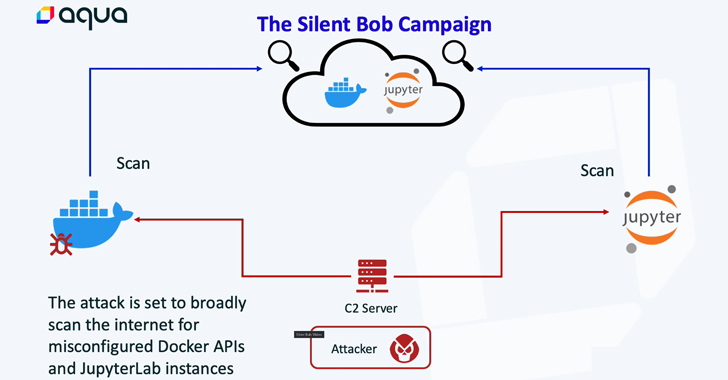
136
Distant work has all the time been round, but it surely gained immense reputation lately as the company world adjusted to restrictions that got here with the COVID-19 pandemic. Regardless of the pandemic softening, many firms have caught with distant work as a result of comfort it gives staff.
Nevertheless, whereas everybody focuses on the comfort of distant work, they usually disregard a crucial side; cybersecurity. Many cybersecurity challenges threaten distant work, and firms and staff should take measures in opposition to them. Step one to combating these challenges is understanding distant work safety.
Due to this fact, on this article, Venn will talk about cybersecurity challenges, dangers, and easy options to deal with them.
Frequent Cybersecurity Challenges for Distant Work
With the comfort of distant work comes cybersecurity challenges that it’s essential to defend your self in opposition to for an excellent expertise. Listed below are the commonest cybersecurity challenges you need to be cautious of when practising distant work:
1. Phishing
Within the early months of the pandemic, phishing assaults soared globally as malicious people and teams tricked victims into offering personal/privileged info, which was used to steal extra information, commit identification fraud, break into financial institution accounts, and rather more.
In April 2020, the Nationwide Cyber Safety Middle recorded no less than 350 instances of cyber assaults (phishing, direct assaults on firms, and extra) in Switzerland, in comparison with the norm of 100-150 month-to-month. In 2020, Australia misplaced over AUD 851 million to scams — a report quantity.
Regardless that many firms have taken measures to protect them in opposition to phishing, scammers are discovering new, extra subtle methods to idiot potential victims, making the scheme a troublesome problem for distant work.
2. Weaker safety controls
A company setting sometimes has a cybersecurity structure with safe firewalls in opposition to malicious site visitors. Additionally, the IT division is usually busy watching staff’ on-line exercise to identify any threats earlier than they may do injury. On this setting, probably fraudulent emails are filtered out, and phishing assaults are nipped within the bud.
However distant employees shouldn’t have the luxurious of such safety at house. Corporations usually lack the capability to increase monitoring to all of the endpoints. The weaker safety controls usually go away company information susceptible to theft.
3. Private units for work
Lately, the Deliver Your Personal System (BYOD) or Deliver Your Personal PC (BYOPC) coverage has gained reputation. The observe permits employees to make use of their private units for work. Whereas this observe gives comfort, its safety threat is gigantic.
Workers who use their private units for work obtain info or apps for private use, however the act could compromise delicate firm information saved on the identical units. Additionally, there’s a threat of an worker holding on to confidential info after leaving the corporate with none manner for the agency to erase the info.
Moreover, company information could also be in danger if staff don’t set up common safety updates on their work units. Furthermore, staff with separate work and private computer systems for distant work may compromise company information by recklessly transferring information between each units.
4. Weak passwords
Cybercriminals are always discovering new methods to crack passwords, and staff who safe their distant work units with weak passwords assist the attackers get what they need. As soon as attackers crack a password, they try and entry different accounts with it, which can be problematic if an worker makes use of the identical password for all or most of their accounts.
5. Insecure Wi-Fi networks
House or public wi-fi networks are often susceptible to malicious assaults as a result of their software program is never up to date. The unsecured networks could enable cyber criminals entry, enabling them to breach company information.
Methods to sort out cybersecurity challenges for distant work
Listed below are sensible methods to deal with the challenges that distant work poses:
1. Safe house community
A house Wi-Fi community doesn’t have the identical degree of safety as a company community, however there’s a method to safe your property community from malicious actors. First, arrange a singular password. Then, make your Wi-Fi invisible utilizing the Service Set Identifier (SSID). Additionally, replace your router’s software program frequently.
Moreover, strengthen your property community with strong encryption, ideally Wi-Fi Protected Entry 2 (WPA2).
2. Set up antivirus software program
Antivirus software program is a dependable device to reinforce distant work safety. Cybercriminals often goal house networks with assault vectors similar to malware, ransomware, adware, and distributed denial-of-service (DDoS). Antivirus software program robotically detects, blocks, and prevents these threats, together with phishing scams and viruses, from penetrating your community.
3. Use a Digital Personal Community (VPN)
Antivirus software program can’t present full safety; a VPN can full the safety cycle. A VPN can safe on-line site visitors and forestall attackers from snooping on you. We strongly advocate utilizing a VPN when on a public community.
4. Use robust passwords
Cybercriminals rely on weak passwords to make cracking simpler, however you may make your accounts virtually impenetrable by embracing distinctive passwords for each account. The passwords ought to embrace no less than 12 characters and use a mix of letters, particular symbols, and numbers.
We advocate putting in a reliable password supervisor to maintain all passwords protected. So that you shouldn’t have to memorize or save them in an unsecured location.
5. Follow protected web use
Workers have a accountability to make sure on-line security when working remotely. Meaning they need to keep away from public Wi-Fi or use a strong VPN in the event that they need to. Additionally, distant employees should be cautious of prying eyes when working in public areas.
Moreover, they need to scrutinize emails and texts to keep away from scams. Distant employees ought to assume that their rip-off e mail filters is not going to all the time work.