A important safety flaw within the Bricks theme for WordPress is being actively exploited by risk actors to run arbitrary PHP code on prone installations.
The flaw, tracked as CVE-2024-25600 (CVSS rating: 9.8), allows unauthenticated attackers to attain distant code execution. It impacts all variations of the Bricks as much as and together with 1.9.6.
It has been addressed by the theme builders in model 1.9.6.1 launched on February 13, 2024, merely days after WordPress safety supplier Snicco reported the flaw on February 10.
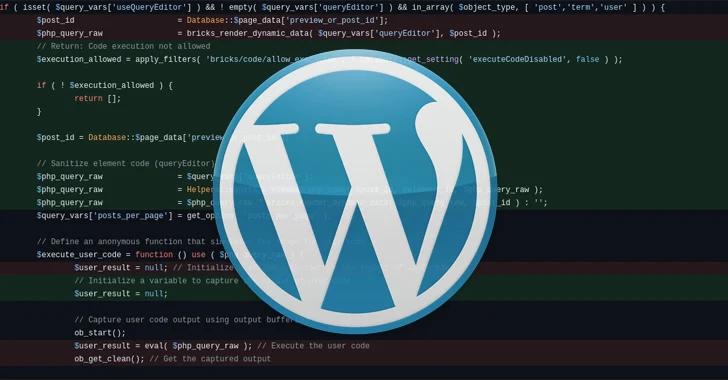
Whereas a proof-of-concept (PoC) exploit has not been launched, technical particulars have been launched by each Snicco and Patchstack, noting that the underlying weak code exists within the prepare_query_vars_from_settings() perform.
Particularly, it considerations the usage of safety tokens known as “nonces” for verifying permissions, which may then be used to cross arbitrary instructions for execution, successfully permitting a risk actor to grab management of a focused web site.
The nonce worth is publicly out there on the frontend of a WordPress web site, Patchstack stated, including there are not any satisfactory position checks utilized.
“Nonces ought to by no means be relied on for authentication, authorization, or entry management,” WordPress cautions in its documentation. “Shield your features utilizing current_user_can(), and at all times assume nonces will be compromised.”
WordPress safety firm Wordfence stated it detected over three dozen assault makes an attempt exploiting the flaw as of February 19, 2024. Exploitation makes an attempt are stated to have commenced on February 14, a day after public disclosure.
A majority of the assaults are from the next IP addresses –
- 200.251.23[.]57
- 92.118.170[.]216
- 103.187.5[.]128
- 149.202.55[.]79
- 5.252.118[.]211
- 91.108.240[.]52
Bricks is estimated to have round 25,000 at the moment energetic installations. Customers of the plugin are really useful to use the most recent patches to mitigate potential threats.