Written by Nathaniel Raymond
An evolving set of credential phishing exercise concentrating on Microsoft Workplace 365 credentials has been noticed reaching enterprise e-mail inboxes. This exercise is categorized by a number of key elements that make it stand out from different campaigns. Key elements embody:
- Over 120 distinctive phishing domains created utilizing the “bulletproof” registrar R01-RU, internet hosting 1000’s of phishing URLs.
- Abuse of Cloudflare CAPTCHA and IP proxying companies for efficacy and anti-analysis
- The usage of phishing companies attributable to the seemingly defunct Phishing-as-a-Service operation referred to as “Caffeine”, which was created by the package maker “MRxC0DER” and options an API for e-mail validation
Emails inside this exercise set are designed merely, utilizing an embedded hyperlink (normally an open redirect) to redirect the person to the credential harvesting web page. URLs of those credential harvesting web page have adopted sure patterns inside the previous yr. These patterns usually change after a time period, with the latest and largest change occurring in April 2023. E mail topics vary from notifications about passwords or messages to tax themes.
Who RU? “Bulletproof” Russian Registrar Used to Shield Menace Actor Id and Infrastructure
The phishing exercise set addressed on this report completely makes use of the area registrar R01-RU. R01-RU is recognized in varied hacking boards as a “bulletproof” Russian registrar the place risk actors can create and host a site securely for malicious functions, with out having to fret about shedding registered domains to fraud studies and shouldering the sunk price that comes with it. This makes registering and internet hosting domains engaging to adversaries. It might additionally imply that even when the phishing content material is eliminated, the adversary nonetheless controls the area and might reuse it in future campaigns.
Cloudy with a Likelihood of Phish: Cloudflare Providers Abused to Streamline and Shield Phishing Operations
Cloudflare is a official area safety service for on a regular basis customers to maintain their web site(s) safe. Nevertheless, this makes Cloudflare companies corresponding to CAPTCHAs, IP proxying, and different Cloudflare safety companies engaging to risk actors as properly. Abuse of Cloudflare companies allows risk actors to safe their very own operations and infrastructure in a number of methods:
- CAPTCHA companies be sure that the visiting shopper is an precise person from the focused nation by IP filtering
- CAPTCHA companies additionally be sure that phishing content material can’t be investigated by automated safety companies
- IP proxying companies enable the risk actor to cover the area’s unique internet hosting supplier to decelerate the takedown course of.
The exercise set mentioned on this report makes use of each CAPTCHAs and IP proxying for each credential phishing area created by R01-RU.

Determine 1: An instance of abused Cloudflare CAPTCHA companies
It’s only a PHaaS Mother: URLs Use Constant Patterns at Domains Probably Belonging to “Caffeine” Phishing-as-a-Service Supplier “MRxC0DER”
Phishing-as-a-Service is nothing new, granting adversaries with little-to-no technical information entry to phishing instruments corresponding to phishing kits, e-mail templates, emailer scripts, domains to host credential phishing pages, and rather more for a value. The risk actor “MRxCODER is a prolific phish package maker who provided such phishing companies and offered the companies by his now seemingly defunct store “Caffeine”. His model and emblem spoof the official stay streaming service Caffeine TV. Though the Caffeine phishing companies look like now not used or up to date, this marketing campaign exhibits that the kits it offered are nonetheless in use.
In Determine 2, we present one area (netsn[.]ru) that MRxC0DER particularly recognized as owned by his phishing service.
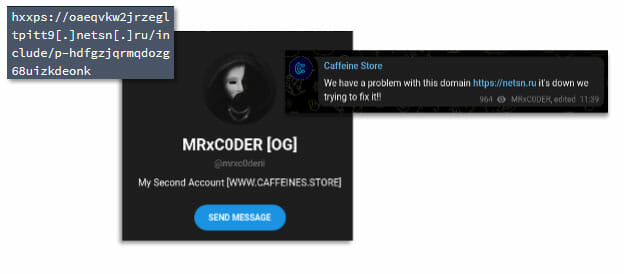
Determine 2:MRxC0DER Malicious Area Hyperlink
This area (netsn[.]ru) and its URLs have shared distinct patterns with the opposite domains in a bigger exercise set over nearly all of the previous yr:
- Every area is inside the .ru TLD
- Every area is registered by R01-RU
- Every URL discovered at these domains has a path containing alphanumeric strings of particular lengths, accompanied by one in every of a number of designated prefixes or suffixes
The Caffeine retailer on Telegram was created in September of 2021, promoting Model 8 of a Microsoft Workplace 365 credential phishing package, as proven in Determine 3. The web site caffeines[.]retailer goes additional again, with its creation on Might 1st, 2021. Though the Caffeine store is now not maintained on both Telegram or the principle web site, phishing emails that replicate these specific patterns have been noticed reaching person’s inboxes since Q3 of 2022.
