Adopting AI is existentially very important for many companies
Machine Studying (ML) and generative AI (GenAI) are revolutionizing the way forward for work. Organizations perceive that AI helps construct innovation, keep competitiveness, and enhance the productiveness of their workers. Equally, organizations perceive that their information supplies a aggressive benefit for his or her AI functions. Leveraging these applied sciences presents alternatives but in addition potential dangers to organizations, as embracing them with out correct safeguards can lead to vital mental property and reputational loss.
In our conversations with clients, they often cite dangers equivalent to information loss, information poisoning, mannequin theft, and compliance and regulation challenges. Chief Info Safety Officers (CISOs) are beneath strain to adapt to enterprise wants whereas mitigating these dangers swiftly. Nonetheless, if CISOs say no to the enterprise, they’re perceived as not being crew gamers and placing the enterprise first. However, they’re perceived as careless if they are saying sure to doing one thing dangerous. Not solely do CISOs have to sustain with the enterprise’ urge for food for development, diversification, and experimentation, however they should sustain with the explosion of applied sciences promising to revolutionize their enterprise.
Half 1 of this weblog sequence will focus on the safety dangers CISOs have to know as their group evaluates, deploys, and adopts enterprise AI functions.
Your information platform needs to be an knowledgeable on AI safety
At Databricks, we imagine information and AI are your most valuable non-human property, and that the winners in each trade might be information and AI firms. That is why safety is embedded within the Databricks Information Intelligence Platform. The Databricks Information Intelligence Platform permits your complete group to make use of information and AI. It is constructed on a lakehouse to supply an open, unified basis for all information and governance, and is powered by a Information Intelligence Engine that understands the individuality of your information.
Our Databricks Safety crew works with 1000’s of shoppers to securely deploy AI and machine studying on Databricks with the suitable security measures that meet their structure necessities. We’re additionally working with dozens of consultants internally at Databricks and within the bigger ML and GenAI group to establish safety dangers to AI programs and outline the controls essential to mitigate these dangers. We now have reviewed quite a few AI and ML danger frameworks, requirements, suggestions, and steerage. In consequence, we now have strong AI safety tips to assist CISOs and safety groups perceive the right way to deploy their organizations’ ML and AI functions securely. Nonetheless, earlier than discussing the dangers to ML and AI functions, let’s stroll by means of the constituent parts of an AI and ML system used to handle the info, construct fashions, and serve functions.
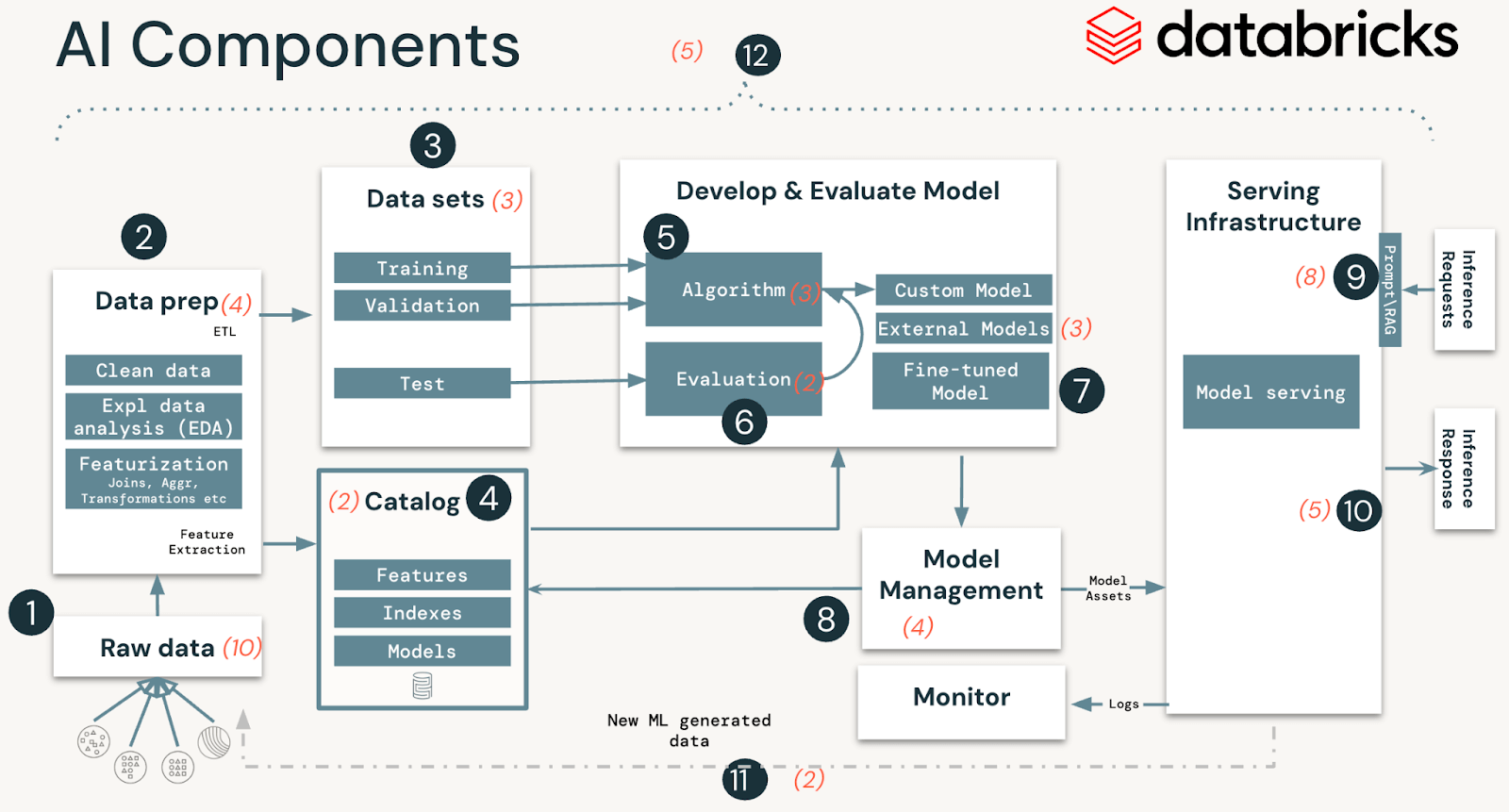
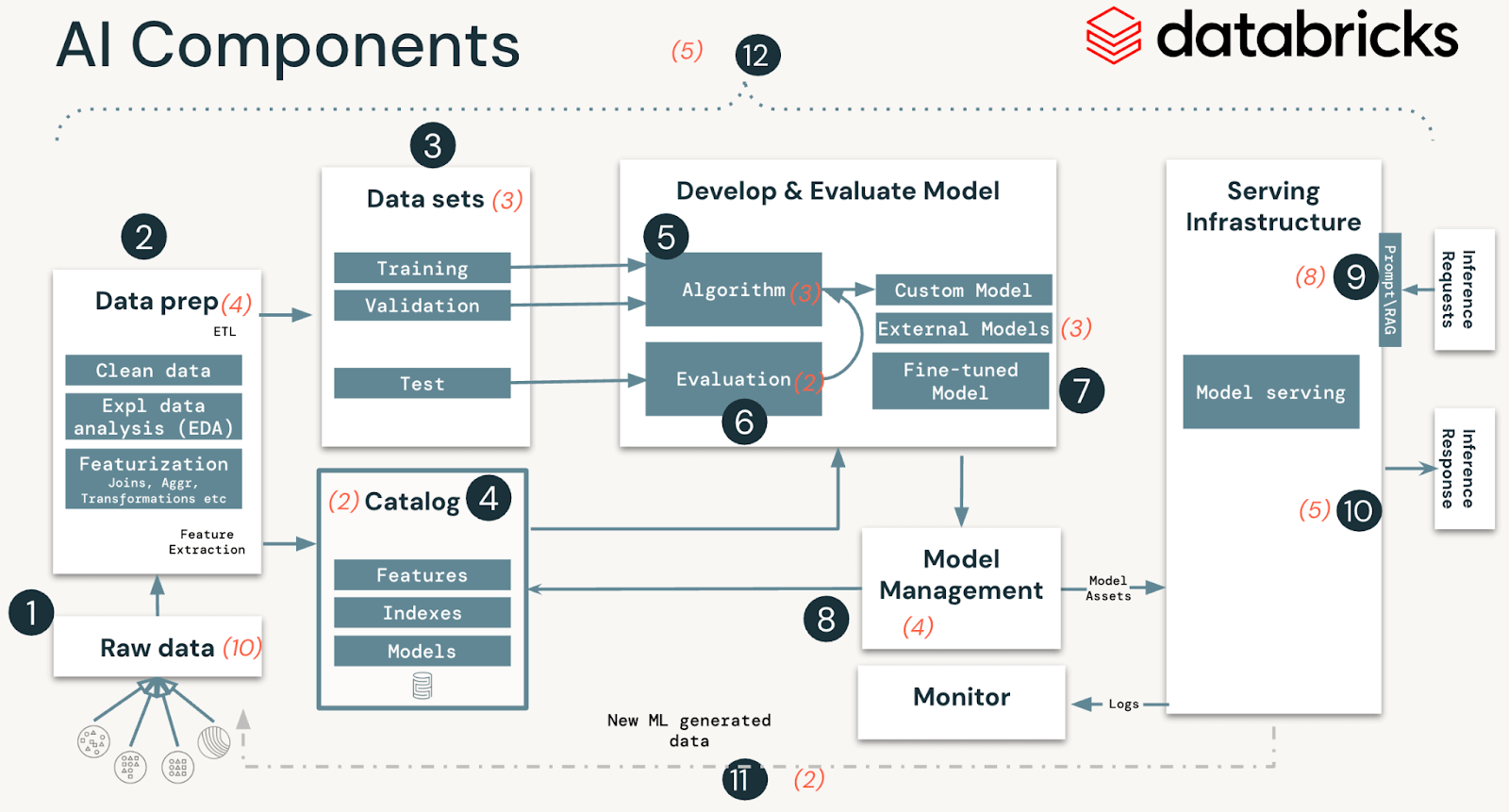
Understanding the core parts of an AI system for efficient safety
