The marketing campaign begins with an e mail and ends with the account being compromised, however there are just a few notable steps all through the an infection chain earlier than the goal enterprise account is absolutely compromised. Every step follows the identical lure to attract victims in and acquire delicate data associated to the account. Pictures of the phishing pages could be seen in Determine 2 beneath.
- Electronic mail Hyperlink – The phishing emails begin with a hyperlink that’s both hyperlinked to textual content or embedded right into a clickable picture just like the “Confirm” button seen earlier. These hyperlinks are all hosted on the domains Netlify[.]app or Vercel[.]app, that are internet hosting providers that the risk actors are abusing to host their phishing websites. In some circumstances, the marketing campaign incorporates a t[.]co, X’s hyperlink shortener, into the an infection chain that simply acts as a further redirect.
- Step 1: Touchdown Web page – Following the e-mail, customers are met with a touchdown web page that serves no useful goal apart from to control customers into believing this can be a authentic course of to get well their account.
- Step 2: Account Info – The second step harvests Meta account data corresponding to enterprise e mail, web page identify, web page proprietor, e mail handle, cellphone quantity, data associated to monetary data, and up to date journey preparations, and an space to submit an attraction. A few of this data could seem pointless, however within the case of the risk actors efficiently having access to an account, this might assist them disrupt Meta’s account restoration course of.
- Step 3: Account Password – The third step is fairly simple, it simply requests that the consumer enter their password. Stolen data on this marketing campaign is exfiltrated to numerous areas arrange by the risk actors, one instance is that credentials have been posted to a Telegram bot.
- MFA Bypass Step – This step is what makes this marketing campaign such a high-level and probably profitable risk. It’s comparatively easy at first look, it simply requests that the consumer inputs their 6-digit or 8-digit code from their authenticator app. As soon as entered, there’s a loading course of that primarily waits lengthy sufficient for a brand new code to be generated after which requests it once more. This extra step is probably going used to make sure that entry to the account has efficiently been stolen.
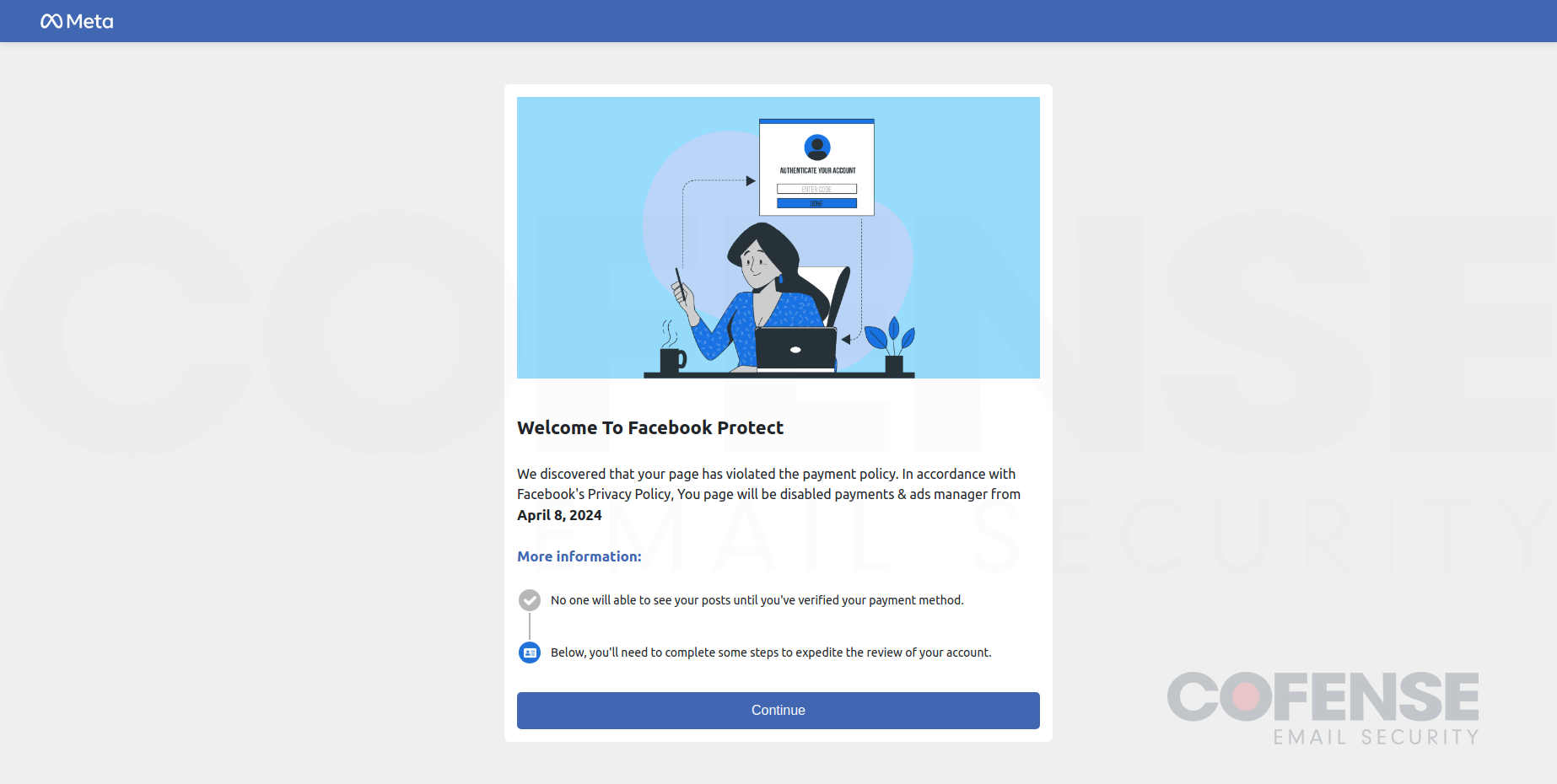
Determine 2: The touchdown web page, the primary web page that customers will see after interacting with the phishing URL.
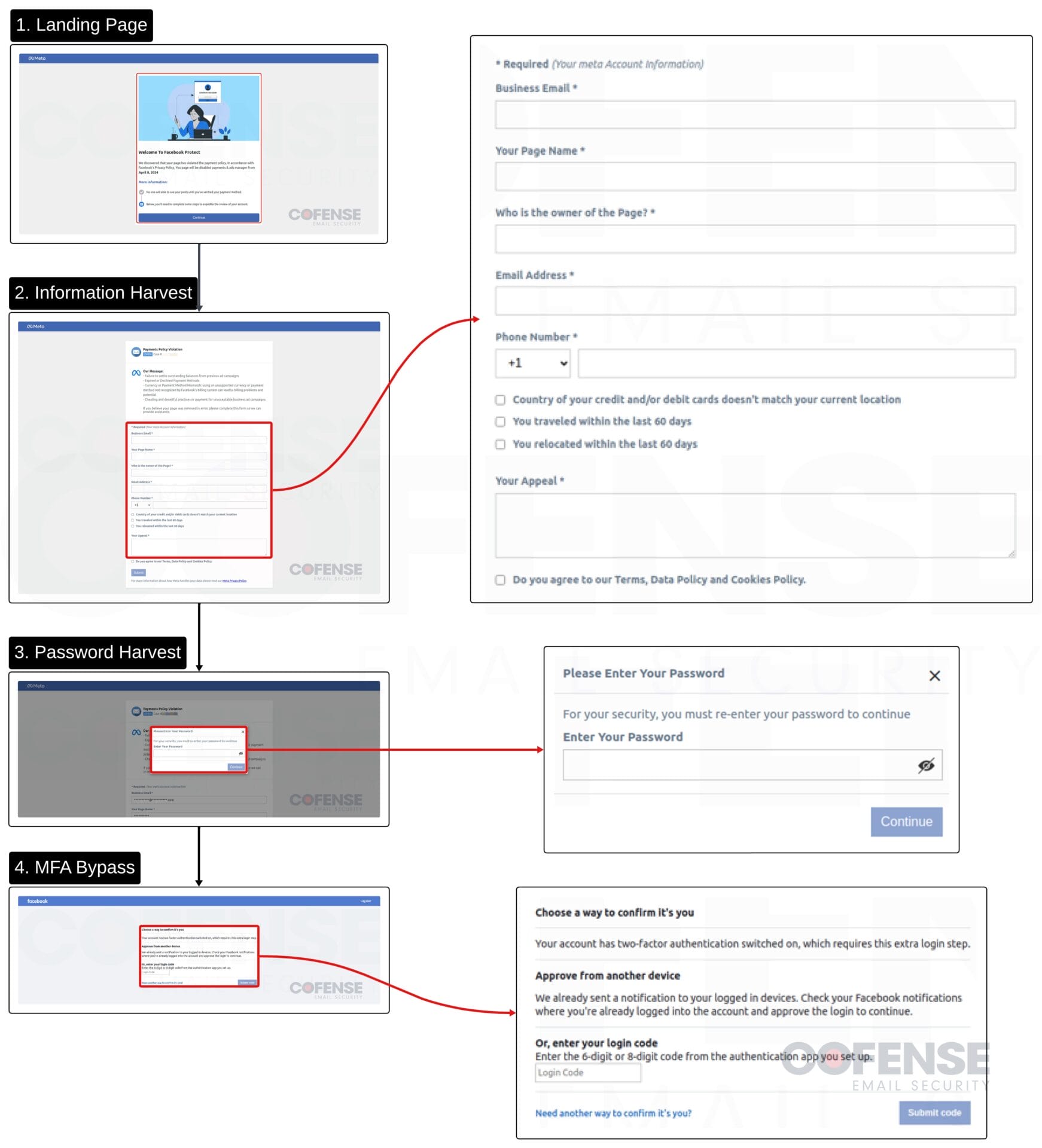
Determine 3: Breakdown of the total phishing an infection chain.
