The Roaming Mantis risk group distributes a widely known Android malware household known as “MoqHao.” This malware household has been beforehand reported to be concentrating on Asian international locations reminiscent of Korea and Japan. Although the distribution methodology stays the identical, the brand new variants use a really harmful approach.
Sometimes, the MoqHao malware requires person interplay to put in and launch the app. Nonetheless, the brand new variant of this malware doesn’t require any execution.
Android is at the moment protected with Google Play Shield, which is the default app scanner that warns customers or blocks functions that comprise malicious habits.
Forestall malware from infecting your community on the supply stage by intercepting malicious recordsdata in transit from their supply to the goal gadget’s net browser..
Android MoqHao Malware
As a part of the distribution, the risk actors ship a malicious phishing SMS message to the customers, which is able to comprise a malicious shortened hyperlink. The gadget downloads the malicious software as soon as the person clicks on the hyperlink.
This new variant has a number of totally different behaviors when in comparison with the earlier variants of this malware, because it launches routinely after set up with out person interplay.
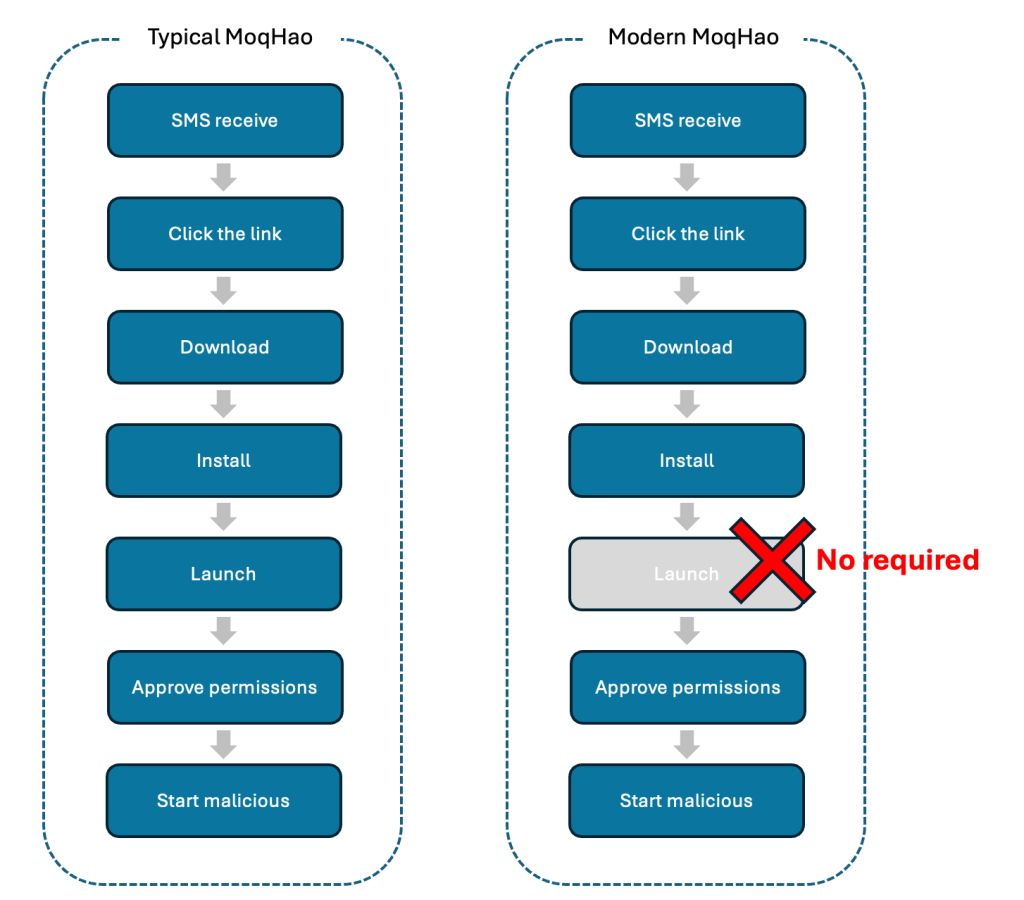
Android safety checks an put in software and the precise worth utilized by that software, which have to be distinctive. The risk actors are abusing this specific function to auto-executing the applying with out person interplay.
Furthermore, the risk actors additionally use social engineering strategies to set this malicious app as a default SMS app. Additional investigations additionally revealed that the malware has been prolonged with targets, together with international locations like South Korea, France, Germany, and India.
Moreover, this variant connects with a C2 server by WebSocket. This new malware has been added with a number of different instructions for checking SIM state, sending SMS messages to different contacts and C2 servers, setting Sound/Vibrate/Silent mode, and varied different functions.
| Command | Description |
| getSmsKW | Ship entire contacts to the C2 server |
| sendSms | Ship SMS messages to somebody |
| setWifi | Allow/disable Wifi |
| gcont | Set Vibrate/Silent mode in accordance with the SDK model |
| lock | Retailer Boolean worth in “lock” key in SharedPreferences |
| bc | Test SIM state |
| setForward | Retailer String worth in “fs” key in SharedPreferences |
| getForward | Get String worth in “fs” key in SharedPreferences |
| hasPkg | Test the precise package deal put in on the gadget |
| setRingerMode | Set Sound/Vibrate/Silent mode |
| setRecEnable | Emulate the House button click on |
| reqState | Ship gadget data (Community, Energy, MAC, Permission) to C2 server |
| showHome | Name a particular quantity with a Silent mode |
| getnpki | Ship Korean Public Certificates (NPKI) to C2 server |
| http | Ship HTTP requests |
| name | Get the record of put in packages |
| get_apps | Ship all images to the C2 server |
| ping | Test C2 server standing |
| getPhoneState | Get distinctive data reminiscent of IMEI, SIM quantity, Android ID, and serial quantity |
| get_photo | Ship all images to C2 server |
McAfee supplies complete data in regards to the malware, together with particulars on its supply code, strategies used to deploy it, targets which have been affected by it, and different necessary insights.
Indicators of Compromise
| SHA256 | Utility Title | Package deal Title |
| 2576a166d3b18eafc2e35a7de3e5549419d10ce62e0eeb24bad5a1daaa257528 | chrome | gb.pi.xcxr.xd |
| 61b4cca67762a4cf31209056ea17b6fb212e175ca330015d804122ee6481688e | chrome | malmkb.zdbd.ivakf.lrhrgf |
| b044804cf731cd7dd79000b7c6abce7b642402b275c1eb25712607fc1e5e3d2b | chrome | vfqhqd.msk.xux.njs |
| bf102125a6fca5e96aed855b45bbed9aa0bc964198ce207f2e63a71487ad793a | chrome | hohoj.vlcwu.lm.ext |
| e72f46f15e50ce7cee5c4c0c5a5277e8be4bb3dd23d08ea79e1deacb8f004136 | chrome | enech.hg.rrfy.wrlpp |
| f6323f8d8cfa4b5053c65f8c1862a8e6844b35b260f61735b3cf8d19990fef42 | chrome | gqjoyp.cixq.zbh.llr |
Keep up to date on Cybersecurity information, Whitepapers, and Infographics. Comply with us on LinkedIn & Twitter.















