On Dec. 18, 2013, KrebsOnSecurity broke the information that U.S. retail large Goal was battling a wide-ranging pc intrusion that compromised greater than 40 million buyer fee playing cards over the earlier month. The malware used within the Goal breach included the textual content string “Rescator,” which additionally was the deal with chosen by the cybercriminal who was promoting the entire playing cards stolen from Goal clients. Ten years later, KrebsOnSecurity has uncovered new clues in regards to the real-life identification of Rescator.
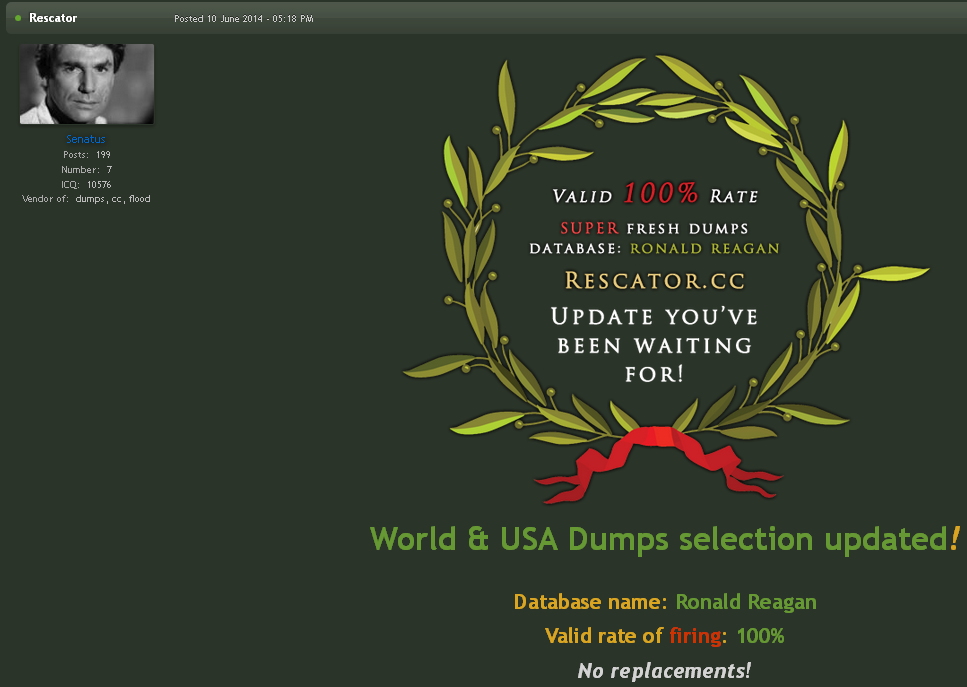
Rescator, promoting a brand new batch of playing cards stolen in a 2014 breach at P.F. Chang’s.
Shortly after breaking the Goal story, KrebsOnSecurity reported that Rescator seemed to be a hacker from Ukraine. Efforts to verify my reporting with that particular person ended once they declined to reply questions, and after I declined to simply accept a bribe of $10,000 to not run my story.
That reporting was based mostly on clues from an early Russian cybercrime discussion board through which a hacker named Rescator — utilizing the identical profile picture that Rescator was recognized to make use of on different boards — claimed to have initially been referred to as “Helkern,” the nickname chosen by the administrator of a cybercrime discussion board referred to as Darklife.
KrebsOnSecurity started revisiting the analysis into Rescator’s real-life identification in 2018, after the U.S. Division of Justice unsealed an indictment that named a distinct Ukrainian man as Helkern.
It could be useful to first recap why Rescator is considered so carefully tied to the Goal breach. For starters, the textual content string “Rescator” was present in among the malware used within the Goal breach. Investigators would later decide that a variant of the malware used within the Goal breach was utilized in 2014 to steal 56 million fee playing cards from House Depot clients. And as soon as once more, playing cards stolen within the House Depot breach have been offered completely at Rescator’s outlets.