A Deep Evaluation of Risk Actor Infrastructure
Throughout an evaluation, a Cofense risk analyst recognized open entry to tooling used for this marketing campaign hosted on bot1[.]sieulike[.]com. The positioning accommodates a number of redirects which were translated from Vietnamese to English. These redirects go to areas the risk actors steadily go to like Netlify[.]app to create new hyperlinks, Microsoft e mail login for Hotmail, and two spreadsheets; one for income and prices along with one containing information on international locations they aim. Most of those are locked behind logins and require entry to be granted by the risk actors.
Specifically, the Revenue / value spreadsheet requires a login to have the ability to entry the spreadsheet. The actual fact that there’s a spreadsheet particularly for prices and income implies that the risk actors are in search of monetary achieve. Whereas that’s apparent for many campaigns, for this one, particularly, it definitely proves that the risk actors will make use of a further assault vector as soon as the enterprise advert account has been compromised.
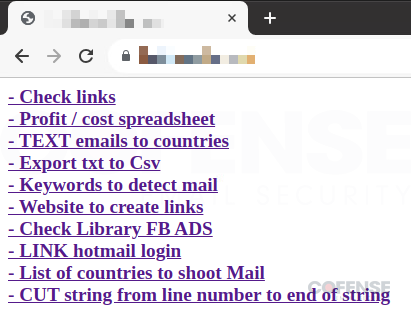
Determine 4: Risk actor sources, infrastructure, and instruments used on this marketing campaign.
The positioning additionally hosts a number of instruments that present how environment friendly and superior these risk actors are. These instruments differ from merely changing enter textual content right into a CSV to producing full phishing emails. A breakdown of a few of the extra notable instruments which are listed in Determine 4:
- Verify Hyperlinks (Figures 5 and 6) – All the indicators of compromise you would ever need are conveniently included on this instrument. Not solely does it comprise a protracted checklist of phishing URLs which are actively getting used, however it additionally permits the risk actors to robotically test if the hyperlinks are nonetheless dwell or have been taken down.
- TEXT emails to international locations (Determine 7) – It is a distinctive instrument used to robotically generate phishing emails primarily based on standards entered by the risk actors. The risk actors choose one of many 19 totally different international locations they aim, the theme they need the e-mail to be (coverage violation or copywriting infringement), the phishing hyperlink they need to use, after which it generates a textual content model of the e-mail and the headers.
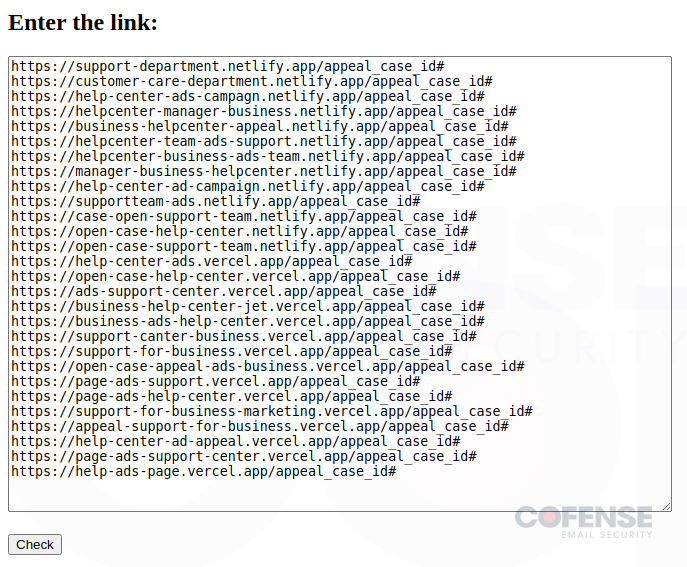
Determine 5: Risk actor instrument to enter malicious hyperlinks to test in the event that they’re lively.
