Microsoft Entra is just not solely the identification system for customers; it’s additionally the identification and entry administration (IAM) system for Azure-based providers, all inner infrastructure providers at Microsoft, and our clients’ workload identities. This is the reason our 99.99% service-level promise extends to workload identification authentication, and why we proceed to enhance our service’s resilience by means of a multilayered strategy that features the backup authentication system.
In 2021, we launched the backup authentication system, as an industry-first innovation that routinely and transparently handles authentications for supported workloads when the first Microsoft Entra ID service is degraded or unavailable. Via 2022 and 2023, we continued to broaden the protection of the backup service throughout clouds and software sorts.
At the moment, we’ll construct on our resilience blogpost sequence by going additional in sharing how workload identities acquire resilience from the regionally remoted authentication endpoints in addition to from the backup authentication system. We’ll discover two complementary strategies that greatest match our regional-global infrastructure. One instance of workload identification authentication is when an Azure digital machine (VM) authenticates its identification to Azure Storage. One other instance is when one among our clients’ workloads authenticates to software programming interfaces (APIs).
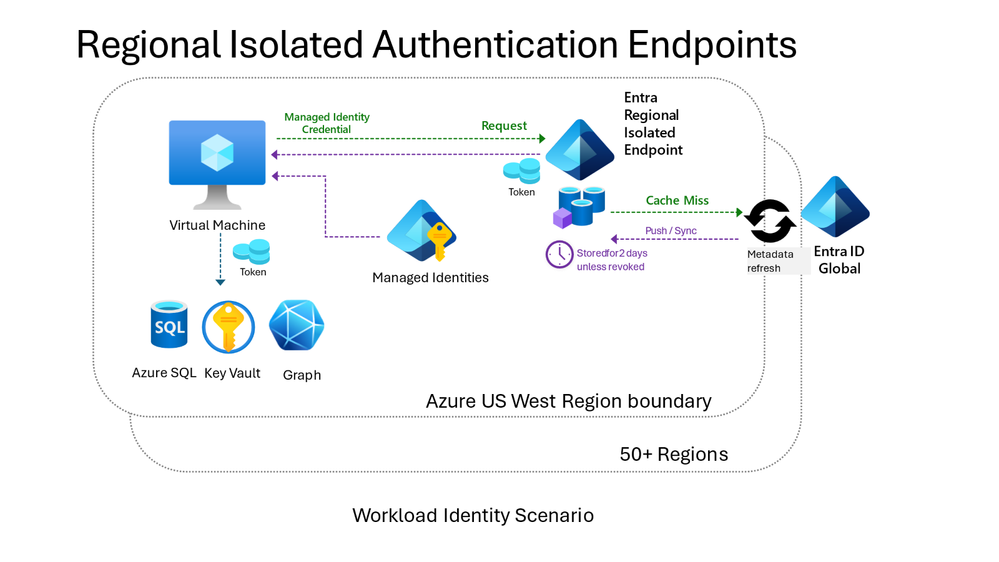
Regionally remoted authentication endpoints
Regionally remoted authentication endpoints present region-isolated authentication providers to an Azure area. All continuously used identities will authenticate efficiently with out dependencies on different Azure areas. Basically, they’re the first endpoints for Azure infrastructure providers in addition to the first endpoints for managed identities in Azure (Managed identities for Azure assets – Microsoft Entra ID | Microsoft Study). Managed identities assist stop out-of-region failures by consolidating service dependencies, and enhancing resilience by dealing with certificates expiry, rotation, and belief.
This layer of safety and isolation doesn’t want any configuration adjustments from Azure clients. Key Azure infrastructure providers have already adopted it, and it’s built-in with the managed identities service to guard the client workloads that depend upon it.
How regionally remoted authentication endpoints work
Every Azure area is assigned a novel endpoint for workload identification authentication. The area is served by a regionally collocated, particular occasion of Microsoft Entra ID. The regional occasion depends on caching metadata (for instance, listing information that’s wanted to challenge tokens domestically) to reply effectively and resiliently to the workload identification’s authentication requests. This light-weight design reduces dependencies on different providers and improves resilience by permitting the whole authentication to be accomplished inside a single area. Information within the native cache is proactively refreshed.
