The Midnight Blizzard and Cloudflare-Atlassian cybersecurity incidents raised alarms concerning the vulnerabilities inherent in main SaaS platforms. These incidents illustrate the stakes concerned in SaaS breaches — safeguarding the integrity of SaaS apps and their delicate knowledge is crucial however will not be straightforward. Frequent risk vectors akin to refined spear-phishing, misconfigurations and vulnerabilities in third-party app integrations display the advanced safety challenges going through IT techniques.
Within the case of Midnight Blizzard, password spraying in opposition to a check setting was the preliminary assault vector. For Cloudflare-Atlassian, risk actors initiated the assault by way of compromised OAuth tokens from a previous breach at Okta, a SaaS id safety supplier.
What Precisely Occurred?
Microsoft Midnight Blizzard Breach
Microsoft was focused by the Russian “Midnight Blizzard” hackers (often known as Nobelium, APT29, or Cozy Bear) who’re linked to the SVR, the Kremlin’s overseas intelligence service unit.
Within the Microsoft breach, the risk actors:
- Used a password spray technique on a legacy account and historic check accounts that didn’t have multi-factor authentication (MFA) enabled. In line with Microsoft, the risk actors “[used] a low variety of makes an attempt to evade detection and keep away from account blocks based mostly on the amount of failures.”
- Leveraged the compromised legacy account as an preliminary entry level to then hijack a legacy check OAuth app. This legacy OAuth app had high-level permissions to entry Microsoft’s company setting.
- Created malicious OAuth apps by exploiting the legacy OAuth app’s permissions. As a result of the risk actors managed the legacy OAuth app, they might preserve entry to the functions even when they misplaced entry to the initially compromised account.
- Granted admin Trade permissions and admin credentials to themselves.
- Escalated privileges from OAuth to a brand new consumer, which they managed.
- Consented to the malicious OAuth functions utilizing their newly created consumer account.
- Escalated the legacy utility’s entry additional by granting it full entry to M365 Trade On-line mailboxes. With this entry, Midnight Blizzard might view M365 e mail accounts belonging to senior employees members and exfiltrate company emails and attachments.
 |
| Recreation of illustration by Amitai Cohen |
Cloudflare-Atlassian Breach
On Thanksgiving Day, November 23, 2023, Cloudflare’s Atlassian techniques had been additionally compromised by a nation-state assault.
- This breach, which began on November 15, 2023, was made doable by means of using compromised credentials that had not been modified following a earlier breach at Okta in October 2023.
- Attackers accessed Cloudflare’s inside wiki and bug database, enabling them to view 120 code repositories in Cloudflare’s Atlassian occasion.
- 76 supply code repositories associated to key operational applied sciences had been probably exfiltrated.
- Cloudflare detected the risk actor on November 23 as a result of the risk actor linked a Smartsheet service account to an admin group in Atlassian.
Can Your Safety Group Monitor Third Social gathering Apps? 60% of Groups Cannot
Suppose your SaaS safety is top-notch? Appomni surveyed over 600 world safety practitioners, and 79% of execs felt the identical – but they confronted cybersecurity incidents! Dive into the insights of the AppOmni 2023 Report.
Risk Actors More and more Goal SaaS
These breaches are a part of a broader sample of nation-state actors focusing on SaaS service suppliers, together with however not restricted to espionage and intelligence gathering. Midnight Blizzard beforehand engaged in vital cyber operations, together with the 2021 SolarWinds assault.
These incidents underscore the significance of steady monitoring of your SaaS environments and the continuing danger posed by refined cyber adversaries focusing on crucial infrastructure and operational tech stack. Additionally they spotlight vital vulnerabilities associated to SaaS id administration and the need for stringent Third-party app danger administration practices.
Attackers use widespread techniques, methods and procedures (TTPs) to breach SaaS suppliers by means of the next kill chain:
- Preliminary entry: Password spray, hijacking OAuth
- Persistence: Impersonates admin, creates additional OAuth
- Protection Evasion: Extremely privileged OAuth, no MFA
- Lateral Motion: Broader compromise of linked apps
- Knowledge Exfiltration: Seize privileged and delicate knowledge out of apps
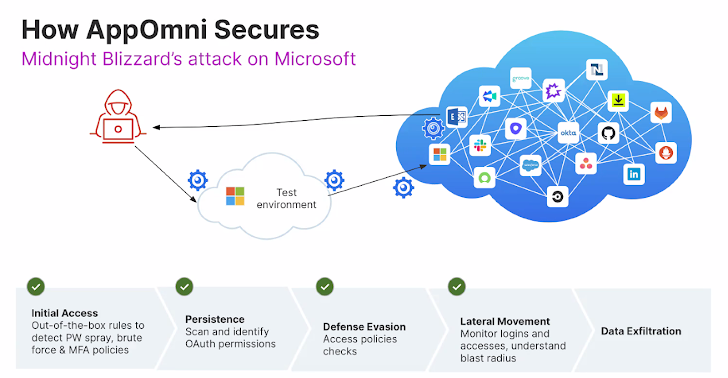
Breaking the SaaS Kill Chain
One efficient technique to break the kill chain early is with steady monitoring, granular coverage enforcement, and proactive lifecycle administration over your SaaS environments. A SaaS Safety Posture Administration (SSPM) platform like AppOmni may also help with detecting and alerting on:
- Preliminary Entry: Out-of-the-box guidelines to detect credential compromise, together with password spraying, brute pressure assaults, and unenforced MFA insurance policies
- Persistence: Scan and determine OAuth permissions and detect OAuth hijacking
- Protection Evasion: Entry coverage checks, detect if a brand new id supplier (IdP) is created, detect permission adjustments.
- Lateral Motion: Monitor logins and privileged entry, detect poisonous mixtures, and perceive the blast radius of a probably compromised account
Observe: This expertly contributed article is written by Beverly Nevalga, AppOmni.