By Dylan Duncan
On February twenty first, 2024, Cofense Intelligence recognized a sophisticated phishing marketing campaign that focused the Oil and Fuel sector to ship Rhadamanthys Stealer, a sophisticated info stealer provided as Malware-as-a-Service (MaaS). The marketing campaign incorporates a number of complicated ways, methods, and procedures (TTPs) together with a singular car incident lure that spoofs the Federal Bureau of Transportation. This marketing campaign follows shut behind a number of updates to the Rhadamanthys MaaS in the marketplace place, and regulation enforcement’s takedown of the LockBit Ransomware group, one of the vital infamous Ransomware-as-a-Service in the marketplace. Because of the uniqueness of the marketing campaign and success price at which emails had been reaching targets, a Cofense Intelligence Flash Alert New MaaS InfoStealer Malware Marketing campaign Focusing on Oil & Fuel Sector was revealed together with an Energetic Menace Report.
Key Factors
- The phishing emails use a singular car incident lure and, in later phases of the an infection chain, spoof the Federal Bureau of Transportation in a PDF that mentions a major superb for the incident.
- TTPs on this marketing campaign observe go well with with these recognized to help in bypassing safe e-mail gateways (SEGs) and different layers of safety infrastructure which are in place to quarantine malicious emails.
- General, the aim of the marketing campaign is to contaminate customers with Rhadamanthys Stealer, a sophisticated MaaS that’s unusual within the phishing risk panorama.
- Based mostly on a report by Cyberint, Rhadamanthys Stealer acquired main updates (replace 5.0) earlier this 12 months that has led to improved stealing capabilities and evasion ways.
- This marketing campaign appeared inside days of the regulation enforcement takedown of the LockBit ransomware group. Whereas this could possibly be a coincidence, there have been stories of Rhadamanthys Stealer used within the supply of LockBit ransomware in 2023.
Phishing Marketing campaign Focusing on Oil & Fuel Sector
As of this report, the targets for this marketing campaign have primarily been within the Oil and Fuel sector. It’s not clear as to why this particular sector is, however the marketing campaign in its present kind could possibly be related in most sectors if risk actors determined to vary targets. Whereas the marketing campaign was actively sending emails, it was efficiently reaching targets at an alarming price. That is attributed to a mixture of generally used TTPs recognized to disrupt evaluation. By becoming a member of a number of TTPs, like trusted domains, a number of redirects, and clickable photos, risk actors can improve the possibilities that their emails will bypass the present e-mail safety requirements and attain targets. Determine 1 exhibits the an infection chain for this marketing campaign from the risk actor to the ultimate Rhadamanthys Stealer executable.

Determine 1: An infection chain of the phishing marketing campaign.
The marketing campaign begins with risk actors crafting a singular topic and physique for every e-mail with the general theme being the recipient’s car being concerned in an incident. The primary malicious indicator is a hyperlink embedded within the e-mail that abuses an open redirect, a vulnerability on a web site that enables risk actors to leverage a selected path on a official area to redirect victims to a malicious location. Open redirects on this marketing campaign are primarily hosted on official Google domains, particularly Google Maps and Google Photographs. The embedded hyperlink redirects to a URL shortener, a URL generated to scale back the scale of a URL but in addition assists in hiding the URL. The URL shortener acts as an extra layer of evasiveness on this marketing campaign, as a result of risk actors usually affiliate extra redirects within the an infection chain to have a greater probability of SEGs not recognizing the malicious intent of the e-mail, which does appear to be the case.
After the redirection, victims are taken to a clickable PDF file hosted on docptypefinder[.]data, a website registered on the identical day that this marketing campaign was first seen. The PDF, proven in Determine 4 later within the report, is a clickable picture that spoofed the Federal Bureau of Transportation and mentions a potential superb of $30,000 for the incident. Clicking on the picture downloads or prompts for the obtain of a ZIP Archive file. This file incorporates an executable that, when ran, unpacks and initiates Rhadamanthys Stealer. The malware instantly begins a reference to a command and management (C2) location that collects any stolen credentials, cryptocurrency wallets, or different delicate info.