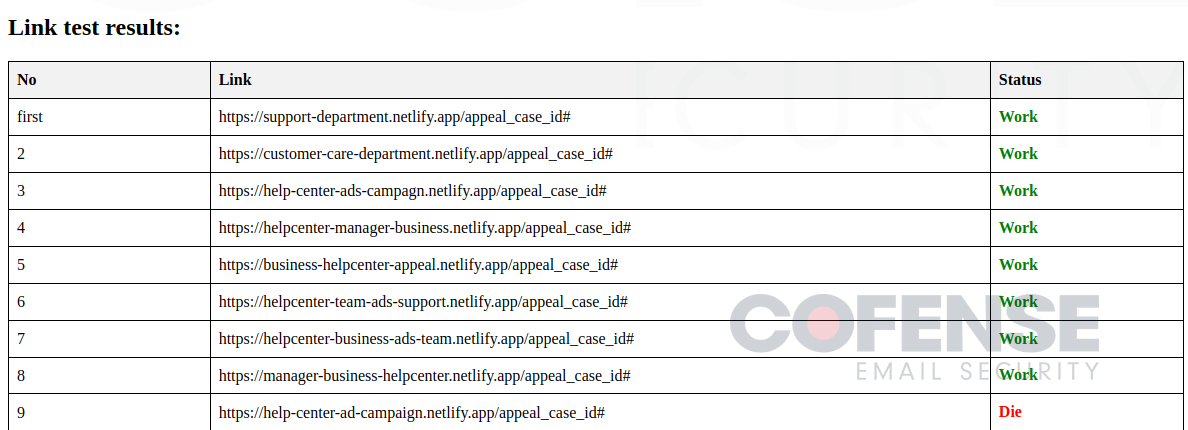
Determine 6: Outcomes from the URL enter displaying if lively or lifeless.
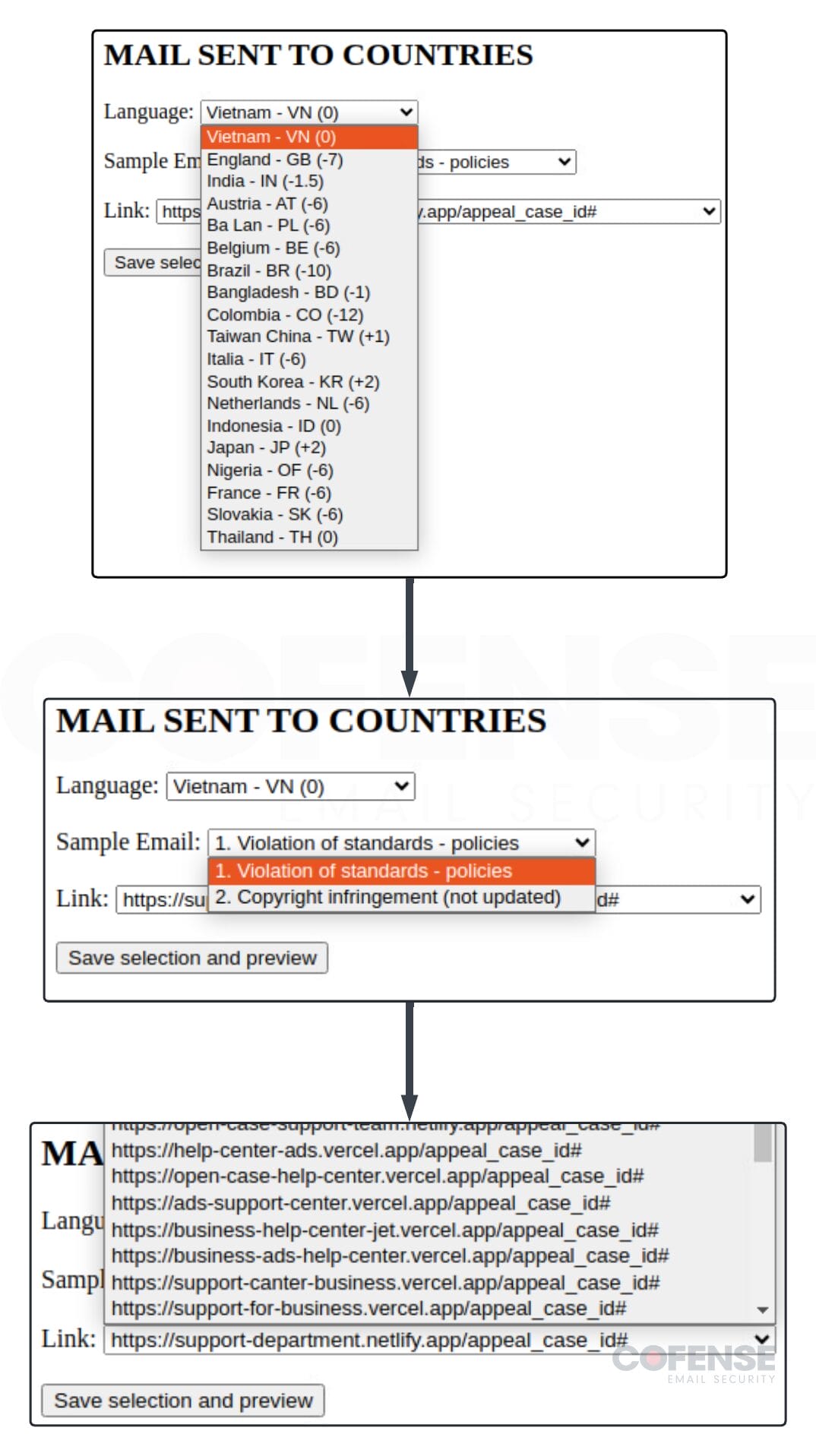
Determine 7: Risk actor instrument to generate phishing emails for this marketing campaign.
Meta Spoofing within the Risk Panorama
Cofense experiences on a major quantity of credential phishing emails on daily basis that have been uncovered inside an enterprise consumer’s inbox. Of these emails, Meta is the second most spoofed model seen within the first quarter of 2024. Out of the