Risk actors are leveraging a just lately disclosed safety flaw impacting Ivanti Join Safe, Coverage Safe, and ZTA gateways to deploy a backdoor codenamed DSLog on prone gadgets.
That is in accordance with findings from Orange Cyberdefense, which mentioned it noticed the exploitation of CVE-2024-21893 inside hours of the general public launch of the proof-the-concept (PoC) code.
CVE-2024-21893, which was disclosed by Ivanti late final month alongside CVE-2024-21888, refers to a server-side request forgery (SSRF) vulnerability within the SAML module that, if efficiently exploited, might allow entry to in any other case restricted sources sans any authentication.
The Utah-based firm has since acknowledged that the flaw has restricted focused assaults, though the precise scale of the compromises is unclear.
Then, final week, the Shadowserver Basis revealed a surge in exploitation makes an attempt concentrating on the vulnerability originating from over 170 distinctive IP addresses, shortly after each Rapid7 and AssetNote shared extra technical specifics.
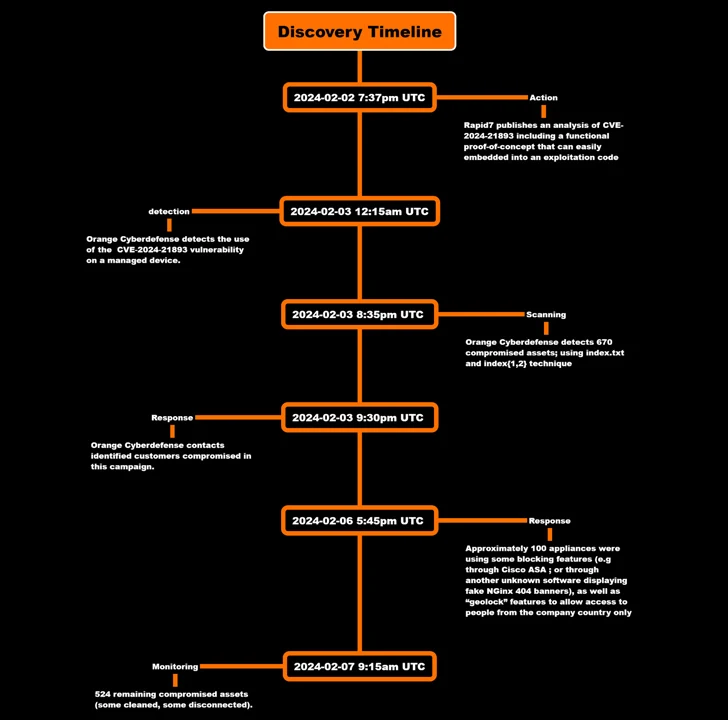
Orange Cyberdefense’s newest evaluation exhibits that compromises have been detected as early as February 3, with the assault concentrating on an unnamed buyer to inject a backdoor that grants persistent distant entry.
“The backdoor is inserted into an current Perl file referred to as ‘DSLog.pm,'” the corporate mentioned, highlighting an ongoing sample during which current professional elements – on this case, a logging module – are modified so as to add the malicious code.
DSLog, the implant, comes fitted with its personal tips to hamper evaluation and detection, together with embedding a novel hash per equipment, thereby making it unattainable to make use of the hash to contact the identical backdoor on one other machine.
The identical hash worth is equipped by the attackers to the Person-Agent header area in an HTTP request to the equipment to permit the malware to extract the command to be executed from a question parameter referred to as “cdi.” The decoded instruction is then run as the basis person.
“The online shell doesn’t return standing/code when attempting to contact it,” Orange Cyberdefense mentioned. “There is no such thing as a recognized approach to detect it instantly.”
It additional noticed proof of menace actors erasing “.entry” logs on “a number of” home equipment in a bid to cowl up the forensic path and fly below the radar.
However by checking the artifacts that have been created when triggering the SSRF vulnerability, the corporate mentioned it was in a position to detect 670 compromised belongings throughout an preliminary scan on February 3, a quantity that has dropped to 524 as of February 7.
In mild of the continued exploitation of Ivanti gadgets, it is extremely really helpful that “all clients manufacturing facility reset their equipment earlier than making use of the patch to stop the menace actor from gaining improve persistence in your surroundings.”