Cryptocurrency-based crime has metastasized into many kinds. Due to the benefit with which cryptocurrency ignores borders and permits multinational crime rings to shortly acquire and launder funds, and due to widespread confusion about how cryptocurrency capabilities, a variety of confidence scams have centered on convincing victims to transform their private financial savings to crypto—after which separate them from it.
Amongst these types of organized prison actions, none appear as pervasive as “pig butchering” (from the Mandarin time period, sha zhu pan, coined to explain the exercise). Most of those scams use courting purposes or different social media to lure victims into what they assume is a budding romantic or platonic relationship, after which introduce a fraudulent scheme to earn cash collectively. In some current circumstances we discovered the scammers utilizing generative AI to write down messages to their targets to make them extra convincing.
We first started investigating pig butchering scams in 2020 in reference to faux cryptocurrency-trading cellular apps that system customers had downloaded on the course of somebody the consumer had been contacted by most of the time by way of a courting app or web site. We dubbed these “CryptoRom” apps, and have continued to analysis the rip-off rings, and the way they evade platform safety on cellular gadgets. One methodology that has grow to be prevalent over the previous yr is to leverage the weaknesses of legit cryptocurrency purposes by way of their skill to be linked to internet purposes.
Not too long ago, I shared the particulars of a rip-off case by which a person sufferer (whom we known as “Frank”) misplaced over $20,000 USD in a faux “mining pool.” Primarily based on the small print Frank supplied, we have been capable of uncover a a lot bigger set of scams utilizing over a dozen totally different domains. The infrastructure of those domains was constructed on 5 totally different controlling “contract wallets” that directed cryptocurrency from victims’ wallets to different wallets for laundering. This set of scams seems to have interacted with over 90 victims. Now we have excessive confidence that the rip-off was run by three units of associates related to a multinational Chinese language-language crime group.
Wanting again to the start of 2023, I discovered these contract wallets had moved $1.22 million value of Tether (USDT) cryptocurrency from focused wallets to locations laundering the stolen crypto between January 1 and November 20. They seem to have been run by three separate menace exercise teams utilizing similar fraudulent decentralized finance (“DeFi”) app websites, suggesting that they’re a part of or affiliated with a single organized crime ring.
The ring is probably a lot bigger. I discovered traces of two different domains that matched our fingerprint for the location that had been deactivated earlier than I might acquire contract information. Inspecting the wallets that obtained the funds for laundering, I discovered further contract wallets that have been transferring scammed funds from different victims—some pointing to further laundering wallets. I proceed to research the information to determine additional rip-off operations.
In complete, the wallets concerned within the scheme moved practically $2.9 million value of cryptocurrency this yr as of November 15, coming from the scams we tracked and different criminality.