The regional service is determined by Microsoft Entra ID’s international service to replace and refill caches when it lacks the information it wants (a cache miss) or when it detects a change within the safety posture for a supported service. If the regional service experiences an outage, requests are served seamlessly by Microsoft Entra ID’s international service, making the regional service interruption invisible to the shoppers.
Performant, resilient, and extensively accessible
The service has confirmed itself since 2020 and now serves six billion requests per day throughout the globe. The regional endpoints, working with international providers, exceed 99.99% SLA. The resilience of Azure infrastructure is additional protected by workload-side caches saved by Azure consumer SDKs. Collectively, the regional and international providers have managed to make most service degradations undetectable by dependent infrastructure providers. Submit-incident restoration is dealt with routinely. Regional isolation is supported by public and all Sovereign Clouds.
Infrastructure authentication requests are processed by the identical Azure datacenter that hosts the workloads together with their co-located dependencies. Which means endpoints which are remoted to a area additionally profit from efficiency benefits.
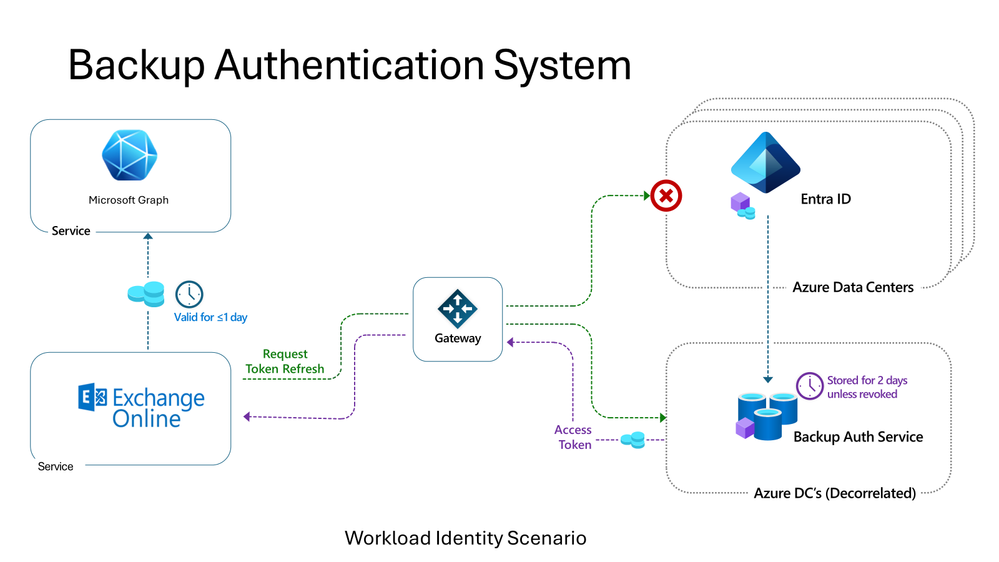
Backup authentication system to cowl workload identities for infrastructure authentication
For workload identification authentication that doesn’t depend upon managed identities, we’ll depend on the backup authentication system so as to add fault-tolerant resilience. In our blogpost from November 2021, we defined the strategy for consumer authentication which has been usually accessible for a while. The system operates within the Microsoft cloud however on separate and decorrelated programs and community paths from the first Microsoft Entra ID system. Which means it will possibly proceed to function in case of service, community, or capability points throughout many Microsoft Entra ID and dependent Azure providers. We at the moment are making use of that profitable strategy to workload identities.
Backup protection of workload identities is at present rolling out systematically throughout Microsoft, beginning with Microsoft 365’s largest inner infrastructure providers within the first half of 2024. Microsoft Entra ID buyer workload identities’ protection will comply with within the second half of 2025.
Defending your individual workloads
The advantages of each regionally remoted endpoints and the backup authentication system are natively constructed into our platform. To additional optimize the advantages of present and future investments in resilience and safety, we encourage builders to make use of the Microsoft Authentication Library (MSAL) and leverage managed identities every time doable.
What’s subsequent?
We need to guarantee our clients that our 99.99% uptime assure stays in place, together with our ongoing efforts to broaden our backup protection system and enhance our automated backup protection to incorporate all infrastructure authentication—even for third-party builders—within the subsequent yr. We’ll ensure to maintain you up to date on our progress, together with deliberate enhancements to our system capability, efficiency, and protection throughout all clouds.
Thanks,
Nadim Abdo
CVP, Microsoft Identification Engineering
Study extra about Microsoft Entra: