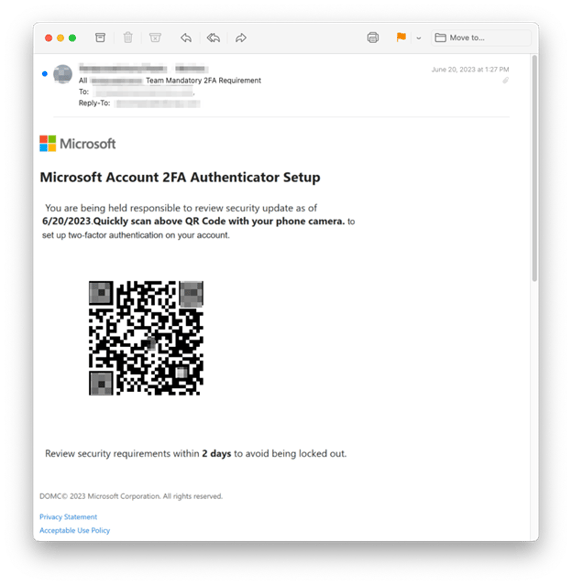
The instance beneath got here from a hijacked account for a Japanese retail retailer. INKY stopped 104 of those threats from reaching the recipients inbox.
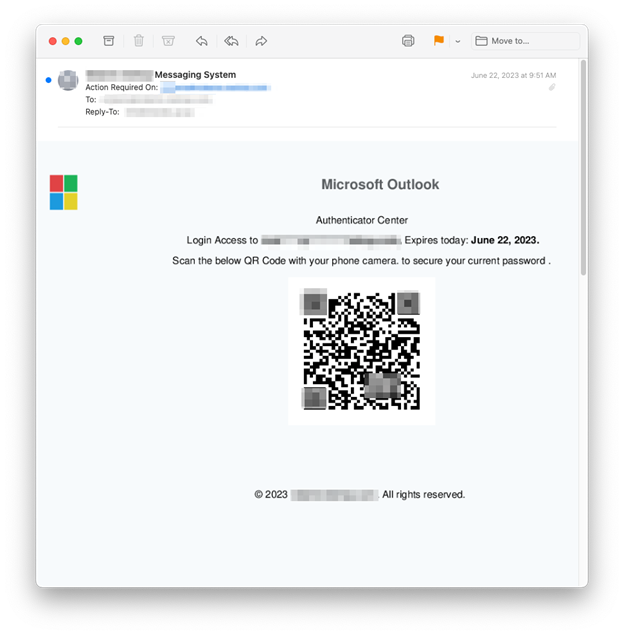
The e-mail beneath is a bit completely different and was despatched to 174 INKY customers and originated from the hijacked account of an American producer and a number of other iCloud accounts that have been created particularly to ship phishing emails.
Our third instance, additionally discovered beneath, originated from the hijacked account of a digital advertising service that operates in Canada, France, and america. INKY caught 267 of those damaging little phish.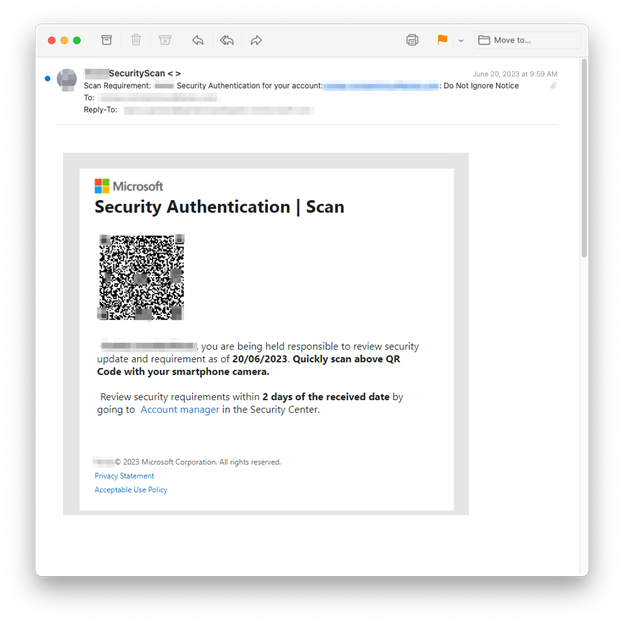
It’s essential to notice that these three QR Code phishing emails weren’t despatched to only a handful of INKY prospects. They have been a part of a “spray and pray” strategy. Phishers ship their emails to as many individuals as attainable (spray) after which hope (pray) {that a} robust majority of recipients will fall for the ruse. On this case, a number of industries have been attacked. Of the 545 emails famous up to now, supposed victims have been within the U.S. and Australia. They included non-profits, a number of wealth administration companies, administration consultants, a land surveyor, flooring firm, and extra.