Following the cash
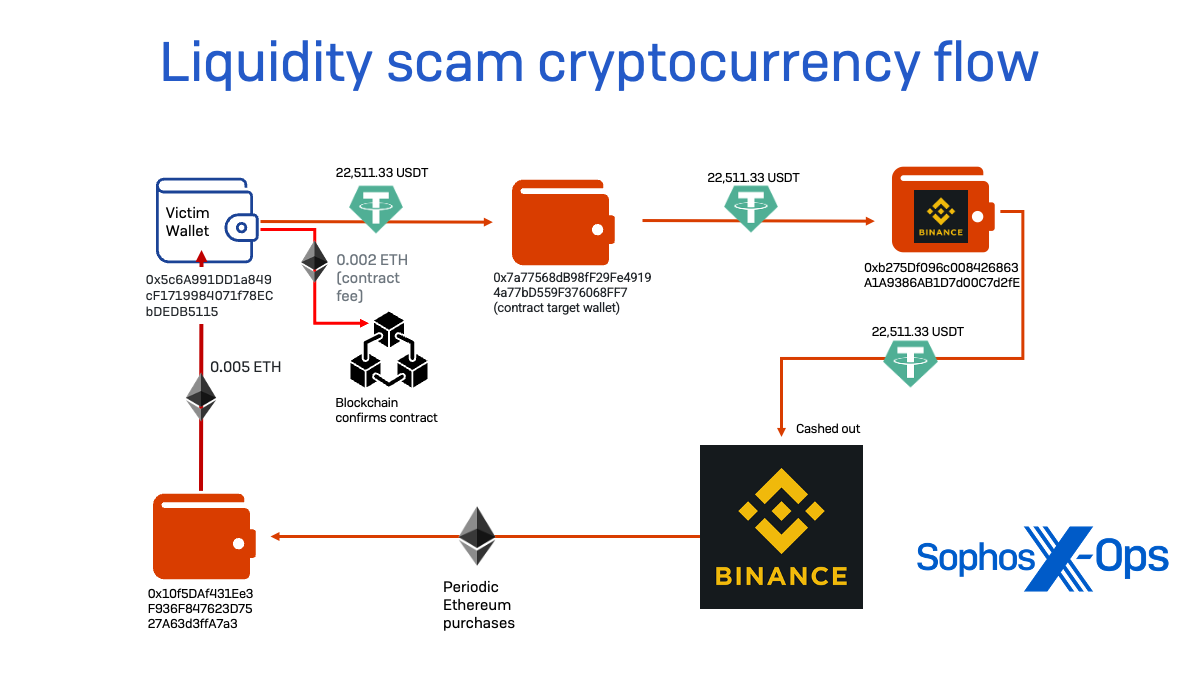
Throughout our investigation of the rip-off concentrating on “Frank,” I tracked the move of cryptocurrency from his pockets. The scammer’s lure was a faux decentralized finance app hosted on the area allnodes[.]vip—a website registered by way of and hosted by Alibaba.
The app created a wise contract—paid for in Ethereum supplied by the scammer in Frank’s case, and certain in all different scams run by this ring—that gave one other pockets handle a just about limitless “allowance,” permitting its proprietor to see the steadiness of the pockets being linked and to switch Tether tokens deposited within the linked pockets. This distant handle—the contract pockets—by no means moved cryptocurrency to itself however as a substitute transferred balances to different wallets underneath management of the scammers utilizing the sensible contract authority by authorizing transactions on the blockchain.
transactions for the management node, I used to be capable of decide that our sufferer was not the primary focused by this explicit rip-off configuration. The management node was first lively on April 5, making what could have been a take a look at switch of $55 value of Tether to test the faux DeFi app’s configuration; the primary sufferer seems to have had funds transferred the following day, being hit over the next two weeks for a complete of $15,400 value of cryptocurrency. In complete earlier than the node went quiet in early August, at the least 7 targets could be fleeced by the scammers for quantities starting from $2,000 to over $50,000—totaling $177,560.
Utilizing traits of this rip-off, I went trying to find further websites that have been comparable. And it shortly grew to become clear that this was related to a a lot bigger operation.
Trying to find extra domains and contract wallets
By inspecting area registry information, I discovered one other area utilizing the identical branding (allnodes[.]xyz) additionally registered and hosted by way of Alibaba at a special IP handle. The websites have been similar in look and in underlying HTML and JavaScript code. The websites shared not simply the identical look, however the identical script file names and used the identical JavaScript-based in-site chat service (tawk[.]to). Nonetheless, the app on the .xyz area used a special contract pockets for its sensible contract payload.
I expanded my search by inspecting the net requests from every of those websites and looking for websites with the identical JavaScript and filenames. Primarily based on these fingerprints, I discovered 11 further domains internet hosting the identical actual code, some sharing the identical contract wallets of their configurations.
In complete, I discovered 4 addresses appearing as management nodes throughout 14 domains. I additionally discovered two domains that had ceased operation however matched all traits in historic telemetry and third-party information. Inspecting the websites, I found distinct groupings of domains utilizing comparable naming conventions, area registrars and hosts, suggesting totally different sub-groups have been working similar rip-off kits concurrently. That is much like what we discovered when investigating pig butchering faux alternate websites, the place dozens of web sites have been utilizing the identical code however with totally different related pockets addresses.