Car Incident and Urgency Lures
As peculiar because it might sound to make use of car incidents as a phishing lure, the risk actor(s) right here put immense effort to make sure that their emails together with the an infection chain goal recipient’s feelings. Every e-mail physique and topic are each totally different than the subsequent, however they are often summarized by notifying an worker of a automotive incident by way of an employer notification, potential authorized actions, or perhaps a discover of contacting regulation enforcement. Determine 2 under, is an instance of one of many phishing emails seen on this marketing campaign. Whereas the topic and physique will differ from the opposite emails, the general theme nonetheless stands, on this case a notification by an employer that the worker had a automotive accident.
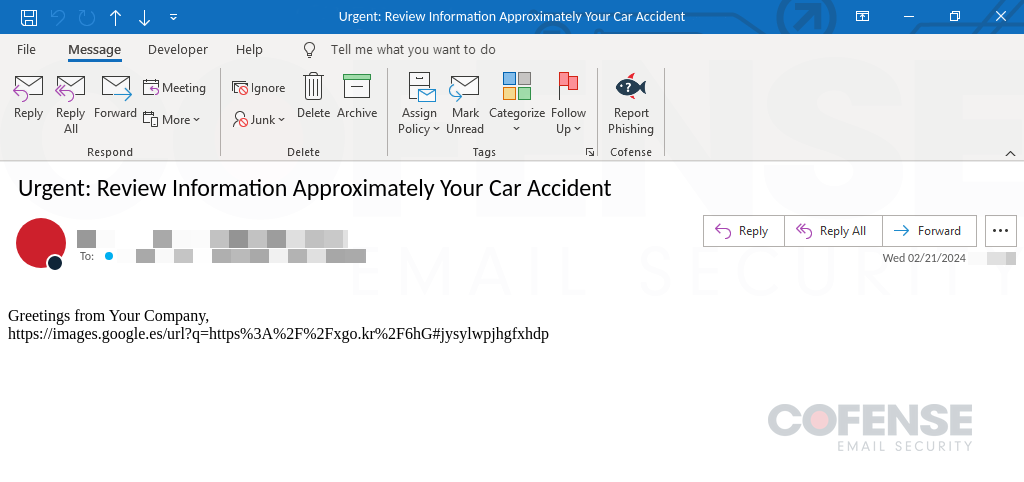
Determine 2: Car incident-themed phishing e-mail delivering Rhadamanthys Stealer.
Because of the quantity of emails and the seemingly randomness of every e-mail, Determine 3 was created to present an concept of all of the key phrases used all through the whole marketing campaign. Following according to the marketing campaign, in style phrases like incident, accident, car, car, automotive, carriage, and different key phrases are distinctly seen within the phrase cloud. Nevertheless, along with these, there are a number of filler phrases to spark recipient’s feelings like pressing, quick, required, notification, regarding, and essential. The chance stage of a phishing risk significantly will increase when the risk actors merge TTPs recognized to help in bypassing safety with well-crafted and socially engineered lures like this one.
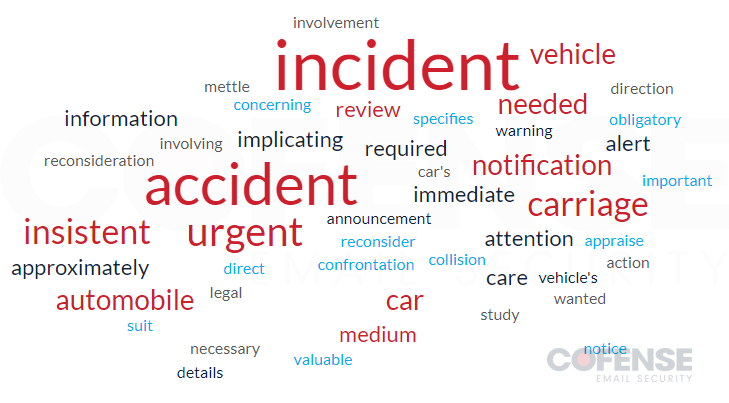
Determine 3: Phrase cloud of key phrases utilized in e-mail topics.
Desk 1 under is only a pattern of how numerous every e-mail topic is. The topics all observe the identical theme however look like randomly generated. The frequent theme consists of emotional filler phrases like pressing or consideration wanted, after which a message referencing the accident. Because of the quantity of the marketing campaign and uniqueness of every e-mail, it’s potential that risk actors included AI or ChatGPT to help within the totally different phrases.
Desk 1: Completely different topics used within the marketing campaign.
