The story doesn’t finish right here. What seems to be e mail textual content within the examples above is one thing altogether completely different.
Picture-Primarily based Phishing Messages Simply Swim by Safe E-mail Gateways (SEGs)
Malicious QR codes are only one a part of the puzzle. With out the best e mail safety in place, these harmful messages would have gone undetected resulting from one other recognized phishing tactic – image-based textual messages despatched as an attachment.
Safe E-mail Gateways (SEGs) and related safety programs are designed to detect fundamental textual clues that sign phishing. A method round that’s to design an e mail with out textual content. On this case, the examples above truly include no textual content. That’s proper, no textual content. As a substitute, the textual content is embedded in a picture and connected to the phishing e mail.
This works as a result of most e mail purchasers robotically show the picture file on to the recipient slightly than delivering a clean e mail with a picture connected. Because of this, recipients don’t know that they’re a screenshot of textual content as a substitute of HTML code with textual content and since there aren’t any hyperlinks or attachments to open, the e-mail feels secure.
Not like SEGs, INKY makes use of optical character recognition (OCR) that extracts the textual content from an connected e mail and makes use of it together with different synthetic intelligence algorithms to detect an e mail as harmful.
Following the Malicious QR Code
INKY decoded a malicious QR code to see the place it was taking recipients. As predicted, victims scanning the QR code are unknowingly taken to a phishing web site in order that their credentials will be stolen. They’re shortly made to really feel comfy as a result of malicious hyperlinks embedded in QR codes include the recipient’s e mail deal with as a URL parameter to prefill private information as soon as the phishing web site masses. Briefly, issues really feel acquainted.
As a part of the decoding, we modified the URL parameter to “batman@batman.com” and on this instance, we visited hxxps://rtsp1[.]com?u=batman@batman.com
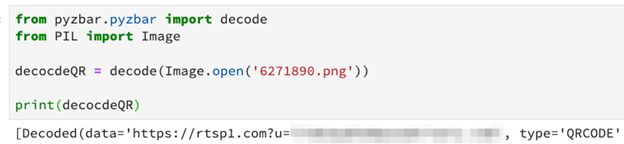
rtsp1[.]com is a newly created area set as much as redirect to y7y[.]on-line, one other newly created area that’s internet hosting a Microsoft credential harvesting web site.
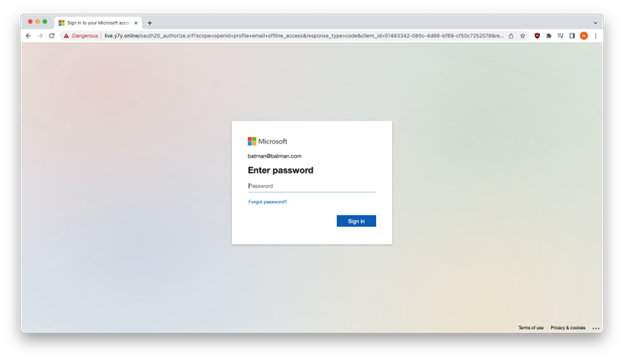
The Microsoft impersonation web site accepted our pretend credentials.