On Nov. 25, 2013, two days earlier than Goal mentioned the breach formally started, Rescator could possibly be seen in instantaneous messages hiring one other discussion board member to confirm 400,000 fee playing cards that Rescator claimed have been freshly stolen.
By the primary week of December 2013, Rescator’s on-line retailer — rescator[.]la — was promoting greater than six million fee card information stolen from Goal clients. Previous to the Goal breach, Rescator had largely offered a lot smaller batches of stolen card and identification information, and the web site allowed cybercriminals to automate the sending of fraudulent wire transfers to cash mules based mostly in Lviv, Ukraine.
Lastly, there may be some honor amongst thieves, and within the market for stolen fee card information it’s thought-about poor kind to promote a batch of playing cards as “yours” if you’re merely reselling playing cards offered to you by a third-party card vendor or thief. When critical stolen fee card store distributors want to talk {that a} batch of playing cards is uniquely their handiwork or that of their rapid crew, they check with it as “our base.” And Rescator was fairly clear in his ads that these thousands and thousands of playing cards have been obtained firsthand.
FLASHBACK
The brand new clues about Rescator’s identification got here into focus once I revisited the reporting round an April 2013 story right here that recognized the writer of the OSX Flashback Trojan, an early Mac malware pressure that shortly unfold to greater than 650,000 Mac computer systems worldwide in 2012.
That story in regards to the Flashback writer was attainable as a result of a supply had obtained a Internet browser authentication cookie for a founding member of a Russian cybercrime discussion board referred to as BlackSEO. Anybody in possession of that cookie might then browse the invite-only BlackSEO discussion board and skim the consumer’s non-public messages with out having to log in.
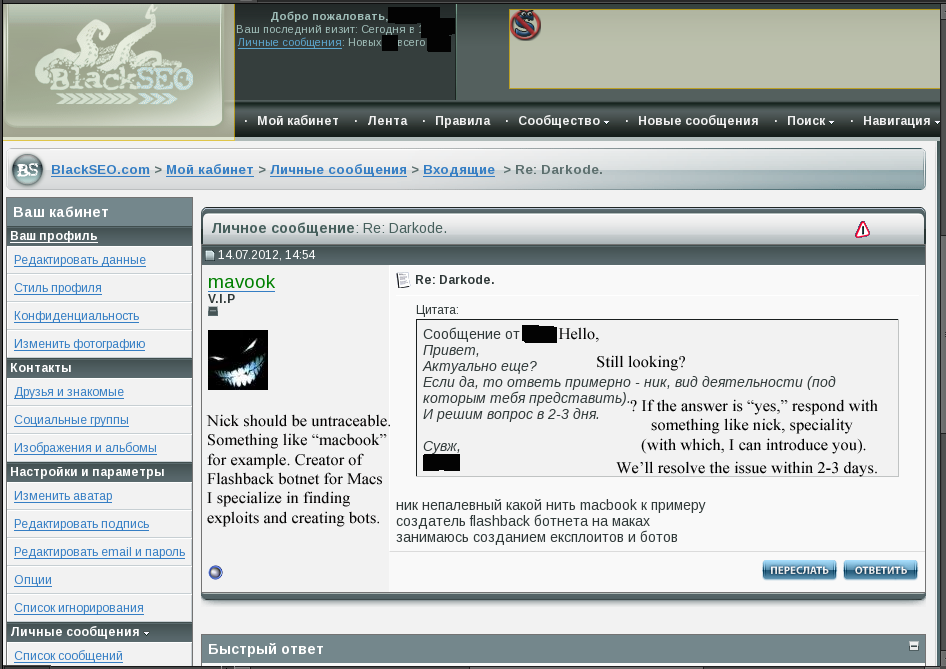
BlackSEO.com VIP member “Mavook” tells discussion board admin Ika in a non-public message that he’s the Flashback writer.