| Group | Area | Contract wallets | Internet hosting | Registrar | Complete Crypto quantity of transactions
(US $) |
|
|---|---|---|---|---|---|---|
| Allnodes | allnodes.vip | 0x6B79f38233726282c7F88FE670F871eAbd0c746c | Alibaba Singapore | Alibaba Cloud | 177,596.00 | |
| allnodes.xyx | 0xd2b14d2fff430a720cf44bbd064f548a585e73de | Alibaba Cloud | Alibaba Cloud | 174,934.00 | ||
| Belief | trust-oke[.}com | 0xcf6b558c218a9148cd77c04be4e3d1c1fc9d61a2 | Amazon | Amazon | 676,869.00 | |
| trust-btrust-oke[.}com | ||||||
| trust-usdt[.]com | ||||||
| trust-v2[.]com | ||||||
| trust-bnb[.]hyperlink | ||||||
| v2-eth[.]com | ||||||
| net-8897[.]com | ||||||
| Ada | ada-defi[.]pics | 0xeb7b75dd5b4b6ef7bbc6ec079cd329a782fc1efe | Cloudflare protected | Dynadot | 62,660.00 | |
| ada-defi[.]magnificence | ||||||
| ada-defi[.]xyz | ||||||
| ada-coin[.]data | ||||||
| eth-defi[.]one | ||||||
| Unknown | trust-eth[.]com | Google, then Cloudflare | Gname.com | |||
| eth-mining[.]xyz | Google, then Cloudflare | Dynadot |
As proven within the desk above, two teams of domains had shared contract pockets addresses. And thru inspecting transaction information, I discovered that each “allnodes” domains, regardless of having separate contract wallets, routed cryptocurrency to the identical locations.
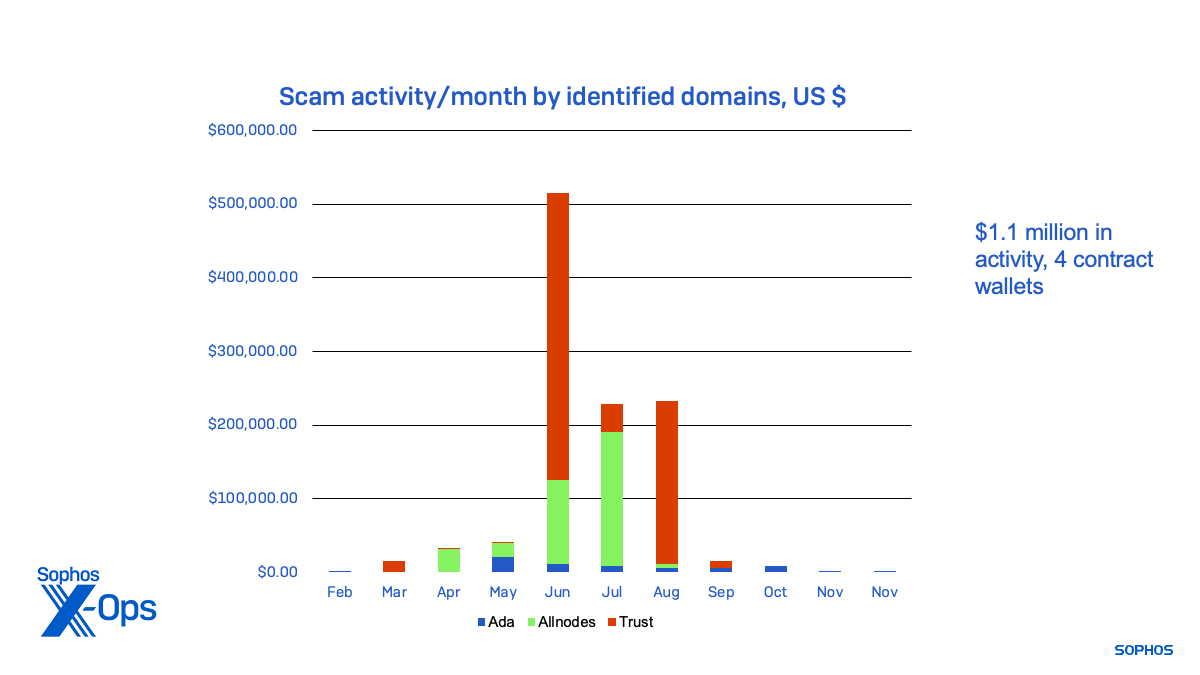
Exercise for the rip-off websites and their contract wallets, a few of which gave the impression to be testing the scripts related to contract wallets, dated again to February. A lot of the precise rip-off exercise related to the websites occurred in the summertime months, as proven beneath by the amount of cryptocurrency moved by way of every of the first contract wallets:
Additional inspecting the transaction information for the wallets receiving fraudulent withdrawals, I found further contract wallets sending crypto following the identical sample. They have been utilizing the identical vacation spot wallets as two of the above teams:
- 0x73b970978cbf19a5e1c727de20ad73db316f3817 and 0xf12a365e53313e59E915f0e8D432a326556dD22C, related to “Belief” vacation spot pockets;
- 0x3698cc343414c69233fe580cef379f02a91bc421 , related to an “Ada” group vacation spot pockets.