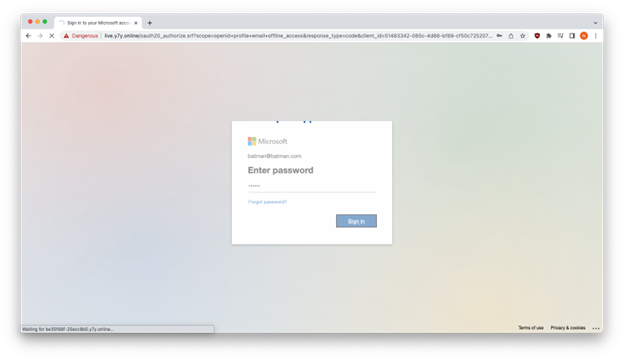
As you possibly can see beneath, Google Chrome warned us that y7y[.]on-line harvested the pretend credentials we entered.
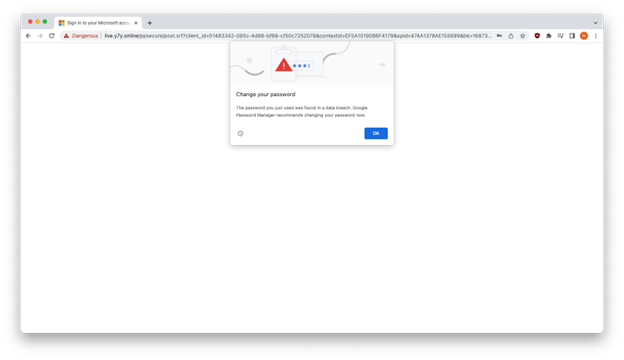
In the long run, phishers will have the ability to simply get hold of the credentials of weak, unprotected victims.
Let’s summarize among the ways used on this QR Code phishing rip-off.
Recap of Methods
- Model impersonation — makes use of components of a well known model to make an e mail look as if it got here from that firm.
- Credential harvesting — happens when a sufferer thinks they’re logging in to one in all their useful resource websites however are actually getting into credentials right into a dialog field owned by the attackers.
- Picture-based phish — textual phish message is embedded in a picture.
- QR code- conceals the malicious URL from recipients and safety software program.
Greatest Practices: Steering and Suggestions
- Recipients ought to use a unique technique of communication to substantiate every time they’re requested to finish a brand new activity.
- Rigorously examine the sender’s e mail deal with. In these circumstances, emails declare to come back from Microsoft and the recipient’s employer however the sender’s area has no relation to those entities.
- Don’t scan QR codes from unknown sources. Web sites reached by QR codes may host malicious code that exploits vulnerabilities or steals delicate information.
- Be cautious when getting into monetary and private info on a web site reached with a QR code.
INKY is the behavioral e mail safety platform that blocks threats, prevents information leaks, and coaches customers to make sensible choices relating to the security of their e mail. Like a cybersecurity coach, it alerts suspicious behaviors with interactive banners that information customers to take secure motion on any system or e mail shopper. IT groups don’t face the burden of filtering each e mail themselves or sustaining a number of programs. By highly effective know-how and intuitive person engagement, INKY retains unhealthy actors out for good. Begin a free trial or schedule a demo at the moment.
———————-
INKY is an award-winning, behavioral e mail safety platform that blocks phishing threats, prevents information leaks, and coaches customers to make sensible choices. Like a cybersecurity coach, INKY alerts suspicious behaviors with interactive e mail banners that information customers to take secure motion on any system or e mail shopper. IT groups don’t face the burden of filtering each e mail themselves or sustaining a number of programs. By highly effective know-how and intuitive person engagement, INKY retains phishers out for good. Be taught why so many corporations belief the safety of their e mail to INKY. Request a web based demonstration at the moment.
1Supply: www.inc.com/eric-v-holtzclaw/qr-codes-dont-bother-five-reasons.html
2Supply: www.qrcode-tiger.com/qr-code-statistics-2022-q1
3Supply: www.qrcode.com/en/historical past/