AI and ML programs are comprised of knowledge, code, and fashions. A typical system for such an answer has 12 foundational structure parts, broadly categorized into 4 main levels:
- Information operations encompass ingesting and reworking information and making certain information safety and governance. Good ML fashions depend upon dependable information pipelines and safe infrastructure.
- Mannequin operations embrace constructing customized fashions, buying fashions from a mannequin market, or utilizing SaaS LLMs (like OpenAI). Creating a mannequin requires a sequence of experiments and a approach to monitor and examine the circumstances and outcomes of these experiments.
- Mannequin deployment and serving consists of securely constructing mannequin photos, isolating and securely serving fashions, automated scaling, charge limiting, and monitoring deployed fashions.
- Operations and platform embrace platform vulnerability administration and patching, mannequin isolation and controls to the system, and approved entry to fashions with safety within the structure. It additionally consists of operational tooling for CI/CD. It ensures the entire lifecycle meets the required requirements by retaining the distinct execution environments – growth, staging, and manufacturing for safe MLOps.
MLOps is a set of processes and automatic steps to handle the AI and ML system’s code, information, and fashions. MLOps needs to be mixed with safety operations (SecOps) practices to safe your entire ML lifecycle. This contains defending information used for coaching and testing fashions and deploying fashions and the infrastructure they run on from malicious assaults.