The legit proprietor of that BlackSEO consumer cookie glided by the nickname Ika, and Ika’s non-public messages on the discussion board confirmed he was shut pals with the Flashback writer. On the time, Ika additionally was the administrator of Pustota[.]pw — a closely-guarded Russian discussion board that counted amongst its members among the world’s most profitable and established spammers and malware writers.
For a few years, Ika held a key place at considered one of Russia’s largest Web service suppliers, and his (largely glowing) repute as a dependable supplier of internet hosting to the Russian cybercrime group gave him an encyclopedic data about almost each main participant in that scene on the time.
The story on the Flashback writer featured redacted screenshots that have been taken from Ika’s BlackSEO account (see picture above). The day after that story ran, Ika posted a farewell deal with to his mates, expressing shock and bewilderment over the obvious compromise of his BlackSEO account.
In a prolonged submit on April 4, 2013 titled “I DON’T UNDERSTAND ANYTHING,” Ika informed Pustota discussion board members he was so spooked by current occasions that he was closing the discussion board and quitting the cybercrime enterprise totally. Ika recounted how the Flashback story had come the identical week that rival cybercriminals tried to “dox” him (their dox named the incorrect particular person, however included a few of Ika’s extra guarded identities).
“It’s no secret that karma farted in my path,” Ika mentioned firstly of his submit. Unbeknownst to Ika on the time, his Pustota discussion board additionally had been fully hacked that week, and a duplicate of its database shared with this writer.
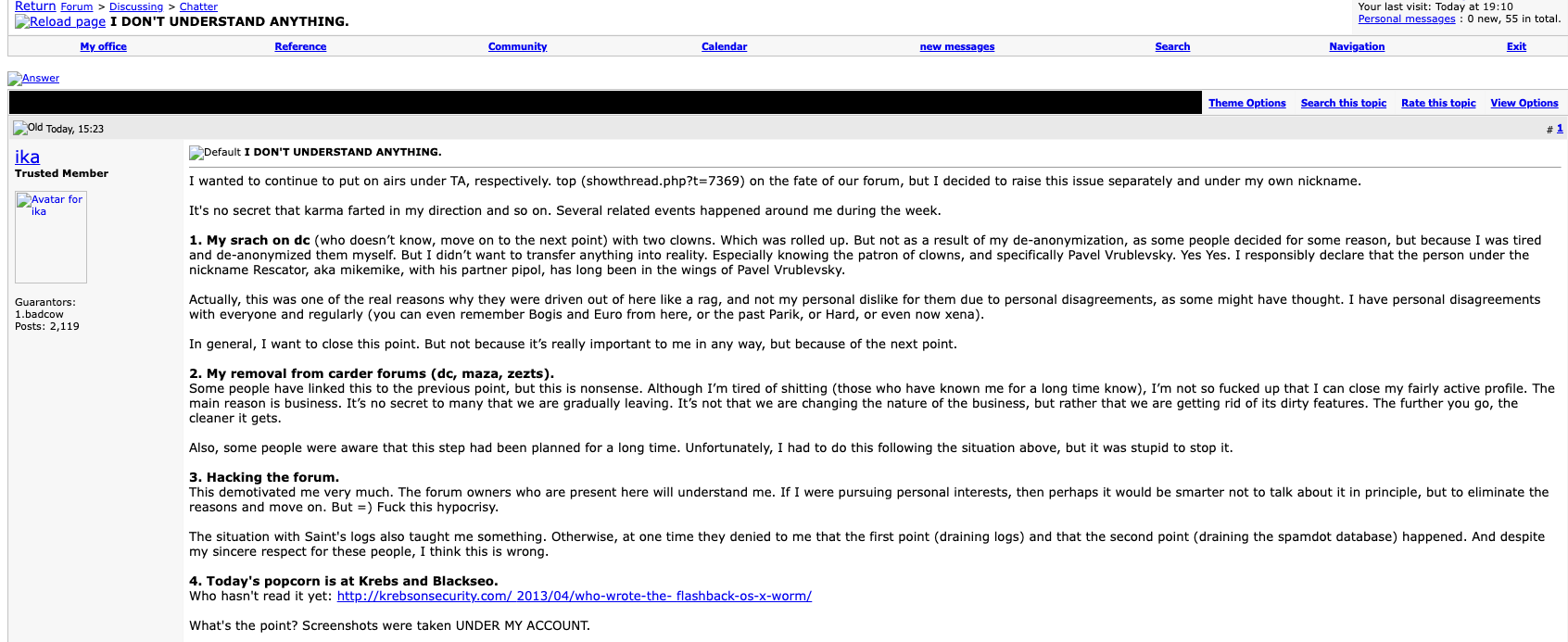
A Google translated model of the farewell submit from Ika, the administrator of Pustota, a Russian language cybercrime discussion board targeted on botnets and spam. Click on to enlarge.