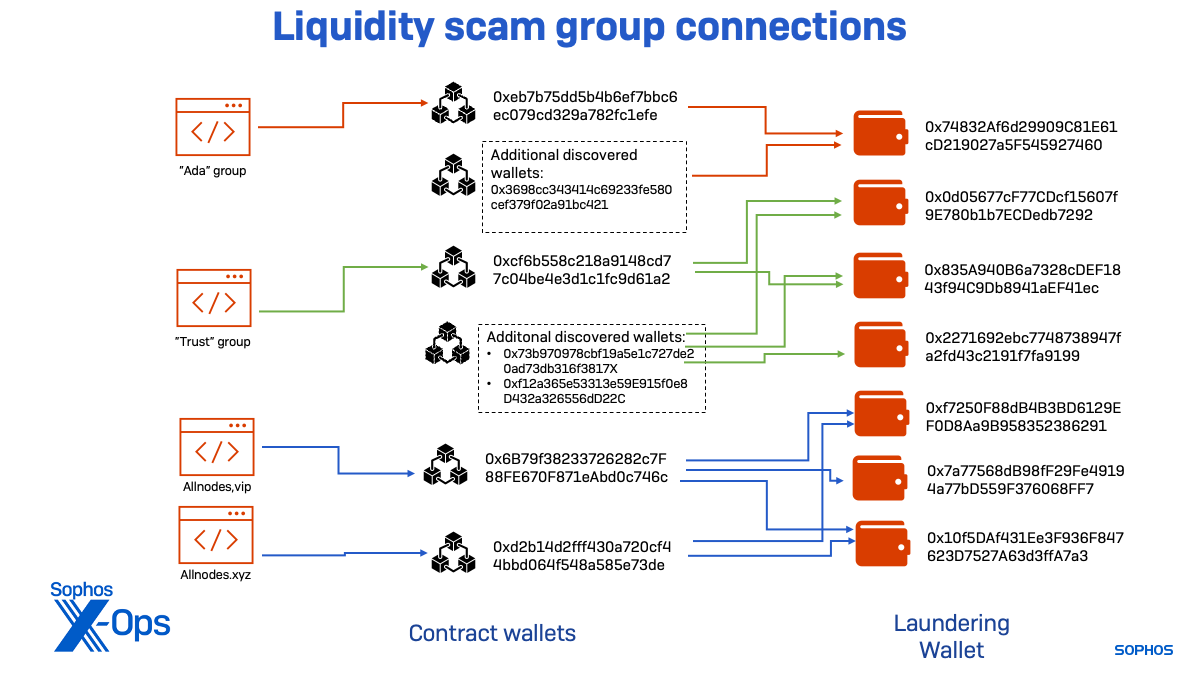
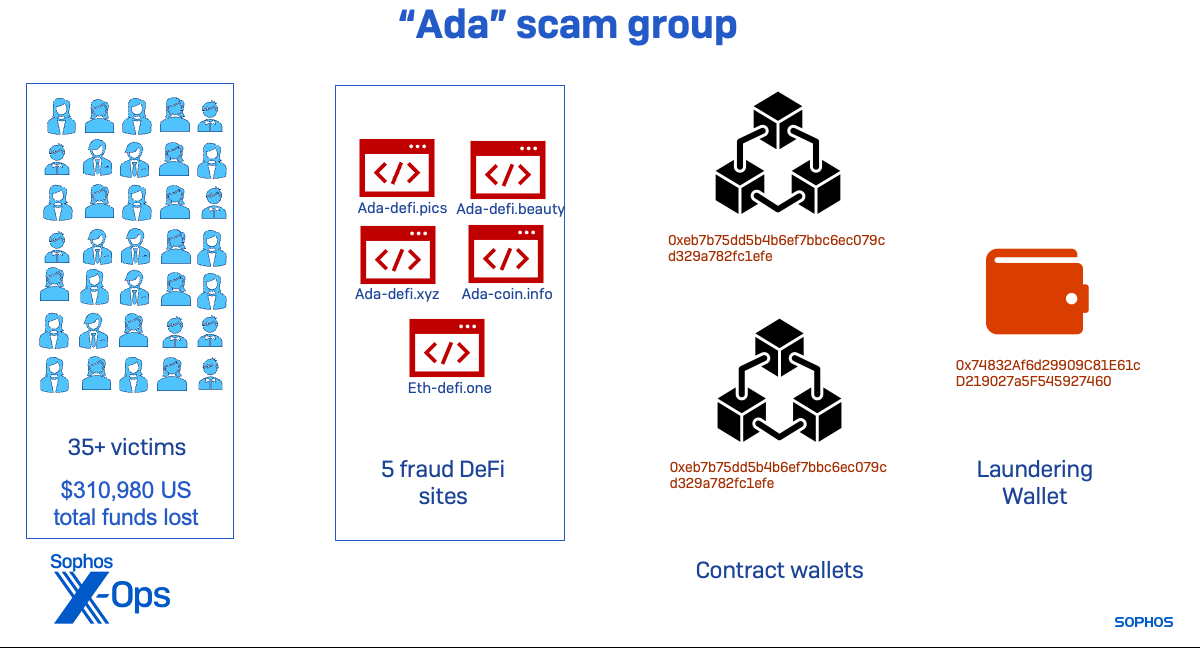
The “Ada” subgroup used a single pockets to launder funds from each its related contract wallets. This group of web sites was lively starting in March, however the wallets confirmed indicators of rip-off exercise as early as February, suggesting one other area was a part of the group.
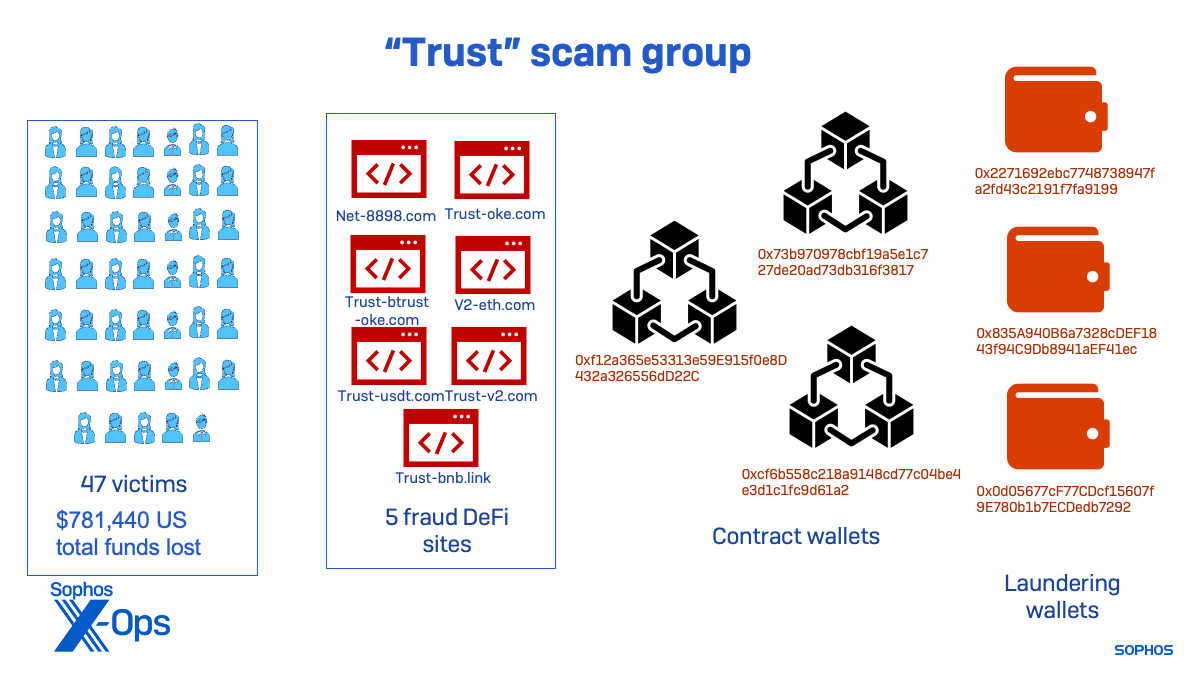
The “Belief” menace exercise cluster seems to have been lively the longest. One in all its contract wallets was extremely lively in January, indicating that one other rip-off website was lively in 2022. That pockets’s exercise fell off utterly in March, with different wallets related to newer websites turning into extra lively. As of November, the “Belief” cluster was nonetheless lively, however far lower than in the course of the peak of the rip-off websites I recognized.