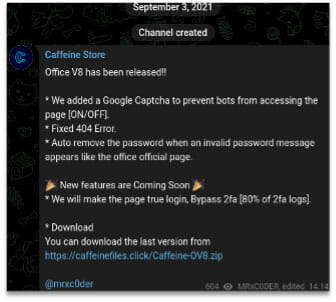
Determine 3: Caffeine Telegram Store Advertises CAPTCHA Providers In September 2021
A number of iterations of the phish package have been seen all through the life span of the Caffeine service, demonstrating MRxC0DER’s flexibility and adaptation. As an illustration, as proven in Determine 3, the Caffeine store beforehand marketed using Google CAPTCHA, however seems to have since switched to Cloudflare CAPTCHA. This flexibility can also lengthen to branding, and the Caffeine retailer might have been rebranded and/or moved whereas sustaining the identical important companies. Cofense has not but discovered proof of a brand new model or location at this level. Nevertheless, given the upkeep of Caffeine-related domains, we surmise that MrXC0DER stays energetic, even when he’s now not promoting his companies on the Caffeine retailer. Additionally it is vital to notice that expert risk actors can modify and deploy phishing kits they’ve discovered, or beforehand bought, to suit their very own wants
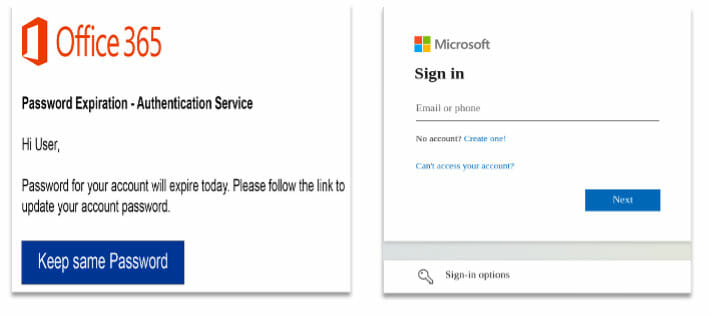
Determine 4: E mail and Phishing Web page Instance
The emails and the hosted phishing pages inside this exercise set had been designed with simplicity in thoughts. Determine 5 exhibits an instance of an e-mail with an embedded redirect hyperlink that takes the person to the credential phish, additionally in Determine 5. The hyperlinks embedded in these emails usually abuse open redirects at each well-known and little-known official web sites, making protection through automated IOC recognition at this stage troublesome. Nevertheless, customers ought to obtain constant phishing consciousness coaching with the intention to acknowledge suspicious emails primarily based on different elements, corresponding to grammatical errors and URLs that don’t correlate with the e-mail physique and anchor textual content or with the person’s anticipated vacation spot.
As soon as the person lands on the credential harvesting web page, a legitimate-looking immediate will ask the person for his or her e-mail deal with. These phishing kits conduct a request to an API that validates the e-mail. If the e-mail is legitimate, the phish will immediate for a password on the credential harvesting web page. The credential-harvesting URLs (in contrast to the redirect URLs embedded within the emails) are simply identifiable by the URL patterns proven earlier in Desk 1, and safety groups can try to dam this site visitors.
Outlook
Though Cofense Intelligence has recognized patterns and traits that lead us to categorize these phishing threats as an “exercise set”, it stays unclear whether or not this exercise is being carried out by a number of risk actors (probably present or former “Caffeine” prospects) utilizing the identical instruments or by a single actor (probably MRxC0DER himself). What is obvious, nonetheless, is that the phishing emails inside this exercise set are usually reaching the inboxes of enterprise e-mail customers, and that patterns inside the set usually change, making steady monitoring tougher. Exercise following noticed patterns peaked in March 2023, and fell over the course of April and Might, in live performance with the adoption of the latest sample (involving “LOG” strings). The usage of all different patterns was concurrently discontinued, offering restricted indication that the exercise is carried out by a single actor or coordinated group. Nevertheless, these observations might not characterize the total extent of the exercise, as there could also be different new, unobserved patterns changing the outdated exercise.
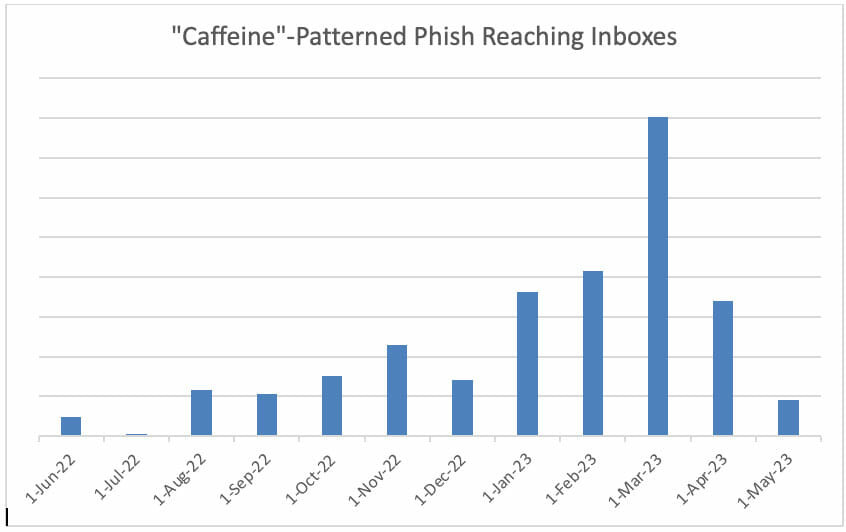
Determine 5: Quantity of Distinctive Phishing URLs Following “Caffeine” Area Patterns and Noticed Reaching Enterprise Inboxes