Ika mentioned the 2 people who tried to dox him did so on an much more guarded Russian language discussion board — DirectConnection[.]ws, maybe essentially the most unique Russian cybercrime group ever created. New candidates of this discussion board needed to pay a non-refundable deposit, and obtain vouches by three established cybercriminals already on the discussion board. Even when one managed to steal (or guess) a consumer’s DirectConnection password, the login web page couldn’t be reached until the customer additionally possessed a particular browser certificates that the discussion board administrator gave solely to accepted members.
In no unsure phrases, Ika declared that Rescator glided by the nickname MikeMike on DirectConnection:
“I didn’t need to deliver any of this to actual life. Particularly since I knew the patron of the clowns – particularly Pavel Vrublevsky. Sure, I do state with confidence that the person with the nickname Rescator a.okay.a. MikeMike together with his associate Pipol have been Pavel Vrublevsky’s puppets for a very long time.”
Pavel Vrublevsky is a convicted cybercriminal who turned well-known because the CEO of the Russian e-payments firm ChronoPay, which specialised in facilitating on-line funds for quite a lot of “high-risk” companies, together with playing, pirated Mp3 recordsdata, rogue antivirus software program and “male enhancement” tablets.
As detailed in my 2014 e book Spam Nation, Vrublevsky not-so-secretly ran a pharmacy affiliate spam program referred to as Rx-Promotion, which paid spammers and virus writers to blast out tens of billions of junk emails promoting generic Viagra and managed prescription drugs like ache reduction drugs. A lot of my reporting on Vrublevsky’s cybercrime empire got here from a number of years price of inner ChronoPay emails and paperwork that have been leaked on-line in 2010 and 2011.

Pavel Vrublevsky’s former Fb profile photograph.
ZAXVATMIRA
In 2014, KrebsOnSecurity discovered from a trusted supply near the Goal breach investigation that the consumer MikeMike on DirectConnection — the identical account that Ika mentioned belonged to Rescator — used the e-mail deal with “zaxvatmira@gmail.com.”
On the time, KrebsOnSecurity couldn’t join that e-mail deal with to something or anybody. Nonetheless, a current search on zaxvatmira@gmail.com on the breach monitoring service Constella Intelligence returns only one consequence: An account created in November 2010 on the website searchengines[.]ru beneath the deal with “r-fac1.”
A search on “r-fac1” at cyber intelligence agency Intel 471 revealed that this consumer’s introductory submit on searchengines[.]ru marketed musictransferonline[.]com, an associates program that paid individuals to drive site visitors to websites that offered pirated music recordsdata for pennies apiece.
In line with leaked ChronoPay emails from 2010, this area was registered and paid for by ChronoPay. These missives additionally present that in August 2010 Vrublevsky licensed a fee of ~$1,200 for a multi-user license of an Intranet service referred to as MegaPlan.