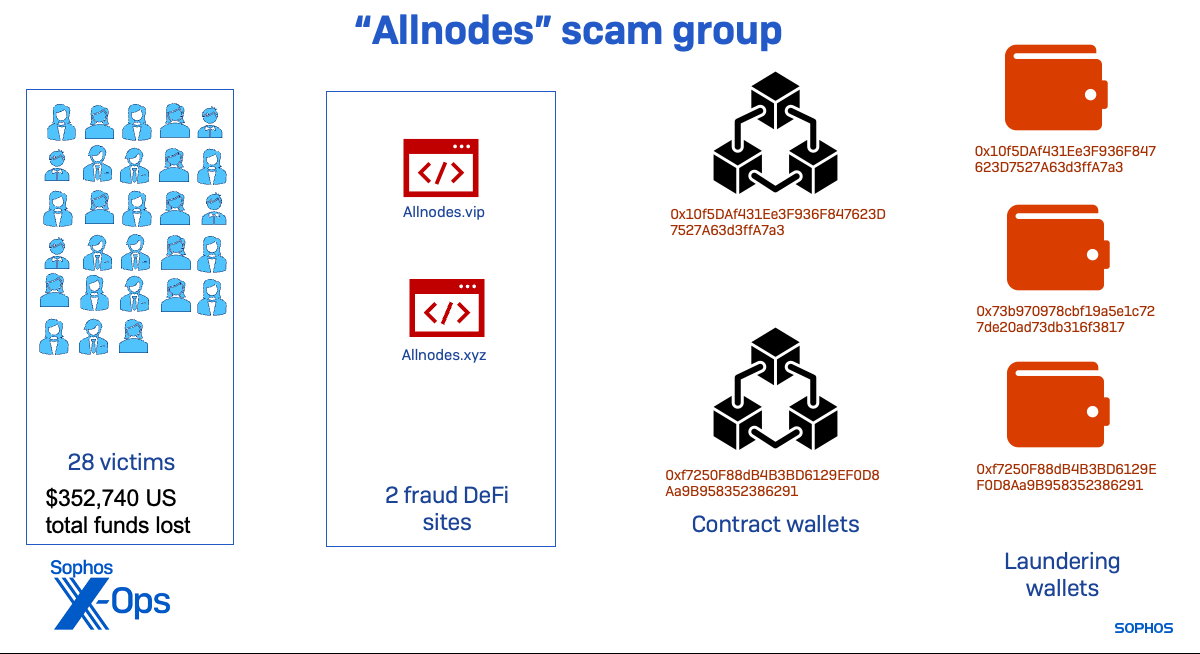
The “Allnodes” cluster was the one related to the “Frank” case. It began later than the others and shut down exercise tied to the infrastructure we recognized shortly after we have been contacted by the sufferer and commenced alerting pockets builders and exchanges of its presence. No additional money out exercise was seen on the wallets related to this menace group after August.
Regardless of being comparatively short-lived, the Allnodes group managed to herald over $352,000 earlier than its lifecycle was ended—most of which was cashed out by way of Hong Kong financial institution accounts.
