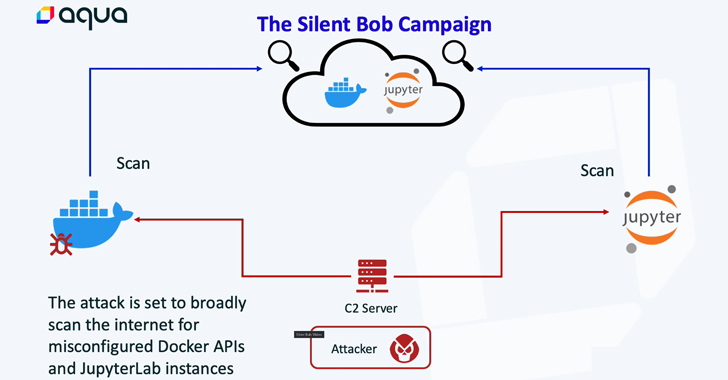
Cybersecurity researchers have unearthed an assault infrastructure that is getting used as a part of a “doubtlessly huge marketing campaign” towards cloud-native environments.
“This infrastructure is in early phases of testing and deployment, and is principally constant of an aggressive cloud worm, designed to deploy on uncovered JupyterLab and Docker APIs with the intention to deploy Tsunami malware, cloud credentials hijack, useful resource hijack, and additional infestation of the worm,” cloud safety agency Aqua stated.
The exercise, dubbed Silentbob in reference to an AnonDNS area arrange by the attacker, is alleged to be linked to the notorious cryptojacking group tracked as TeamTNT, citing overlaps in ways, methods, and procedures (TTPs). Nevertheless, the involvement of an “superior copycat” hasn’t been dominated out.
Aqua’s investigation was prompted within the aftermath of an assault concentrating on its honeypot in early June 2023, resulting in the invention of 4 malicious container photographs which might be designed to detect uncovered Docker and Jupyter Lab situations and deploy a cryptocurrency miner in addition to the Tsunami backdoor.
This feat is achieved via a shell script that is programmed to launch when the container begins and is used to deploy the Go-based ZGrab scanner to find misconfigured servers. Docker has since taken down the pictures from the general public registry. The listing of photographs are beneath –
- shanidmk/jltest2 (44 pulls)
- shanidmk/jltest (8 pulls)
- shanidmk/sysapp (11 pulls)
- shanidmk/blob (29 pulls)
shanidmk/sysapp, moreover executing a cryptocurrency miner on the contaminated host, is configured to obtain and run extra binaries, which Aqua stated might both be backup cryptominers or the Tsunami malware.
🔐 Privileged Entry Administration: Study Learn how to Conquer Key Challenges
Uncover totally different approaches to beat Privileged Account Administration (PAM) challenges and degree up your privileged entry safety technique.
Additionally downloaded by the container is a file named “aws.sh.txt,” a script that is probably designed to systematically scan the setting for AWS keys for subsequent exfiltration.
Aqua stated it discovered 51 servers with uncovered JupyterLab situations within the wild, all of which have been actively exploited or exhibited indicators of exploitation by menace actors. This features a “stay handbook assault on one of many servers that employed masscan to scan for uncovered Docker APIs.”
“Initially, the attacker identifies a misconfigured server (both Docker API or JupyterLab) and deploys a container or engages with the Command Line Interface (CLI) to scan for and determine extra victims,” safety researchers Ofek Itach and Assaf Morag stated.
“This course of is designed to unfold the malware to an rising variety of servers. The secondary payload of this assault features a crypto miner and a backdoor, the latter using the Tsunami malware as its weapon of selection.”