ChronoPay used the MegaPlan service to assist handle the sprawling initiatives that Vrublevsky referred to internally as their “black” fee processing operations, together with pirated tablets, porn, Mp3s, and pretend antivirus merchandise. ChronoPay workers used their MegaPlan accounts to trace fee disputes, order volumes, and promoting partnerships for these high-risk packages.
Borrowing a web page from the Quentin Tarantino film Reservoir Canines, the workers adopted nicknames like “Mr. Kink,” “Mr. Heppner,” and “Ms. Nati.” Nonetheless, in a basic failure of operational safety, many of those workers had their MegaPlan account messages routinely forwarded to their actual ChronoPay e-mail accounts.
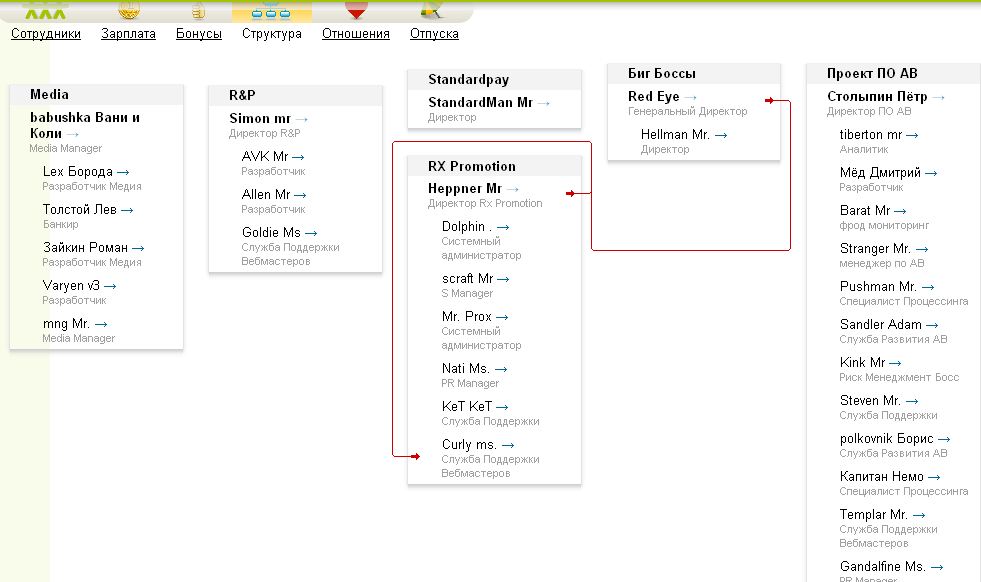
When ChronoPay’s inner emails have been leaked in 2010, the username and password for its MegaPlan subscription have been nonetheless working and legitimate. An inner consumer listing for that subscription included the private (non-ChronoPay) e-mail deal with tied to every worker Megaplan nickname. That listing itemizing mentioned the e-mail deal with zaxvatmira@gmail.com was assigned to the pinnacle of the Media/Mp3 division for ChronoPay, pictured on the high left of the organizational chart above as “Babushka Vani and Koli.”
[Author’s note: I initially overlooked the presence of the email address zaxvatmira@gmail.com in my notes because it did not show up in text searches of my saved emails, files or messages. I rediscovered it recently when a text search for zaxvatmira@gmail.com on my Mac found the address in a screenshot of the ChronoPay MegaPlan interface.]
The nickname two rungs down from “Babushka” within the ChronoPay org chart is “Lev Tolstoy,” which the MegaPlan service confirmed was picked by somebody who used the e-mail deal with v.zhabukin@freefrog-co-ru.
ChronoPay’s emails present that this Freefrog e-mail deal with belongs to a Vasily Borisovich Zhabykin from Moscow. The Russian enterprise monitoring web site rusprofile[.]ru studies that Zhabykin is or was the supervisor or proprietor of three Russian organizations, together with one referred to as JSC Sizzling Spot.