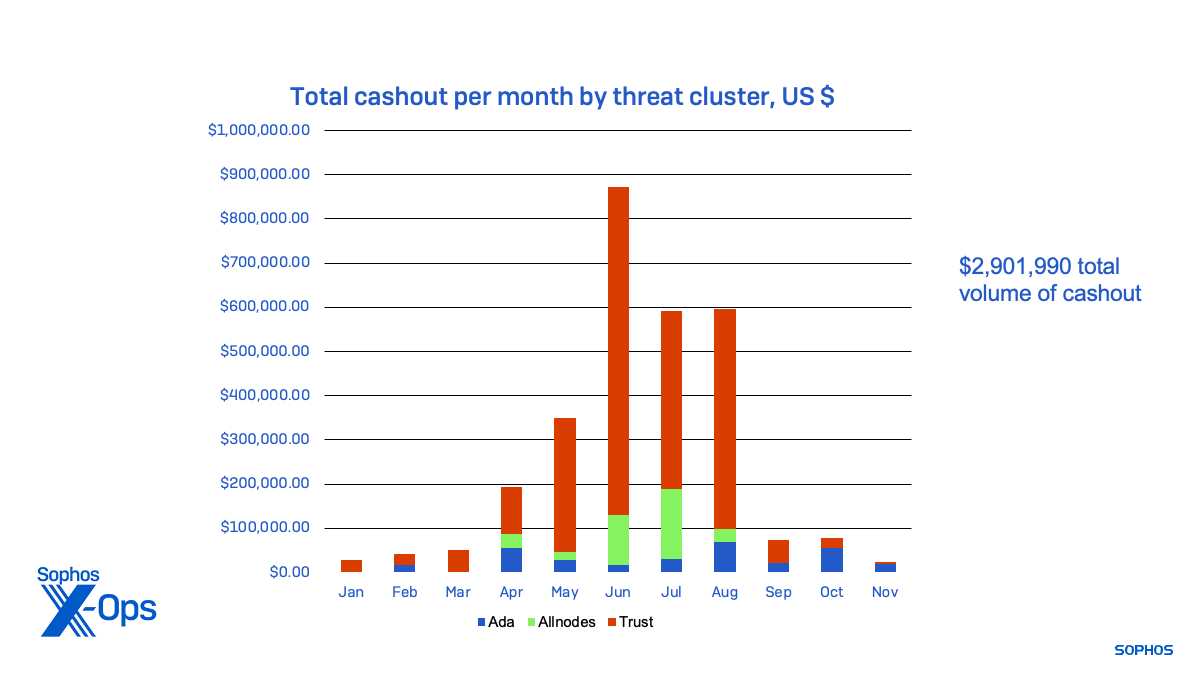 Determine 8: The funds cashed out by every of the menace exercise clusters, from January 2023 to November 2023
Determine 8: The funds cashed out by every of the menace exercise clusters, from January 2023 to November 2023
In complete, the teams utilizing the liquidity mining rip-off equipment introduced in over $2.9 million over the course of the yr. It’s doubtless that they proceed to run different, comparable scams with new infrastructure. And there are various different rip-off operations utilizing comparable ways, instruments and practices—as I discovered investigating suggestions I obtained from different rip-off victims in the course of the course of this analysis.
Extra kits, extra scams
Following the identical strategies—trying to find domains that used DeFi and cryptocurrency names or borrowed branding from legit cryptocurrency-related manufacturers—we discovered a number of further scams. One, I recognized, fronted by the area eth-defi[.]xyz, yielded one other contract pockets handle: 0x2e7e4df940a2c999bf5b5cdcd15a738b8bb462d5.
Between August 18 and November 28, that contract pockets had pulled $115,820 value of Tether cryptocurrency from victims. Nearly all of these funds have been cashed out by way of Binance.
![Figure 9: The fake liquidity mining site eth-defi[.]xyz](https://news.sophos.com/wp-content/uploads/2023/12/eth-defi-xyz.png)
Utilizing the artifacts of this website, I discovered one other 60 rip-off websites utilizing the identical equipment. I’ve not but carried out evaluation on these websites past confirming they’re working the identical rip-off interface.
As I investigated these rings, I noticed a shift in instruments and ways by different rip-off operations—which partially seems to be pushed by the response of exchanges and pockets builders to share menace information, enabling them to dam scams on the app stage. Rip-off device builders are taking measures to dam harvesting of contract node information, controlling which wallets might be used for the rip-off, and taking higher care to evade geolocation and evaluation. These extra cautious rip-off deployments spanned a whole lot of domains.
