A financially motivated menace actor referred to as UNC4990 is leveraging weaponized USB units as an preliminary an infection vector to focus on organizations in Italy.
Google-owned Mandiant stated the assaults single out a number of industries, together with well being, transportation, building, and logistics.
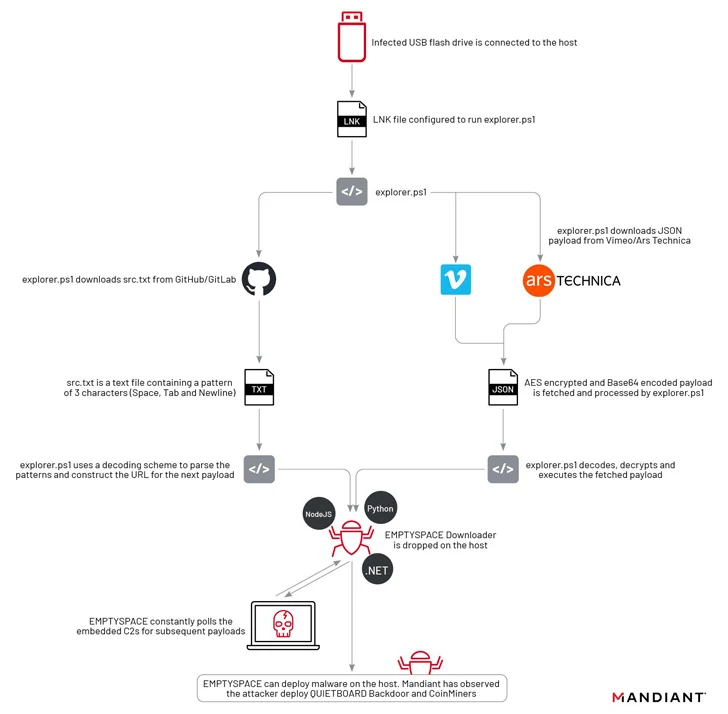
“UNC4990 operations typically contain widespread USB an infection adopted by the deployment of the EMPTYSPACE downloader,” the corporate stated in a Tuesday report.
“Throughout these operations, the cluster depends on third-party web sites corresponding to GitHub, Vimeo, and Ars Technica to host encoded further phases, which it downloads and decodes through PowerShell early within the execution chain.”
UNC4990, lively since late 2020, is assessed to be working out of Italy primarily based on the intensive use of Italian infrastructure for command-and-control (C2) functions.
It is presently not recognized if UNC4990 capabilities solely as an preliminary entry facilitator for different actors. The top objective of the menace actor can also be not clear, though in a single occasion an open-source cryptocurrency miner is claimed to have been deployed after months of beaconing exercise.
Particulars of the marketing campaign had been beforehand documented by Fortgale and Yoroi in early December 2023, with the previous monitoring the adversary underneath the identify Nebula Dealer.
The an infection begins when a sufferer double-clicks on a malicious LNK shortcut file on a detachable USB system, resulting in the execution of a PowerShell script that is accountable for downloading EMPTYSPACE (aka BrokerLoader or Vetta Loader) from a distant server through one other intermedia PowerShell script hosted on Vimeo.
Yoroi stated it recognized 4 totally different variants of EMPTYSPACE written in Golang, .NET, Node.js, and Python, which subsequently acts as a conduit for fetching next-stage payloads over HTTP from the C2 server, together with a backdoor dubbed QUIETBOARD.
A notable side of this part is the usage of common websites like Ars Technica, GitHub, GitLab, and Vimeo for internet hosting the malicious payload.
“The content material hosted on these companies posed no direct threat for the on a regular basis customers of those companies, because the content material hosted in isolation was fully benign,” Mandiant researchers stated. “Anybody who might have inadvertently clicked or considered this content material up to now was not susceptible to being compromised.”
QUIETBOARD, alternatively, is a Python-based backdoor with a variety of options that permit it to execute arbitrary instructions, alter crypto pockets addresses copied to clipboard to redirect fund transfers to wallets underneath their management, propagate the malware to detachable drives, take screenshots, and collect system info.
Moreover, the backdoor is able to modular growth and operating unbiased Python modules like coin miners in addition to dynamically fetching and executing Python code from the C2 server.
“The evaluation of each EMPTYSPACE and QUIETBOARD suggests how the menace actors took a modular method in growing their toolset,” Mandiant stated.
“The usage of a number of programming languages to create totally different variations of the EMPTYSPACE downloader and the URL change when the Vimeo video was taken down present a predisposition for experimentation and adaptableness on the menace actors’ aspect.”