[Author’s note: The word “babushka” means “grandma” in Russian, and it could be that this nickname is a nod to the ChronoPay CEO’s wife, Vera. The leaked ChronoPay emails show that Vera Vrublevsky managed a group of hackers working with their media division, and was at least nominally in charge of MP3 projects for ChronoPay. Indeed, in messages exposed by the leaked ChronoPay email cache, Zhabykin stated that he was “directly subordinate” to Mrs. Vrublevsky].
CYBERCRIME HOTSPOT
JSC Sizzling Spot is fascinating as a result of its co-founder is one other ChronoPay worker: 37-year-old Mikhail “Mike” Shefel. A Fb profile for Mr. Shefel says he’s or was vp of fee techniques at ChronoPay. Nonetheless, the final replace on that profile is from 2018, when Shefel seems to have legally modified his final title.
Archive.org reveals that Sizzling Spot’s web site — myhotspot[.]ru — offered quite a lot of consulting providers, together with IT safety assessments, code and system audits, and e-mail advertising and marketing. The earliest recorded archive of the Sizzling Spot web site listed three shoppers on its homepage, together with ChronoPay and Freefrog.
ChronoPay inner emails present that Freefrog was considered one of its funding initiatives that facilitated the sale of pirated Mp3 recordsdata. Rusprofile[.]ru studies that Freefrog’s official firm title — JSC Freefrog — is included by a thinly-documented entity based mostly within the Seychelles referred to as Impex Consulting Ltd., and it’s unclear who its true house owners are.
Nonetheless, a search at DomainTools.com on the telephone quantity listed on the homepage of myhotspot[.]ru (74957809554) reveals that quantity is related to eight domains.
Six of these domains are some variation of FreeFrog. One other area registered to that telephone quantity is bothunter[.]me, which included a copyright credit score to “Sizzling Spot 2011.” On the annual Russian Web Week IT conference in Moscow in 2012, Mr. Shefel gave a brief presentation about bothunter, which he described as a service he designed to establish inauthentic (bot) accounts on Russian social media networks.
Curiously, considered one of r-fac1’s first posts to Searchengines[.]ru a yr earlier noticed this consumer requesting assist from different members who had entry to massive numbers of hacked social media accounts. R-fac1 informed discussion board members that he was solely wanting to make use of these accounts to submit innocent hyperlinks and feedback to the followers of the hacked profiles, and his submit prompt he was testing one thing.
“Good afternoon,” r-fac1 wrote on Dec. 20, 2010. “I’m on the lookout for individuals with their very own not-recently-registered accounts on boards, (aside from search) Social networks, Twitter, blogs, their web sites. Duties, relying in your accounts, submit textual content and a hyperlink, generally only a hyperlink. Most frequently the subject is chatter, rest, dialogue. Posting my hyperlinks in your profiles, in your partitions. A separate supply for individuals with a big set of contacts in instantaneous messengers to attempt to use viral advertising and marketing.”
Neither Mr. Shefel nor Mr. Zhabykin responded to requests for remark.
WHERE ARE THEY NOW?
Mr. Zhabykin quickly moved on to larger ventures, co-founding a cryptocurrency trade based mostly in Moscow’s monetary heart referred to as Suex. In September 2021, Suex earned the excellence of turning into the primary crypto agency to be sanctioned by the U.S. Division of the Treasury, which successfully blocked Suex from the worldwide monetary system. The Treasury alleged Suex helped to course of thousands and thousands in prison transactions, together with the proceeds of quite a few ransomware assaults.
“I don’t perceive how I bought blended up on this,” Zhabykin informed The New York Occasions in 2021. Zhabykin mentioned Suex, which is registered within the Czech Republic, was largely a failure and had carried out solely a half dozen or so transactions since 2019.