One instance of this variation in rip-off website tooling—associated to a rip-off hosted at phpsqo[.]prime—got here from a sufferer. The goal, a scholar in Poland, was approached by way of WhatsApp by somebody claiming to be a Chinese language lady dwelling in Germany. The interplay led to the goal connecting her cellular pockets to a contract pockets by way of that area: 0x63809823AD21B6314624621172bAf4532c5B8b72
The goal put $1,177.79 value of USDT within the pockets and noticed day by day deposits till the complete steadiness was pulled a few week later.
This contract pockets was extraordinarily lively, with over 950 transactions between March 26 and November 15, so guide evaluation of the full variety of victims and cryptocurrency transferred remains to be in progress. However drawing from a random sampling of the transactions, I estimate the contract pockets transferred at the least $200,000 value of cryptocurrency over that interval.
Getting that information would have been troublesome with out the sufferer offering her pockets handle, as the location makes use of JavaScript to detect the net agent connecting and disallows desktop browsers along with checking for cryptocurrency pockets connections.:
![Figure 10: a screenshot of phpsqo[.]top showing how it appears in a desktop browser](https://news.sophos.com/wp-content/uploads/2023/12/phpsqo-top.png)
Looking out on parts utilized by the location, I discovered 350 websites utilizing the very same equipment, most registered within the “.prime” top-level area, and all with internet hosting hid by way of Cloudflare. With out the flexibility to passively harvest information on contract wallets related to these websites with out utilizing the kind of pockets consumer permitted by the websites, it was not attainable to get an concept of the scope of the scams related to them.
I additionally recognized by way of DNS searching one other set of about 100 websites utilizing yet one more mining rip-off equipment. This one permits somebody to connect with the location with a browser-based pockets however checks the pockets steadiness earlier than permitting a connection to the contract pockets. Nonetheless others use an API from WalletConnect to obscure the contract pockets handle and hold out guests and not using a particular set of cellular wallets appropriate with that service.
![Figure 11: USDmining[.]shop, another liquidity mining scam site, requires a balance in a connected wallet before the contract can be accessed](https://news.sophos.com/wp-content/uploads/2023/12/USDmining-shop.png)
Caveat Investor
When in comparison with final yr’s investigations, it’s clear that liquidity mining rip-off operations have matured of their methods, instruments, and practices, and that rip-off decentralized finance app “kits” have made these operations easier to scale up—whereas being extra accessible to much less technically-capable cybercriminals. The shifting ways in newer kits counsel vital technical efforts are being made by device builders within the make use of of the Chinese language organized crime operations that again these rip-off rings.
As a result of these scams use legit purposes which were enabled to connect with decentralized finance purposes, the most effective protection towards these ever-maturing scams stays public consciousness of the scams and wholesome skepticism towards on-line interactions. As a result of victims of pig butchering-style scams reminiscent of these are sometimes remoted and focused by way of emotional appeals, extensive public outreach is the one strategy to forestall or cut back loss.
We proceed to do what we are able to by reporting websites, blocking them by way of adverse status scores, and collaborating with internet hosting suppliers, legislation enforcement and cryptocurrency exchanges to get websites and alternate accounts tied to them shut down.
Should you consider you’re a sufferer of certainly one of these scams, you must:
- Instantly withdraw all funds from the pockets that you just related to the rip-off website.
- Doc every thing you’ll be able to, together with messages between you and the attainable scammer, your cryptocurrency pockets handle, and the area you have been instructed to connect with.
- Contact legislation enforcement. Even when your case isn’t massive sufficient by itself to warrant a federal case, contact the suitable legislation enforcement company on your locality and nation (). Your information could also be useful in creating a bigger case towards rings.
- Contact the Cybercrime Help Community. They will present assets to help you in reporting crime and coping with the aftermath.
A listing of probably the most not too long ago lively domains found to be related to these scams and different indicators of the rip-off operations researched right here could be discovered on our GitHub. Further domains shall be added as we course of them.
















