The Iranian state-sponsored risk actor often known as OilRig deployed three totally different downloader malware all through 2022 to take care of persistent entry to sufferer organizations positioned in Israel.
The three new downloaders have been named ODAgent, OilCheck, and OilBooster by Slovak cybersecurity firm ESET. The assaults additionally concerned using an up to date model of a recognized OilRig downloader dubbed SampleCheck5000 (or SC5k).
“These light-weight downloaders […] are notable for utilizing one in all a number of reputable cloud service APIs for [command-and-control] communication and information exfiltration: the Microsoft Graph OneDrive or Outlook APIs, and the Microsoft Workplace Alternate Internet Companies (EWS) API,” safety researchers Zuzana Hromcová and Adam Burgher mentioned in a report shared with The Hacker Information.
Through the use of well-known cloud service suppliers for command-and-control communication, the aim is to mix with genuine community visitors and canopy up the group’s assault infrastructure.
A few of the targets of the marketing campaign embody a corporation within the healthcare sector, a producing firm, and a neighborhood governmental group, amongst others. All of the victims are mentioned to have been beforehand focused by the risk actor.
Beat AI-Powered Threats with Zero Belief – Webinar for Safety Professionals
Conventional safety measures will not lower it in immediately’s world. It is time for Zero Belief Safety. Safe your information like by no means earlier than.
The precise preliminary entry vector used to compromise the targets is at the moment unclear and it is not recognized if the attackers managed to retain their foothold within the networks in order to deploy these downloaders at numerous factors of time in 2022.
OilRig, also referred to as APT34, Crambus, Cobalt Gypsy, Hazel Sandstorm (previously EUROPIUM), and Helix Kitten, is an Iranian cyber espionage group that is recognized to be lively since at the least 2014, utilizing a variety of malware at its disposal to focus on entities within the Center East.
This 12 months alone, the hacking crew has been noticed leveraging novel malware like MrPerfectionManager, PowerExchange, Photo voltaic, Mango, and Menorah.
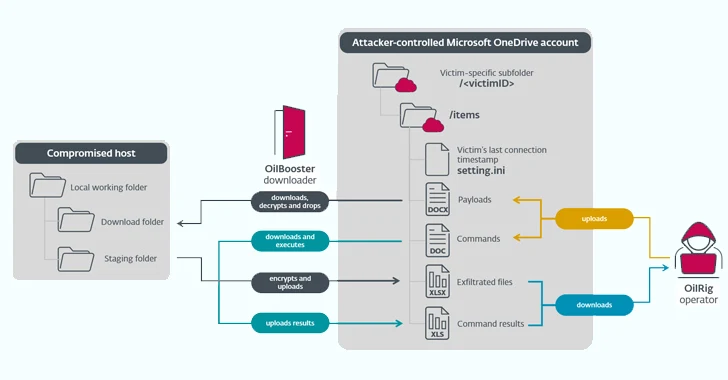
ODAgent, first detected in February 2022, is a C#/.NET downloader that makes use of Microsoft OneDrive API for command-and-control (C2) communications, permitting the risk actor to obtain and execute payloads, and exfiltrate staged information.
SampleCheck5000, however, is designed to work together with a shared Microsoft Alternate mail account to obtain and execute further OilRig instruments utilizing the Workplace Alternate Internet Companies (EWS) API.
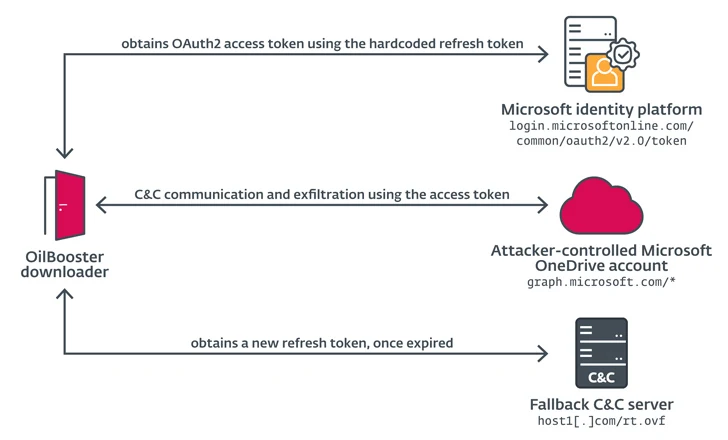
OilBooster, in the identical approach as ODAgent, makes use of Microsoft OneDrive API for C2, whereas OilCheck adopts the identical approach as SampleCheck5000 to extract instructions embedded in draft messages. However as an alternative of utilizing the EWS API, it leverages Microsoft Graph API for community communications.
OilBooster can also be much like OilCheck in that it employs the Microsoft Graph API to connect with a Microsoft Workplace 365 account. What’s totally different this time round is that the API is used to work together with an actor-controlled OneDrive account versus an Outlook account to be able to fetch instructions and payloads from victim-specific folders.
These instruments additionally share similarities with MrPerfectionManager and PowerExchange backdoors in the case of utilizing email-based C2 protocols to exfiltrate information, though within the case of the latter, the victimized group’s Alternate Server is used to ship messages to the attacker’s e-mail account.
“In all instances, the downloaders use a shared (e-mail or cloud storage) OilRig-operated account to change messages with the OilRig operators; the identical account is often shared by a number of victims,” the researchers defined.
“The downloaders entry this account to obtain instructions and extra payloads staged by the operators, and to add command output and staged information.”