Apple launched a brand new iMessage safety function yesterday in beta known as Contact Key Verification. We realized the fundamentals of the way it works yesterday however now Apple has printed technical particulars of how the next-level iMessage safety function operates – together with a singular resolution to an issue that different messaging companies face.
The brand new iMessage safety function protects in opposition to a risk that hasn’t been seen within the wild but, however Apple has constructed a sturdy protection to assist ensure it stays that method.
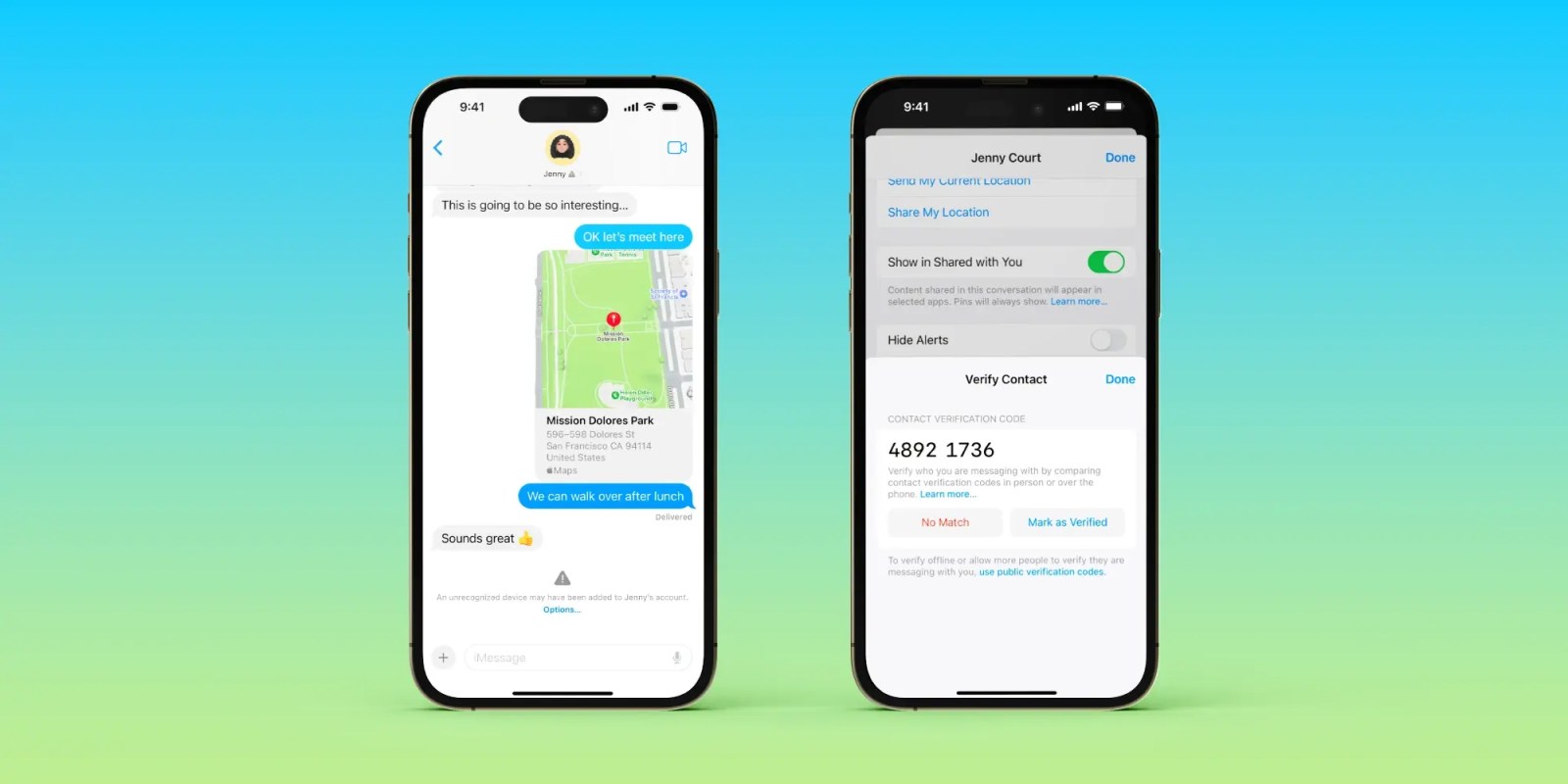
When enabled, the opt-in Contact Key Verification offers computerized alerts if the iMessage key distribution companies return system keys that haven’t been verified (e.g. if an unrecognized system has been added to an iMessage account).