High safety dangers of AI and ML programs
Technical Safety Dangers
In our evaluation of AI and ML programs, we recognized 51 technical safety dangers throughout the 12 parts. Within the desk under, we define these primary parts that align with steps in any AI and ML system and spotlight the forms of safety dangers our crew recognized:
| System stage | System parts (Determine 1) | Potential safety dangers |
|---|---|---|
| Information operations |
|
19 particular dangers, equivalent to
|
| Mannequin operations |
|
12 particular dangers, equivalent to
|
| Mannequin deployment and serving |
|
13 particular dangers, equivalent to
|
| Operations and Platform |
|
7 particular dangers, equivalent to
|
Databricks has mitigation controls for all the above-outlined dangers. In a future weblog and whitepaper, we are going to stroll by means of the entire checklist of dangers in addition to our steerage on the related controls and out-of-the-box capabilities like Databricks Delta Lake, Databricks Managed MLflow, Unity Catalog, and Mannequin Serving that you need to use as mitigation controls to the above dangers.
Organizational Safety Dangers
Along with the technical dangers, our discussions with CISOs have highlighted the need of addressing 4 organizational danger areas to ease the trail to AI and ML adoption. These are key to aligning the safety perform with the wants, tempo, outcomes and danger urge for food of the enterprise they serve.
- Expertise: Safety organizations can lag the remainder of the group when adopting new applied sciences. CISOs want to know which roles of their expertise pool ought to upskill to AI and implement MLSecOps throughout departments.
- Working mannequin: Figuring out the important thing stakeholders, champions, and enterprise-wide processes to securely deploy new AI use circumstances is vital to assessing danger ranges and discovering the right path to deploying functions.
- Change administration: Discovering hurdles for change, speaking expectations, and eroding inertia to speed up by leveraging an organizational change administration framework, e.g., ADKAR, and so forth., helps organizations to allow new processes with minimal disruption.
- Resolution help: Tying technical work to enterprise outcomes for prioritizing which technical efforts or enterprise use circumstances is vital to arriving at a single set of organization-wide priorities.
Mitigate AI safety dangers successfully with our CISO-driven workshop
CISOs are instinctive danger assessors. Nonetheless, this superpower fails most CISOs in the case of AI. The first motive is that CISOs do not have a easy psychological mannequin of an AI and ML system that they will readily visualize to synthesize property, threats, impacts, and controls.
That can assist you with this, the Databricks Safety crew has designed a brand new machine studying and generative AI safety workshop for CISOs and safety leaders. The content material of those workshops is additional being developed right into a framework for managing AI Safety to render CISOs’ instinctive superpower of assessing danger to be operable and efficient relating to AI.
As a sneak peek, here is the top-line strategy we suggest for managing the technical safety dangers of ML and AI functions at scale:
- Determine the ML Enterprise Use Case: Be sure that there’s a well-defined use case with stakeholders you are attempting to safe adequately, whether or not already carried out or in planning phases.
- Decide ML Deployment Mannequin: Select an applicable mannequin (e.g., Customized, SaaS LLM, RAG, fine-tuned mannequin, and so forth.) to find out how shared tasks (particularly for securing every element) are cut up throughout the 12 ML/GenAI parts between your group and any companions concerned.
- Choose Most Pertinent Dangers: From our documented checklist of 51 ML dangers, pinpoint essentially the most related to your group primarily based on the end result of step #2.
- Enumerate Threats for Every Danger: Determine the particular threats linked to every danger and the focused ML/GenAI element for each menace.
- Select and Implement Controls: Choose controls that align along with your group’s danger urge for food. These controls are outlined generically for compatibility with any information platform. Our framework additionally supplies tips on tailoring these controls particularly for the Databricks atmosphere.
- Operationalize Controls: Decide management homeowners, lots of whom you would possibly inherit out of your information platform supplier. Guarantee controls are carried out, monitored for effectiveness, and recurrently reviewed. Changes could also be wanted primarily based on modifications in enterprise use circumstances, deployment fashions, or evolving menace landscapes.
Study extra and join with our crew
If you happen to’re fascinated by taking part in one in all our CISO workshops or reviewing our upcoming Databricks AI Safety Framework whitepaper, contact [email protected].
If you’re interested in how Databricks approaches safety, please go to our Safety and Belief Heart.