What’s occurred?
Researchers at Irregular have found the most recent evolution in call-back phishing campaigns.
Name-back phishing?
Conventional phishing emails may include a malicious hyperlink or attachment, and lure recipients into clicking on them by way of social engineering methods.
Name-back phishing dupes unsuspecting victims into telephoning a fraudulent name centre, the place they’ll communicate to an precise human being – who will then trick them into downloading and operating malware, offering malicious hackers with distant entry to their PC.
How would I be tricked into calling a bogus name centre?
It is in all probability simpler than you think about. Chances are you’ll know the actual web site addresses of companies like PayPal, Norton, GeekSquad, or Disney+, however have you learnt the telephone quantity for his or her help desk?
So all a malicious hacker has to do is ship me an e mail from a service I take advantage of, giving me a compelling motive to name them…
…and perhaps you’ll simply name the quantity within the e mail.
Here is an instance the place a fraudulent e mail claiming to return from PayPal claims that Netflix has charged you virtually $500. Should you do not recognise the transaction, you are invited to name a help quantity.
Okay, I can see how which may work on some individuals. However absolutely I might simply take a look at the e-mail headers and decide it is not likely from the corporate it claims to be from.
Properly sure, you may… in the event you’re nerdy sufficient to examine your emails with that a lot dedication. However most individuals would not ever trouble doing that.
And moreover, the most recent assaults are exploiting Google Types in a quite ingenious method to make their call-back phishing emails much more plausible.
Ingenious?
I believe so.
Here is what seems to be occurring behind the scenes within the newest BazarCall (also called BazaCall) assaults seen by Irregular’s safety researchers.
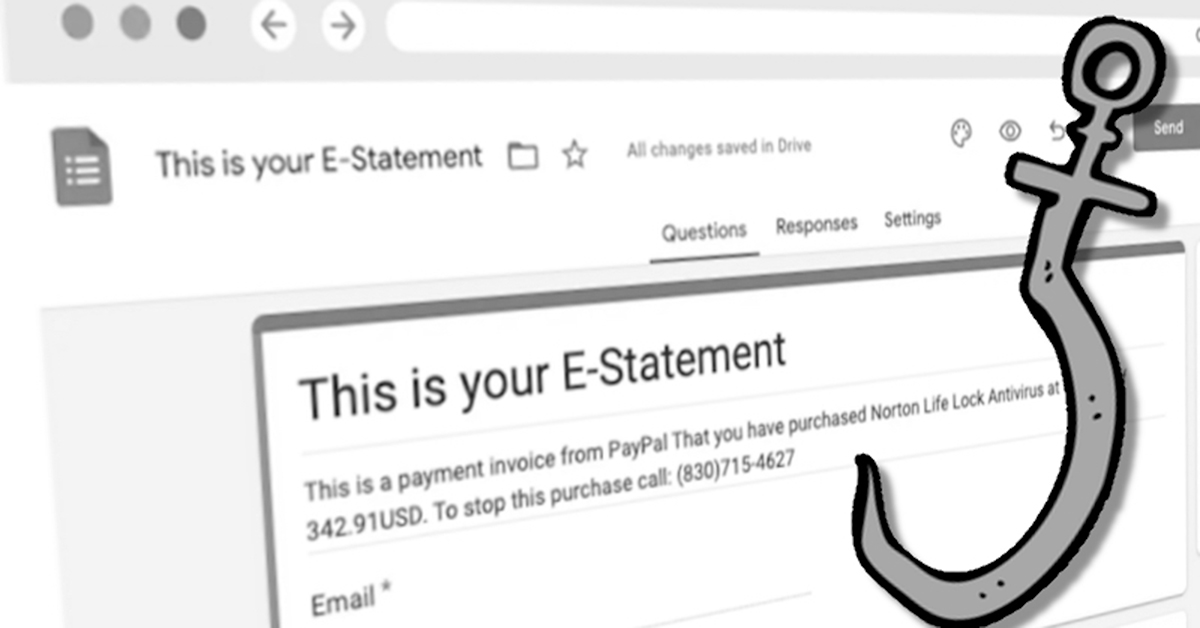
Step one is that the attackers creates a bogus assertion in Google Types, containing thanks for fee, and telling the reader to name a quantity in the event that they want to cease the acquisition.
That is your E-Assertion It is a fee bill from PayPal That you’ve bought Norton Life Lock Antivirus at the price of 342.91USD. To cease this buy name: (830)715-4627
Subsequent, the attacker modifications the shape’s settings to mechanically ship a replica of the finished type to any e mail deal with entered into the shape.
Then, and that is the place issues actually start to get intelligent, the attacker sends an invite to finish the shape to themselves, to not their meant sufferer.
So, the attacker receives the invitation to fill out the shape – and once they full it, they enter their meant sufferer’s e mail deal with into the shape, not their very own.
Ah! So, the sufferer receives the assertion, telling them to name a quantity in the event that they wish to dispute the fees.
Proper!
However I do not see how that is any higher for the attacker than simply sending the sufferer a call-back phishing e mail instantly. Why fiddle with Google Types?
The attackers are profiting from the truth that the emails are being despatched out instantly by Google Types (from the google.com area). It is a longtime reliable area that helps to make the e-mail look extra reliable and is much less more likely to be intercepted en route by email-filtering options.
That is actually sneaky.
Is not it? And that is why companies and people must be on their guard – and suppose twice earlier than calling buyer help name centres. Are you certain you are calling an actual help centre, or might or not it’s an operation run by cybercriminals?
Editor’s Notice: The opinions expressed on this visitor creator article are solely these of the contributor and don’t essentially replicate these of Tripwire