And much more safety is accessible through the use of CKV in particular person, on FaceTime, or by way of one other safe technique like one other cellphone name.
Now Apple has shared in-depth particulars on how the brand new iMessage safety function works on its Safety Analysis weblog.
Right here’s a quick historical past of the safety features Apple has carried out with iMessage through the years:
Apple’s iMessage was the primary extensively obtainable messaging service to offer safe end-to-end encryption by default, ranging from when it launched in 2011. As safety threats have advanced, we’ve continued to strengthen iMessage by upgrading the protocol with stronger cryptographic primitives and including extra sturdy key administration that takes benefit of {hardware} protections supplied by the Safe Enclave. In iOS 14, we added BlastDoor, a sophisticated sandboxing mechanism that makes it vastly harder to assault the system with malicious content material within the Messages app. And in iOS 16 we launched Lockdown Mode, a groundbreaking safety for the very small variety of customers who face grave, focused threats to their digital safety — and which incorporates highly effective extra safety hardening within the Messages app when enabled. At the moment, we’d prefer to share an outline of our subsequent vital advance in iMessage safety: Contact Key Verification, a brand new function that’s designed to detect subtle assaults in opposition to iMessage servers and permit customers to confirm that they’re messaging solely with whom they intend.
Going into Contact Key Verification, right here’s what’s taking place:
iMessage makes use of end-to-end encryption to make sure that solely the sender and recipient of a message can learn it. To realize this robust safety property, every system in a consumer’s iMessage account generates its personal set of encryption keys, and the non-public keys are by no means exported to any exterior system. Usually, the supplier of an end-to-end encrypted messaging service operates a key listing service, which maps a consumer’s identifier — akin to an e-mail deal with or cellphone quantity — to public keys for every of their registered units. When Alice needs to ship Bob a message, Alice’s system contacts the important thing listing service and requests the record of public keys for Bob’s units. Alice’s system can then begin an encrypted dialog utilizing the encryption keys it obtained for Bob and ship him a message utilizing the transport specified by the protocol.
Whereas a key listing service like Apple’s Identification Listing Service (IDS) addresses key discovery, it’s a single level of failure within the safety mannequin. If a robust adversary have been to compromise a key listing service, the service might begin returning compromised keys — public keys for which the adversary controls the non-public keys — which might enable the adversary to intercept or passively monitor encrypted messages.
Some messaging techniques attempt to deal with this concern with an out-of-band, peer-to-peer verification step, the place two customers can confirm one another’s encryption keys utilizing lengthy verification numbers or QR codes. This resolution is helpful to substantiate that the important thing listing service returned the proper public keys for a consumer’s particular set of units at a selected cut-off date. Nonetheless, since each system generates and shops its personal keys, signing in to a messaging service on a brand new system generates a model new key; customers who depend on guide key verification would then must re-verify keys in each dialog to substantiate their conversations are safe, which is a difficult consumer expertise that doesn’t scale. The Sign messaging service, for instance, consists of the flexibility to switch an account to a brand new system in a method that avoids the necessity for guide key re-verification, but when Alice indicators in to a brand new system with out utilizing this mechanism, the individuals in all of her conversations are warned that their “security quantity with Alice has modified,” even when that they had by no means manually verified that security quantity with Alice.
Aiming to “each safe the important thing discovery protocol and supply an excellent consumer expertise in iMessage” Apple constructed Contact Key Discovery round six necessities:
- Safe a supply of fact for key materials and metadata in a method that can not be altered by unauthorized entities, together with the important thing listing service operator.
- Robotically confirm the important thing materials and metadata introduced by the important thing listing service in opposition to this supply of fact.
- Synchronize the supply of fact throughout all present and future units approved by a consumer for his or her account.
- Detect break up views between what the important thing listing service presents for a consumer’s personal identifiers and what it presents to friends (different dialog individuals) for that consumer.
- Scale to billions of customers and all of their conversations, together with one-to-one discussions and group chats.
- Notify customers solely when an sudden safety situation happens. Warnings should be uncommon and correct, fairly than the system counting on the consumer to note ongoing optimistic indicators of safety.
For extra in-depth particulars on Key Transparency, Automated verification, and extra, take a look at Apple’s full put up on the subject.
The corporate additionally highlights a “full technical walkthrough” for the function might be printed “quickly.”
FTC: We use earnings incomes auto affiliate hyperlinks. Extra.