The Russian enterprise monitoring service Rusprofile says Zhabykin is also the proprietor of an organization based mostly in the UK referred to as RideWithLocal; the corporate’s web site says it makes a speciality of arranging excursions for excessive sports activities, together with snowboarding, snowboarding, browsing and parasailing. Photographs from the RideWithLocal Fb web page present helicopters dropping snowboarders and skiers atop some pretty steep mountains.

A screenshot from the Fb web page of RideWithLocal.
Constella Intelligence discovered a cached copy of a now-deleted LinkedIn profile for Mr. Zhabykin, who described himself as a “sporttech/fintech specialist and mentor.”
“I create services and products worldwide, specializing in innovation and world challenges,” his LinkedIn profile mentioned. “I’ve began my profession in 2002 and since then I labored in Moscow, totally different areas of Russia, together with Siberia and in Finland, Brazil, United Kingdom, Sri Lanka. During the last 15 years I contributed to many superb merchandise within the following industries: sports activities, ecology, sport tech, fin tech, digital funds, massive information, telecommunications, pulp and paper trade, wooden processing and journey. My specialities are Product improvement, Mentorship, Technique and Enterprise improvement.”
Rusprofile studies that Mikhail Borisovich Shefel is related to a minimum of eight present or now-defunct corporations in Russia, together with Dengi IM (Cash IM), Web Capital, Web Lawyer, Web 2, Zao Sizzling Spot, and (my private favourite) an entity included in 2021 referred to as “All of the Cash within the World.”
Constella Intelligence discovered a number of official paperwork for Mr. Shefel that got here from hacked Russian telephone, vehicle and residence information. They point out Mr. Shefel is the registrant of a black Porsche Cayenne (Plate:X537SR197) and a Mercedes (Plate:P003PX90). These car information present Mr. Shefel was born on Could 28, 1986.
Rusprofile reveals that in some unspecified time in the future close to the tip of 2018, Shefel modified his final title to Lenin. DomainTools studies that in 2018, Mr. Shefel’s firm Web 2 LLC registered the area title Lenin[.]me. This now-defunct service offered bodily USSR-era Ruble notes that bear the picture of Vladimir Lenin, the founding father of the Soviet Union.

In the meantime, Pavel Vrublevsky stays imprisoned in Russia, awaiting trial on fraud prices levied towards the fee firm CEO in March 2022. Authorities allege Vrublevsky operated a number of fraudulent SMS-based fee schemes. Additionally they accused Vrublevsky of facilitating cash laundering for Hydra, the biggest Russian darknet market. Hydra trafficked in unlawful medication and monetary providers, together with cryptocurrency tumbling for cash laundering, trade providers between cryptocurrency and Russian rubles, and the sale of falsified paperwork and hacking providers.
In 2013, Vrublevsky was sentenced to 2.5 years in a Russian penal colony for convincing considered one of his high spammers and botmasters to launch a distributed denial-of-service (DDoS) assault towards a ChronoPay competitor that shut down the ticketing system for the state-owned Aeroflot airline.
Following his launch, Vrublevsky started engaged on a brand new digital funds platform based mostly in Hong Kong referred to as HPay Ltd (a.okay.a. Hong Kong Processing Company). HPay seems to have had a large number of shoppers that have been working schemes which bamboozled individuals with faux lotteries and prize contests.
KrebsOnSecurity sought touch upon this analysis from the Federal Bureau of Investigation (FBI) and the U.S. Secret Service, each of which have been concerned within the Goal breach investigation over time. The FBI declined to remark. The Secret Service declined to verify or dispute any of the findings, however mentioned it’s nonetheless curious about listening to from anybody who might need extra data.
“The U.S. Secret Service doesn’t touch upon any open investigation and gained’t affirm or deny the accuracy in any reporting associated to a prison method,” the company mentioned in a written assertion. “Nonetheless, When you’ve got any data referring to the topics referenced on this article, please contact the U.S. Secret Service at mostwanted@usss.dhs.gov. The Secret Service pays a reward for data resulting in the arrest of cybercriminals.”