campaigns spoofing Meta, emails from this marketing campaign make up an excellent portion of the quantity. Determine 8 beneath reveals the highest 5 manufacturers spoofed in Credential Phishing campaigns seen by Cofense in Q1 of this yr. Meta follows behind Microsoft, which is well-known for being spoofed in a excessive share of phishing emails as a result of standard use of Microsoft e mail providers.
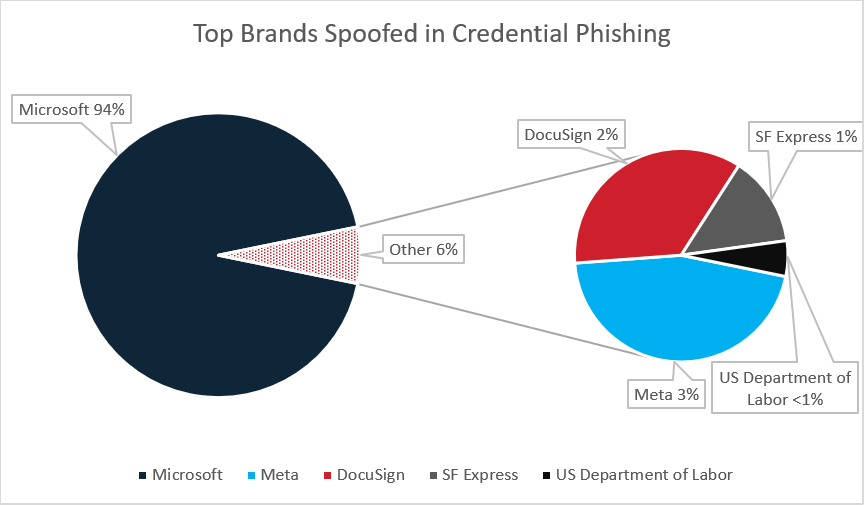
Determine 8: Prime manufacturers spoofed in Credential Phishing campaigns seen by Cofense in Q1 2024.
Redmi 13C 5G (Startrail Green, 4GB RAM, 128GB Storage) | MediaTek Dimensity 6100+ 5G | 90Hz Display
₹10,499.00 (as of May 14, 2024 14:12 GMT +00:00 - More infoProduct prices and availability are accurate as of the date/time indicated and are subject to change. Any price and availability information displayed on [relevant Amazon Site(s), as applicable] at the time of purchase will apply to the purchase of this product.)Fire-Boltt Phoenix Ultra Luxury Stainless Steel, Bluetooth Calling Smartwatch, AI Voice Assistant, Metal Body with 120+ Sports Modes, SpO2, Heart Rate Monitoring (Gold)
₹1,749.00 (as of May 14, 2024 14:12 GMT +00:00 - More infoProduct prices and availability are accurate as of the date/time indicated and are subject to change. Any price and availability information displayed on [relevant Amazon Site(s), as applicable] at the time of purchase will apply to the purchase of this product.)realme NARZO 70x 5G (Forest Green, 6GB RAM,128GB Storage| 120Hz Ultra Smooth Display | Dimensity 6100+ 6nm 5G | 50MP AI Camera | 45W Charger in The Box
₹13,499.00 (as of May 14, 2024 14:12 GMT +00:00 - More infoProduct prices and availability are accurate as of the date/time indicated and are subject to change. Any price and availability information displayed on [relevant Amazon Site(s), as applicable] at the time of purchase will apply to the purchase of this product.)Oneplus Nord CE4 (Dark Chrome, 8GB RAM, 256GB Storage)
₹26,999.00 (as of May 14, 2024 14:12 GMT +00:00 - More infoProduct prices and availability are accurate as of the date/time indicated and are subject to change. Any price and availability information displayed on [relevant Amazon Site(s), as applicable] at the time of purchase will apply to the purchase of this product.)OnePlus Nord Buds 2r True Wireless in Ear Earbuds with Mic, 12.4mm Drivers, Playback:Upto 38hr case,4-Mic Design, IP55 Rating [Deep Grey]
₹1,799.00 (as of May 14, 2024 14:12 GMT +00:00 - More infoProduct prices and availability are accurate as of the date/time indicated and are subject to change. Any price and availability information displayed on [relevant Amazon Site(s), as applicable] at the time of purchase will apply to the purchase of this product.)Ambrane Unbreakable 60W / 3A Fast Charging 1.5m Braided Micro USB Cable for Smartphones, Tablets, Laptops & other Micro USB devices, 480Mbps Data Sync, Quick Charge 3.0 (RCM15, Black)
₹149.00 (as of May 14, 2024 14:12 GMT +00:00 - More infoProduct prices and availability are accurate as of the date/time indicated and are subject to change. Any price and availability information displayed on [relevant Amazon Site(s), as applicable] at the time of purchase will apply to the purchase of this product.)Zebronics-NS1500 Laptop Stand Featuring Foldable Design, Anti-Slip Silicone Rubber Pads, Supports Maximum of 5kgs Weight Tabletop
₹299.00 (as of May 14, 2024 14:12 GMT +00:00 - More infoProduct prices and availability are accurate as of the date/time indicated and are subject to change. Any price and availability information displayed on [relevant Amazon Site(s), as applicable] at the time of purchase will apply to the purchase of this product.)STRIFF Mpad Mouse Mat 230X190X3mm Gaming Mouse Pad, Non-Slip Rubber Base, Waterproof Surface, Premium-Textured, Compatible with Laser and Optical Mice(Universe Black)
₹99.00 (as of May 14, 2024 14:12 GMT +00:00 - More infoProduct prices and availability are accurate as of the date/time indicated and are subject to change. Any price and availability information displayed on [relevant Amazon Site(s), as applicable] at the time of purchase will apply to the purchase of this product.)amazon basics Type A to Micro USB Braided Cable | 3A/18W Fast Charging and 480 Mbps Data Transfer Speed | 1.2m, Tangle Free Cable
₹109.00 (as of May 14, 2024 14:12 GMT +00:00 - More infoProduct prices and availability are accurate as of the date/time indicated and are subject to change. Any price and availability information displayed on [relevant Amazon Site(s), as applicable] at the time of purchase will apply to the purchase of this product.)Wayona Nylon Braided USB to Lightning Fast Charging and Data Sync Cable Compatible for iPhone 14,13, 12,11,X, 8, 7, 6, 5, iPad Air, Pro, Mini (3 FT Pack of 1, Grey)
₹399.00 (as of May 14, 2024 14:12 GMT +00:00 - More infoProduct prices and availability are accurate as of the date/time indicated and are subject to change. Any price and availability information displayed on [relevant Amazon Site(s), as applicable] at the time of purchase will apply to the purchase of this product.)Auto Amazon Links: No products found.











